StrikeReady : A powerful platform with a virtual cyber assistant
StrikeReady: Everyone knows how important cyber security is in every work process of the companies operating in today’s market. But how interesting would it be to have a cyber assistant there for every need or request that you may have regarding a security issue? More or less a friend that could help you with every question and offer you a thorough analysis of every security concern.
A few people thought of this innovative approach. They came up with StrikeReady, a company that has developed an advanced technology solution offering real-time personalized and proactive assessment and remediation of future and current risks. It goes by the name Cara.
CARA Intelligent System
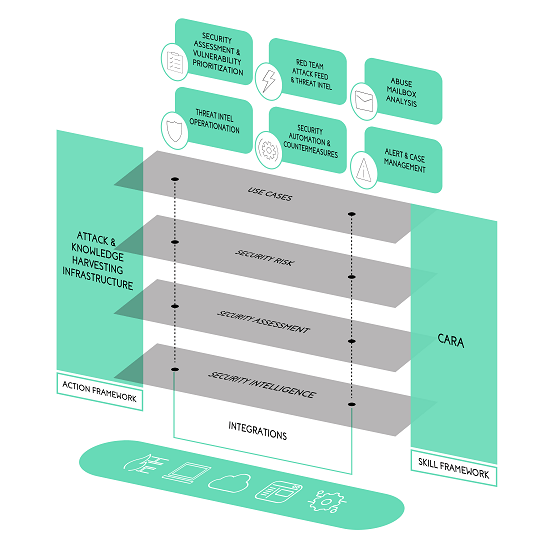
CARA is an Intelligent System that gathers information on the institutional knowledge and practical experiences of defenders worldwide and processes it in real time. It is the first digital cybersecurity analyst and assistant that can help the team analyze, guide, and resolve different issues.
CARA was designed to assist and empower cybersecurity teams that are overburdened by an endless tally of incidents, alerts, and an ever-changing threat landscape. Cara can be a part of any team like Incident response, SOC, Threat Intelligence, SO and security engineering team, etc.
We were curious about this new and innovative approach and the solutions offered by the StrikeReady platform, so we met with Strike Ready’s Chief Product Officer & Marketing Executive – Anurag Gurtu, for an exclusive interview with 4imag.
How was StrikeReady born?
“We started the company three years ago. The founder, Yasir Khalid, had been with FireEye for almost ten years. He was there from 2008 and onwards. I joined FireEye about a year before they went public to build their (StrikeReady) technical marketing product. And then, most of our engineers were focused on research or threat research. They were also part of the engineering team and the QA team product. I was also focused on products and marketing, so when we were starting StrikeReady, we also did 0 detections for quite a few years.
When starting StrikeReady, we thought we should focus on the subsequent Gen detection and response platform. But as far as we knew, they’re already over 1000 companies doing the same thing, so we said, let’s focus on something different, innovative. So, what can we do and leverage our expertise in the next company?
Machine Learning
Over the course of years, I moved into other aspects of security, so I was heavily leveraging machine learning. I moved into NLP and AI, so with that background, we started thinking about what would be the next wave of technology where we can leverage intelligence and blend it with artificial intelligence and technology sectors like cyber security. Therefore, we looked at the market and noticed that there’s still a skill talent shortage in cyber. We started looking at technologies, emerging security automation, and companies claiming to solve the skill talent problem. Still, the challenge is that you need highly skilled people to write these playbooks. We know that there is a skill gap problem that exists in organizations.

We started looking at the next-generation workforce, and it was pretty evident that old-timers like us would retire. The new-age millennial workforce will come into the industry. We looked at the behavior profile of this new-age workforce, and it was evident that they are used to text and voice interaction.
On the other hand, we know millennials reinforce a skill talent problem because very few educational institutes will do a master’s or bachelors in cyber. Even if they do, it’s a very theoretical thing. It’s not like you give them an alert, and they’ll know what to do or thread Intel feeds. I think it’s very clear that this generation of the workforce will need technology like ours, and we said, if the national force is so used to text and voice, what should be the interface that should be made available? That is where we decided that the interface has to be a virtual assistant, easy to embrace like Cara. We decided to create a female embodiment since this sector is still dominated by males, statistically speaking. Also, the name means friend in Irish and stands for cyber awareness and response analysis. That’s how StrikeReady was born.”
Which are the main components of the StrikeReady platform?
“When we decided to build this platform, we focused on creating a cognitive security platform. And that platform was designed with three purposes in mind: the first was to help maximize the utilization of existing layered defense technology, so a lot of organizations, depending on their maturity curve, will have different types of debts that they would have deployed. For example, a lower maturity code organization may only have a firewall.
Meanwhile, a little higher maturity code organization may have a firewall in a proxy. But depending on the maturity code, if you are lower on the mature security code, that doesn’t mean you should not be protected. So, we want to maximize the utilization of the tech stack you have using our cognitive security plan. And a company might not have a workforce that can be fully skilled, so they will not understand how to maximize the utilization of the tech stack they have deployed. That’s why you need a technology that can help you with that. That’s the goal. The core philosophy is empowering the defenders.
