Gold Pickaxe: As you all might already know it, our faces have become the new currency, granting us access to a vast array of conveniences and services. From unlocking our smartphones to authorizing financial transactions, facial recognition technology has become deeply embedded in our daily lives. However, this newfound reliance on our facial data also makes us vulnerable to a growing threat: scammers who are exploiting this technology for malicious purposes.
The rise of the “Gold Pickaxe” malware
One such malicious actor is the “Gold Pickaxe” malware, a smartphone-targeting threat making waves in the cybersecurity landscape. According to Bleeping Computer, the security company Group-IB initially identified the malicious mobile app. It is part of a broader, ongoing malware operation referred to as Gold Factory. Typically masquerading as a genuine application, Gold Pickaxe deceives users into installing it and is classified as either an iOS or Android Trojan.
By disguising itself as a legitimate government-backed application, the Gold Pickaxe lures users into granting it access to their devices, where it can then capture facial images and transmit them back to the scammers. The Gold Pickaxe’s malware often masquerades as a digital pension management app or other government-affiliated software, sending out social engineering emails that impersonate official authorities and urge users to download the infected application. Once installed, the malware springs into action, scouring the device for valuable data, including text messages, web traffic, and even stored files.
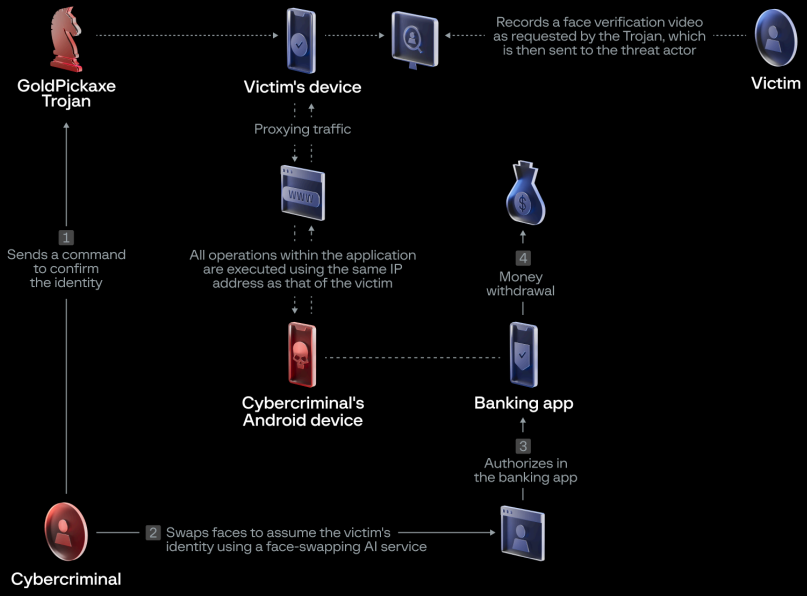
But the Gold Pickaxe’s true focus is on obtaining its victims’ facial data. It employs two distinct methods to achieve this goal. The first is a direct approach, where the malware prompts the user to scan their face through the device’s camera, ostensibly for authentication purposes. The second, more covert tactic involves the malware intermittently taking snapshots through the front-facing camera, hoping to capture the user’s face in the process. If that fails, it will scour the device’s photo gallery for any images containing the victim’s likeness.
The sinister uses of stolen facial data
One of the primary ways they can leverage this information is to bypass biometric security measures, such as those used by banks to verify large financial transactions. By presenting the stolen facial data, the scammers can circumvent these safeguards and gain unauthorized access to the victim’s accounts.
But the threat doesn’t end there. Scammers can also use the harvested facial data to create highly convincing deepfakes – synthetic media that seamlessly superimposes a person’s likeness onto another body, allowing the scammer to make the victim “say” or “do” anything they desire. These deepfakes can then be used to create a wide range of scams, from impersonating the victim in online interactions to committing identity theft by creating official documents under the victim’s name. Unlike other personal information, such as passwords or credit card numbers, our faces are constantly on display, vulnerable to capture by cameras in our surroundings. This lack of control over our facial data makes it an attractive target for scammers, who can exploit it without the victim’s knowledge or consent.


Combating the threat: strategies for facial data protection
Fortunately, there are steps that individuals can take to mitigate the risks posed by facial recognition scams. One of the most crucial measures is to be vigilant about app permissions, particularly those that request access to a device’s camera or photo gallery. If an application that doesn’t seem to require facial data asks for such permissions, it should be treated with caution.
Additionally, users can bolster their defenses by enabling two-factor authentication (2FA) on their sensitive online accounts. This extra layer of security can help prevent unauthorized access, even if the scammers have obtained the victim’s facial data. Furthermore, the installation of reliable antivirus software can help detect and block the installation of malicious apps like the Gold Pickaxe.
Beyond technological safeguards, individuals can also take proactive steps to limit the exposure of their facial data. This may involve carefully curating one’s online presence and minimizing the number of publicly available images that contain one’s likeness. Additionally, being mindful of one’s physical surroundings and the potential for hidden cameras can help reduce the risk of inadvertent facial data capture.
The future of facial recognition and cybersecurity
As facial recognition technology continues to evolve and become more prevalent in our daily lives, the battle against scammers who seek to exploit this data will only intensify. Governments, financial institutions, and technology companies must work collaboratively to develop robust security measures that can effectively safeguard individuals’ facial data while empowering users with the knowledge and tools to protect themselves.
Some promising developments in this regard include Apple’s Face ID technology, which employs advanced depth mapping and infrared imaging to create a highly secure facial authentication system. Additionally, some banks and financial service providers are leveraging third-party facial identification services, incorporating additional verification measures to ensure the authenticity of the user’s identity.
Ultimately, the responsibility to safeguard one’s facial data lies with the institutions and technology providers and the individual. By staying informed, exercising caution, and proactively implementing security measures, users can significantly reduce the risk of falling victim to facial recognition-based scams.



