Cold Boot attacks: what are they, and how to defend yourself
Hackers have been exploiting system vulnerabilities for years, attempting to gain unauthorized access to sensitive data. One such method, known as Cold Boot Attacks, has been in use since the discovery of the first exploitable loophole in 2008. Although patches have been developed over the years to prevent such breaches, hackers have recently found a new vulnerability, putting most computer systems at risk.
What is a Cold Boot attack?
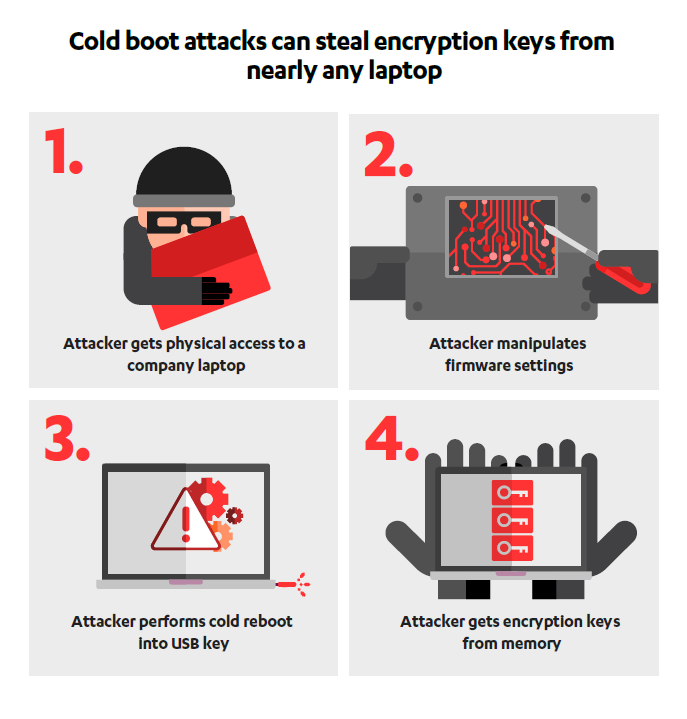
Often lurking in technology forums is a term that leaves many users puzzled – Cold Boot Attack. This term refers to a side-channel assault aiming to access your computer’s data illicitly. It exploits the fact that data persists in your computer’s RAM (Random Access Memory) even after being shut down. This data includes various files, data types, and, notably, encryption keys.
Following a cold reboot, a hacker can steal encryption keys due to the data remanence in SRAM and DRAM. This allows the data stored in memory to remain readable for some time after the reboot, providing a window of opportunity for a hacker with physical access to the computer.
Security measures were rapidly developed to protect against these types of attacks, but these patches have also been exploited, leading security researchers to discover a new vulnerability.
New versions of Cold Boot attacks
Although the Cold Boot Attack has been known since 2008, its potential danger was highlighted when F-Secure released a report stating that almost all computer systems are susceptible to these attacks. This includes advanced systems equipped with the latest processors.
Upon investigating, the team discovered a vulnerability that allows hackers to access even a locked or recently shut-down system. The attackers use a physical device to prevent data overwrite and enable booting from external devices. A common tool for this is a USB stick. Without USB access, the data in your computer’s RAM remains safe. After bypassing the memory overwrite feature, a hacker can access all the data stored in the computer’s memory, just like the older versions of the Cold Boot Attack. There’s no limit to what can be accessed – from encryption keys to passwords, account information, addresses, and corporate credentials – all are at risk. The report has led major computer manufacturers worldwide to acknowledge this vulnerability and work towards preventive solutions.
The implications of Cold Boot attacks
The F-Secure report suggests that these attacks are not easily preventable in the short run, making them a potent threat. The most effective immediate precaution suggested is avoiding sleep mode and shutting down the system completely instead. This is because encryption keys are stored in RAM during sleep mode but not when the computer is shut down or set to hibernate. Additionally, implementing a PIN system for every computer can also help keep hackers at bay.
Companies like Microsoft, Intel, and Apple have already started working on solutions to prevent these attacks. However, the confirmation of such attacks on advanced systems is indeed alarming. Knowing the nature of the threat, we can now explore various methods to protect your computer from Cold Boot Attacks.
Method 1: disabling the sleep function
Disabling the sleep function on your computer is a simple preventive measure. Here’s how to achieve this on a Windows system:
Disabling the sleep function on your computer is a straightforward preventive measure to reduce the risk of a Cold Boot Attack, especially on a Windows system. To achieve this, you start by clicking the Start Button, which is located in the lower-left corner of your screen. From there, click on the Settings icon that appears in the Start Menu. In the Windows Settings menu, select the “System” option. Then, navigate to the “Power & Sleep” option, which you can find in the Left Sidebar.
Finally, under the Sleep section, choose the “Never” option from the drop-down menus. By completing these steps, you can ensure that your system does not automatically fall into sleep mode, thereby safeguarding it against potential security risks like Cold Boot Attacks.
Method 2: leveraging hibernate mode
Hibernation is an excellent option for those who use their computers for extended periods. Instead of shutting down your system completely or putting it into sleep mode, you can use the hibernate option. This not only allows faster booting but also provides protection against Cold Boot Attacks.
To enable hibernation on a Windows system, begin by clicking the Start Menu located in the lower-left corner of your screen. Next, right-click on Command Prompt from the Start Menu and select “Command Prompt Admin.” In the Command Prompt window, you need to type the command powercfg.exe /hibernate On. After typing this command, press the Enter key to take effect. Once done, close the Command Prompt window by clicking the ‘X’ button.
To check if the Hibernate option is enabled, select the Start Menu and then choose the Shutdown or Sign Out option. You should see the Hibernate option on the Menu. Always choose Hibernate before leaving your computer system.
Method 3: implementing security solutions
Adding an extra layer of security to your system with Bitlocker PIN can also help protect against Cold Boot Attacks. This PIN differs from the Admin password, preventing the encryption key from automatically loading into the RAM.
To set up a Bitlocker PIN on your Windows system, you should first ensure Bitlocker is enabled. Begin by opening the Group Policy Settings; this can be done by pressing the Windows + R keys, typing in gpedit.msc, and pressing Enter. In the Local Group Policy Editor folder, navigate to the “Bitlocker Drive Encryption” option. Here, you need to click on “Require Additional Authentication at Startup.” In the next step, select the “Enabled” option and then go to the “Confirm TPM Startup PIN” option, choosing “Require Startup PIN with TPM.”
Following this, launch the Command Prompt and enter the command: manage-bde -protectors -add c: -TPMAndPIN. When prompted in the Command Prompt Window, enter your Bitlocker’s PIN. After you have entered the PIN, close the Command Prompt Window by pressing the X button. Remember, this security feature is only available for Windows Professional and Enterprise editions.
Rescuing lost data with Recoverit
If your computer has been a victim of a Cold Boot Attack, there’s a high chance of data loss. Fortunately, you can recover your lost data using a third-party tool like Wondershare Recoverit. To begin the recovery process, you first need to download and install Wondershare Recoverit on your system. Once installed, launch the tool and select the location where the lost or deleted file was stored.
Upon selection, the recovery process initiates automatically. You can keep track of the progress directly on your screen. After the scan, the tool will display the recoverable files. From here, select the files that you wish to recover and click on the “Recover” button. The final step involves choosing a suitable location on your system to restore the recovered data. Now, you’ve successfully completed the recovery process! Remember, in the realm of cybersecurity, prevention is always better than cure. Stay safe, stay protected!



