Security Information and Event Management (SIEM) systems have emerged as a crucial tool for organizations aiming to bolster their security posture. By providing real-time analysis of security alerts and aiding in the detection of anomalies, SIEM systems can significantly enhance your organization’s ability to respond to threats. SIEM systems are designed to aggregate and analyze data from various sources within your IT infrastructure. This data includes logs from servers, applications, network devices, and security appliances. The primary function of SIEM is to identify and alert to potential security incidents, helping security teams to respond and mitigate risks quickly. However, to truly optimize your security using SIEM, it’s essential to go beyond mere data aggregation and alerting. Understanding the core functionality of SIEM systems is the first step towards maximizing their potential.
Success factors in the Data Collection Phase
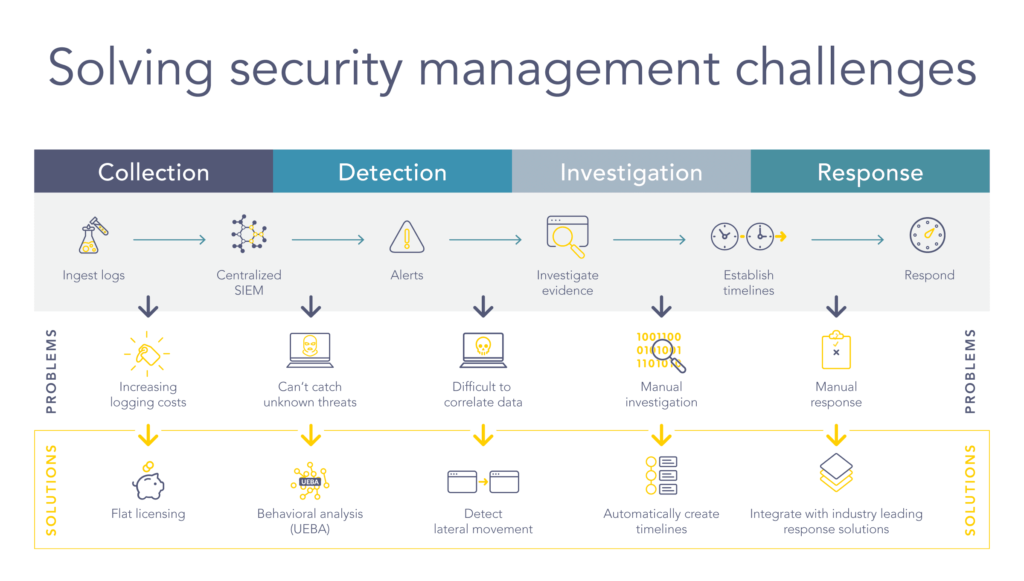
A SIEM system is only as good or efficient based on the nature and volume of data it captures. Begin by making sure all the data sources that matter are integrated with your SIEM. This range from the classical log-generating systems to new and state-of-the-art technology offering cloud services, IoTs. Collecting complete data empowers the SIEM to give you a more detailed view of your security environment, allowing for better detection and response capabilities. The most elaborate SIEM systems are helpless when data is unavailable in the face of critical threats.
Combine multiple data sources into your SIEM. To improve their ability to correlate events and detect more complex attack patterns, businesses should also leverage different types of security log information. These logs will prove very useful in detecting threats if your SIEM system can readily digest them, along with the traditional Windows and Unix-type files. This thorough data collection methodology will significantly reduce security monitoring blind spots to offer a comprehensive snapshot of an organization’s actual information and regulatory compliance posture.
Combining events for better detection
A SIEM system offers an ability to correlate events from multiple data sources in a single location which is the main power of this tool. It takes unrelated events and connects them, revealing intricate attack patterns that otherwise would likely go unseen had they only been looked at one by one. An example would be a failed attempt to log into a server. But, if these were coupled with other failed login attempts on the same server within a short period, they may be part of an organized brute-force attack. We can more easily discover yet invisible threats with correlation capabilities.
Successful event correlation means more than just consolidating data; it requires understanding which events from different sources might represent a security incident together. You can accomplish this by configuring correlation rules and various other algorithms so that the patterns retain simplicity (throughout for network detection) rather than overly complex ones. This improves threat detection and cuts down the number of false positives so your security team can focus on legitimate threats.
Using AI and Machine Learning in SIEM
This includes monitoring and analysing a range of digital systems, such as personal computers, websites, mobile apps, etc., for the purpose through machine learning (ML), which uses AI to automatically detect or defend against unwelcome digital intrusion. The latter are able to analyse large volumes of data streams for changes in typical patterns and even early indicators of potential security incidents. Machine learning models can improve using historical data, and as they learn over time, they provide better, more timely alerts. You can enhance its threat detection capabilities by bringing machine learning and AI to your SIEM mix.
Machine learning and AI can even automate much of the more mundane side of threat detection, meaning your security team is free to attend only meaningful activities. This can include automatically classifying alerts and ranking them in order of significance (using Machine Learning algorithms so your security analysts spend their time only on serious threats. Through the use of these types of advanced technologies, you can be sure your SIEM system will keep up with a fast-evolving threat landscape.
Focusing alerts to work against the response
This makes SIEM systems produce many alerts, possibly false-positive ones. In order to prevent alert fatigue and promptly address real threats, you must prioritise your priorities based on their severity level and the impact they can have. Adopting a strong alert prioritisation does not bind your security team to the most meaningful incidents and ensures that limited resources are engaged efficiently. This should be done by setting thresholds on alert severity and using automated tools to bucket into buckets accordingly.
Prioritising alerts means prioritising adjusting your SIEM rules and configurations to minimise false positives. One of the most important ways to stay ahead is to be (among other things) constantly revisiting and improving your alert logic as industry understanding grows about new threats. Alerts should always be prioritised, enabling your security to prioritise and best respond swiftly and efficiently to the most severe threats before they can cause widespread damage to you.
SIEM with response and remediation automation
Some ways this can be achieved include SIEM integration with Security Orchestration, Automation & Response (SOAR). SOAR automatically responds in some cases, helping the organizations keep alert handling times at a minimum. Suppose an SIEM notices an irregular log-in frequency, which might suggest an instance of breach. In that case, using the SOAR tool, one can perform the required activities automatically, e.g., Quarantining the system or blocking IP address, etc. This one will automatically respond to the first of its kind, reducing potential security incidents and increasing efficiency overall.
Rather than your security team spending time on basic incident response activities, automation helps funnel more and better human resources to work on larger issues. Automate Common Security Scenarios. Suppose you automate the workflows that normally require a SOC analyst to examine and decide on standard user behaviour. In that case, it will help minimize outage times for all alarms coming through your SIEM and better focus time with security experts. Not only will this enhance your security operations, but it also makes you less prone to human error.
Continuous monitoring and improvement
The cybersecurity landscape is constantly evolving, with new threats emerging regularly. So, to ensure that your SIEM system remains effective, it’s essential to monitor and improve continuously. Periodically review and update your SIEM rules and configurations to adapt to new threats and changing IT environments. Conduct periodic audits and assessments to identify any gaps in your SIEM coverage and address them promptly because continuous improvement ensures that your SIEM system remains a robust and reliable component of your security strategy.
However, optimizing security with SIEM is not just about technology; it also involves people and processes. Foster a culture of collaboration within your security team to ensure that SIEM alerts are investigated and addressed promptly. Encourage regular communication and knowledge sharing among team members to improve their understanding of SIEM capabilities and threat detection techniques. Enhancing team collaboration can ensure a more cohesive and effective response to security incidents, providing maximum benefit to your organization.