RaaS: In recent years, the ransomware threat has continued to grow. The most apparent trend is that ransomware groups are now targeting larger businesses and, in doing so, can demand larger payouts.
Another significant trend, however, is the rise of ransomware as a service (RaaS). Ransomware is no longer just an attack tool. It has also become a software product that can be rented to others.
So, what exactly is ransomware as a service? And how can businesses protect themselves from it?
Ransomware as a Service
Ransomware as a Service (Raas) is a type of ransomware attack that provides ordinary people with tools to conduct cyber-attacks. Like other ransomware, the perpetrator uses malware to access the victim’s network. Once they grant access to sensitive data – they demand a ransom. Raas works as a so-called affiliate software – meaning users can buy it on underground forums and use it to create ransomware attacks.
You don’t have to be a hacker to blackmail companies with Raas. People with little to no skills can buy an affiliate and target someone with a ransomware attack.
Important attacks from RaaS
As of 2021, the Colonial Pipeline attack, which caused widespread panic in the natural gas market, was carried out by an affiliate of DarkSide. The attack on JBS, which almost caused a meat shortage, was carried out by another RaaS organization, Revil. Revil was also responsible for the Kaseya VSA attack that temporarily shut down more than 800 Swedish grocery stores.
According to research by Trend Micro, the number of RaaS groups and extortionists increased by 63.2% in the first quarter of 2022 compared to the same period of the previous year. This increase inevitably led to more organizations falling victim to ransomware activity. According to the ransomware groups’ leak sites, which documented attacks on successfully compromised organizations that refused to pay the ransom, ransomware victims increased by 29.2% yearly.
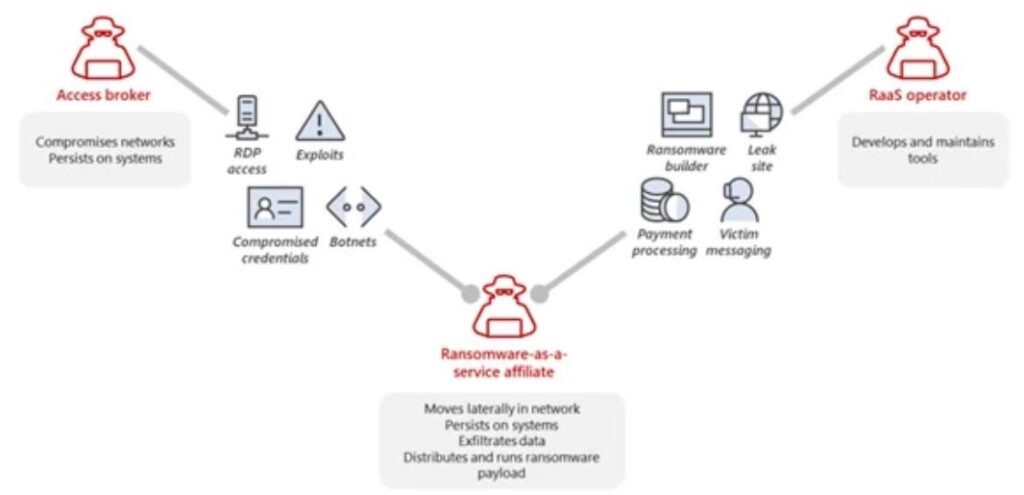
An example that explains a RaaS model
Converting ransomware malware to RaaS is a partnership – an agreement between an operator and an affiliate. The RaaS operator develops and maintains the tools to power ransomware operations, including the manufacturers that generate the ransomware payloads and the payment gateways for communicating with victims. The RaaS program may also include a leak site to share data snippets extracted from victims, allowing attackers to pretend the intrusion is real and attempt to extort payment. Many RaaS programs further integrate a range of extortion support offerings, including leak site hosting and integration into ransom notes, decryption trading services, payment pressure, and cryptocurrency trading services.
What happens is that the RaaS operator sells access to the ransom payload and the decryptor to an affiliate, which performs the intrusion and privilege escalation, and is responsible for developing the actual ransomware payload. The parties then shared the profits. In addition, developers and RaaS operators can also use the payload for profit, sell it, and run their campaigns with other ransomware payloads – further muddying the waters regarding tracking the criminals behind these actions.
How to secure from RaaS attacks
- Data backup
By backing up data, RaaS attackers won’t have the same leverage they would if they owned it exclusively. So don’t rely solely on cloud storage. Back up your data to external hard drives as a precaution against RaaS. Keep your software up to date
- All software should be kept up to date.
Software updates are often avoided for fear of breaking something. While this is always possible, the cost of a successful ransomware attack is significantly higher.
- Security Training
All staff should be provided with cybersecurity training. Ideally, employees should be able to identify malicious emails. However, specific email protocols should also be established, such as never clicking on links or downloading attachments.
- Divide all networks into segments
If an attacker gains access to a network, their ability to do damage depends mainly on where they can go.
Therefore, all networks should be separated, and each staff member should only have the level of access required to do their job. The most important data should be kept separate from everything else.
- Use Antivirus Suites
Sophisticated hackers are usually able to hide from such software. However, many ransomware attacks rely on software that a reliable antivirus suite will flag and block from running.



