Essential cybersecurity tools for your PC in 2024
Essential cybersecurity tools: As we enter the second half of 2024, it becomes increasingly evident that security is a part of our lives. From viruses masquerading as the most innocent downloads to sophisticated phishing scams, the array of threats targeting
Why you should use incognito mode
Websites and companies, including giants like Google, track your activities through your browser; this is not news. But while altogether avoiding browsers isn't practical, using incognito mode is a powerful way to mitigate this tracking. This article delves into why
Internet scanning and the value of an ethical approach
Organizations often lack a comprehensive understanding of the external and internal risks to their networks. Securing their attack surface is the number one priority for organizations over the next 12 months. While Internet scanning has drastically shifted how security professionals
5 methods to locate accounts linked to your email
Did you know that the average person has over 100 online accounts? From social media profiles to subscription services, we've accumulated a vast digital footprint that can be challenging to manage. Therefore, keeping tabs on these accounts is crucial for
Cyber attack compromised Indonesia data centre, ransom sought
By Stanley Widianto and Ananda Teresia JAKARTA (Reuters) - A cyber attacker compromised Indonesia's national data centre, disrupting immigration checks at airports, and asked for an $8 million ransom, the country's communications minister told Reuters on Monday. The attack disrupted several government
How to set up your Passkey to your Microsoft Account
Again, Microsoft has a new feature for its users. The tech giant has introduced an innovative security feature called Passkey, which leverages cutting-edge passwordless authentication technology. By setting up your Passkey, you can bid farewell to the hassle of remembering
Top 5 free virus scanners to fortify your devices
Top 5 free virus scanners: As we entrust our personal and professional lives to the convenience of technology, the threat of malicious software, or malware, becomes larger. Viruses, worms, Trojans, and ransomware can wreak our devices, compromising sensitive data, hijacking
OTP Bots: what are they?
Have you heard of OTP Bots making the headlines lately? If not, keep reading. OTP bot, an abbreviation for "one-time password bot," is a malicious program meticulously crafted to circumvent the security measures provided by OTP authentication systems. These bots
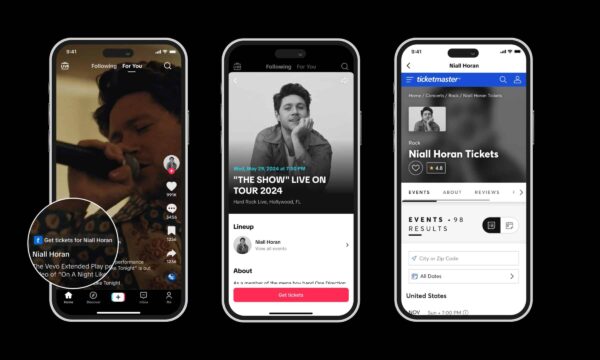
Live Nation admits Ticketmaster hacking
A big problem for the company and its customers A data breach in which the personal data of 560 million people was stolen. A huge reputational hit for Ticketmaster, a serious threat to the data owners that ended up in the