The second aspect was maximizing the utilization of the tech stack. If you want to maximize the ROI of the tech stack that you have deployed, how about using this technology that improves your security maturity?
Maximization
We maximize what you have, but let’s say you don’t have an attack simulation capability, a threat Intel capability, an alert management capability, a case management capability, a security automation response capability, risk-based, quality management, and so on. There are a lot of different tech stacks, and if you don’t have the same platform, we’ll expose those capabilities. You don’t have to buy products from other companies. The same platform can expose those features or capabilities if you need them, and we don’t charge anything extra for that.
And the third aspect was: After improving the security maturity of an organization, it can reduce the operating cost of the organization. And how we are reducing your costs by offering your next Gen security category, which is fully integrated with many other security aspects.”
How does Cara work?
“Cara assistant can offer her help to any cyber security defender, in any team. Cara has gathered a lot of information and many cyber security engineers can leverage their skills through Cara. At the same time, she can leverage the tech stack that you have to maximize the utilization. And if you did not have a specific tech stack, she can expose capabilities and features at the same time for you to leverage, all based in AI technology. You can start delegating tasks to her or you even delegate functions and let her run in an autonomous way. Every week we are training Cara with new products in different categories. We would train Cara in firewalls and then within those specific vendors we train Cara to get a broader knowledge about dissection, attack simulation when testing firewalls, proxies of gateways, etc.”
How do you implement this platform in the company’s work processes?
“Our platform was fully functional since Day One, and I know that many AI-based systems cannot perform since day one because they have to learn their environment. But we have been training Cara with the skills of different defenders over the course of years. We are a SaaS-based platform, and the use of it is pretty simple. You create your account, log in, and then we request you provide your first name, last name, and e-mail address. And then, within a few minutes, you can receive an automated e-mail that your account has been provisioned, reset your password, and log into the platform. That’s how you connect to the platform.
Meanwhile, Cara is already trained with hundreds and hundreds of skills in different personas, so she is fully operational. And you can start conversing with her, and she’ll respond. She doesn’t know what’s in your environment, so the next thing is for you to connect to the tech stack of organization of technologies that you have, so it’s very straightforward. We have oversimplified it, and we need credentials to access the technology. Also, Cara keeps a tab on the tech stack to see if there are any increments, and if they’re new capabilities that these tech stacks expose, she knows how we leverage it, and she starts leveraging with instantaneously. It’s fairly straightforward for an organization to get onboarded onto the platform in less than a day and start reaping the benefits.”
How does the platform minimize ‘false positives’ generated?
“We call this phenomenon the alert overload, which consists of both true positives and a lot of false positives. In most organizations that we have deployed the product, we see about 60 to 70% FPS, so excessive false positives. Because of our Intel background, we knew we would run into this problem. How you deal with false positives is as when you are dealing with any artifact or IOCs, you basically will go on different reputation engines and start analyzing.
The knowledge of the reputation engine is very subjective. It depends on the analyst. We observed analysts, and we said they are like 5055 analysis engines that these actors go to, basically, the whole knowledge that nobody shares. And then, it basically extracts all the artifacts from the vulnerability, runs it through all analysis engines, and then rescores it. It figures out whether it is a true positive or a false positive.
Observation
It also observes your organization and what your analysts have done in the past.
Some will say it’s non-malicious, but that’s where the algorithms come in to really analyze if it’s a true positive or false positive, and then if it’s a true positive, it automatically. And then, very structured documentation happens where you can click on it, and we’ll show you the analysis of what the system did across all the engines it looked at and then score itself. This is where the intelligence of the best defenders is instantly made available to a junior analyst or even a seasoned analyst who maybe doesn’t have time to write a signature or is so overloaded that they cannot think in real time about what they should do. Perhaps they’re under pressure, breached, or compromised and want to solve the problem instantly. Now the knowledge of the best defenders is available in real-time.”
What was the business approach to this type of solution?
Our platform is a disruptive product, and we typically joke and say it’s just like how Tesla in 2004 came out and said we would build electric park cars that would drive on their own. And people laughed at it. We are in the same stage. There’s always a challenge where people don’t believe it can be done, and they get impressed during the demo. We say if you don’t see value in one week, you will never see value in a product. But there’s not a situation where they haven’t seen a value. So, it’s fairly easy for us to demonstrate AI’s value and power within our platform.”
Is Cyber AI the future of cyber defense?
“Yes, I think AI will be a crucial part of the future of cyber defense strategies. But I also think it will be the future of following-stage technologies, not just for cyber, but for pretty much everything. We already have seen a massive adoption of AI-based technologies, which consumer tech embraces heavily.
I mean, the general population is using AI all the time, which is why I think Ai and Cyber will be the next wave of a technology revolution that will come in place. AI will be the next significant aspect of cyber, and you would need to have defenders also empowered with AI fight different cyber battles.”



