Social Engineering: Most of us have encountered numerous cyberattacks based on different methodologies and form types. And one thing that we are witnessing is that these cyberattacks are becoming more and more sophisticated on a technical aspect. Now attackers can bypass different forms of authorization and break down security walls without breaking a sweat because the methodologies used to perform these actions have evolved massively. In this ongoing war between attackers and security defenders, we can say that technology has developed quite a lot in both aspects. The attackers have come up with intuitive solutions to break down security walls. In contrast, defenders have developed innovative strategies to face hackers and malicious intentions.
But even with these advanced defense mechanisms that security engineers are implementing worldwide, one part of the ongoing chain continues to be weak and ready to be exploited. That part is human behavior. Unfortunately, the human factor is among the lowest chain links in the workflow process. Tricking a human and manipulating the behavior is proven to be a very efficient way on trying to perform malicious attacks. Nowadays, this type of exploitation is believed to be the number one cause of an enormous number of attacks worldwide. This form of manipulation of humans is known in the cybersecurity world by the term Social Engineering, and it’s one of the most dangerous attack methods that hackers use to penetrate illegally into different information systems.
What is Social Engineering?
Social engineering, unlike many other technical attacks, doesn’t try to break into computer systems directly. While a hacker might write a program that attempts to brute-force someone’s password or exploit a bug in the software, social engineering, as mentioned above, relies only on tricking or manipulating victims to do something that the attacker wants. Even with strong passwords, top-notch security software, and physically secured machines, a deceived person can be a vulnerability and still invite a security breach into a company or their own setup. Hackers have leveled up their skills in using this technique by regularly changing up their tactics to keep them viable. As a result, specific social engineering schemes adapt over time. The main methods used by fraudsters are:
- Creating a sense of urgency in a user by not letting the person take the time needed to think through an action, therefore pressuring them into taking actions they don’t want to do.
- Scaring the user to the point of blackmail and psychological abuse makes the person feel frightened and pressured to make a choice, most often indicated by the attacker.
- Impersonating a legitimate person or company. By doing this, the attacker tried to deceive the user into thinking they were legitimate to create a sense of trust between the attacker and the victim. Afterward, the attacker uses this to his/her/them advantage to trick the innocent user into undertaking some actions they didn’t want to do in the first place.
Most common types
By definition, social engineering takes many forms, including phishing, sweet-talking or lying, tailgating, threats and intimidation, and other tactics. According to the InfoSec Institute, the following five techniques are among the most commonly used social engineering attacks.
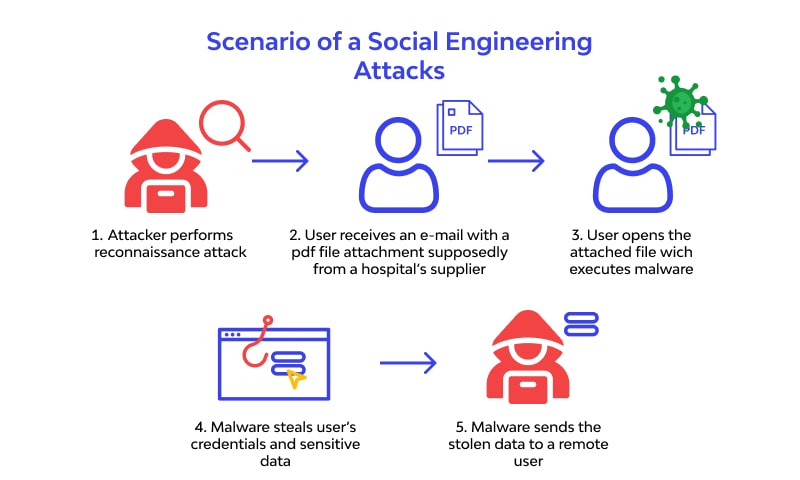
- Phishing: Phishing attack is one of the most common forms of social engineering, and it is widely spread due to their nature and the way of approach to the users. It has become a hazardous form of attack since it has advanced to be very realistic. This is an attack where someone pretends to be a legitimate entity, usually over email, and requests sensitive information. It often professes to be from PayPal, Apple, your bank, or another trusted company, asking you to “confirm” your details or review a suspicious transaction. If you want to learn more about phishing emails, take a look at our Phishing Attack Explanation Video
- Phone scams: are another form of social engineering, and we can say that these types of scams are more old-school than email phishing, but they’re still popular. In these schemes, someone calls you claiming, for example, to be from your credit card company and asking you to confirm your details because of suspicious activity.
- While it’s not as widespread as the above forms, baiting is a form of social engineering that preys on human curiosity. In these attacks, a fraudster leaves an infected CD or USB drive in a place where they hope someone will pick it up. If you insert the media into your PC, you could get hit by malware if the contents of the drive run automatically.
- Another form of social engineering is scareware, a mix between phishing and malware. In these attacks, you’re threatened using fake and alarming messages in the hopes that you’ll pay money to a scammer or give up sensitive information.
- Tailgating: is one exciting form of social engineering since it requires the attacker to be physically present to perform the attack. Tailgating refers to gaining access to a secured area by tricking another legitimate person into letting them in.
Protecting ourselves from Social Engineering
All these forms and much more are all part of the whole phenomenon of the social engineering method, which can result in some hazardous consequences. Therefore, we must watch out for manipulations of this sort to protect ourselves from danger. A few pieces of advice I can suggest are not to trust everyone or everything we receive because you might never know its real purpose. That is why we always have to double-check everything to confirm if the person we are talking to is legitimate or if the communication we receive is from a legitimate entity. And most. Importantly, it is to not give in to our emotions and take actions that we might later regret, for example, clicking right away on that suspicious link or opening that strange file. Recognizing these common scams and thinking critically when these situations arise can avoid playing into a fraudster’s hands.



