Ransomware in healthcare: An old enemy that is still very difficult to contain. This is the story of ransomware and companies, which, despite the years, continue to be hit by ransomware attacks to get their data back. Suppose large companies find it easier to invest substantial budgets in organising their cybersecurity team to minimise the risk of attack and limit the damage so that they can react quickly to the eventual offensive. In that case, the scenario changes for small and medium-sized companies.
These are the most numerous and the most vulnerable precisely because, in some cases, they misdirect their strategy, preferring to use the money to increase business, or, in other cases, they lack the necessary funds to rely on countermeasures that are as effective as required to counter cyber criminals’ moves.
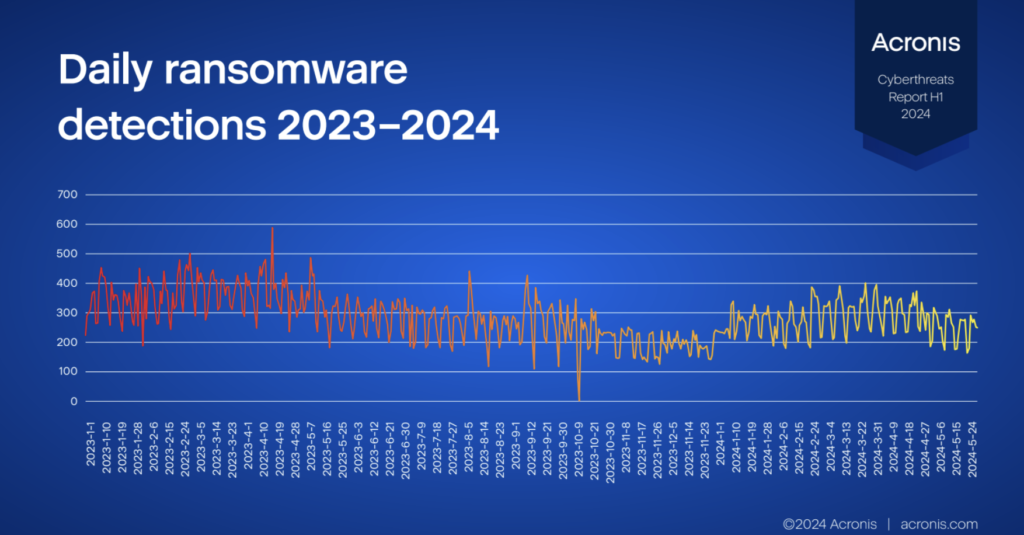
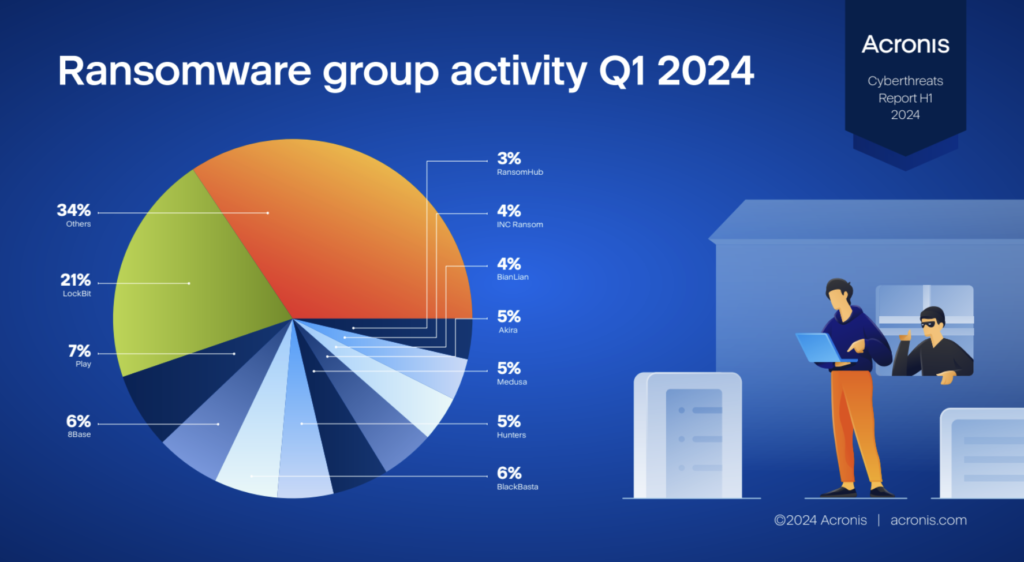
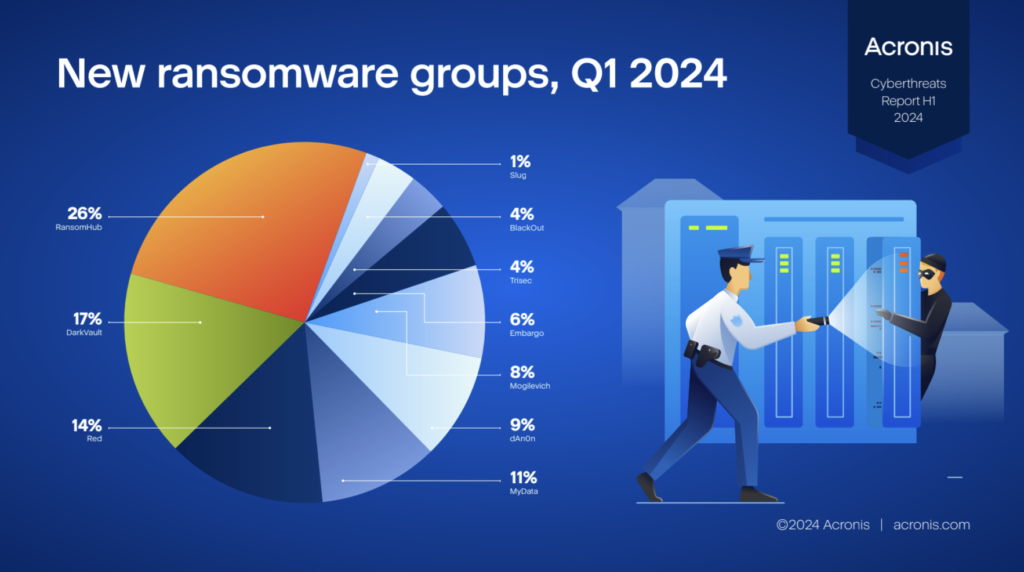
For some years now, ransomware has been the preferred technique of hackers, who can orchestrate an attack with a high success rate in a short time. According to a recent report by Acronis, there was a 32% increase in detected ransomware attacks between the last quarter of 2023 and the first three months of 2024. The Swiss company with global headquarters in Singapore recorded ten new ransomware groups that claimed 84 cyber attacks worldwide.
This group has three central corporate nightmares: PLAY, Black Basta, and the ubiquitous LockBit. One of the most interesting (and worrying) aspects highlighted by the researchers is that cybercriminals’ favourite targets are the government and healthcare companies. These are two critical sectors for society because they compromise key areas rich in personal data, which is the best to resell on the dark web.
The surge in attacks on health facilities
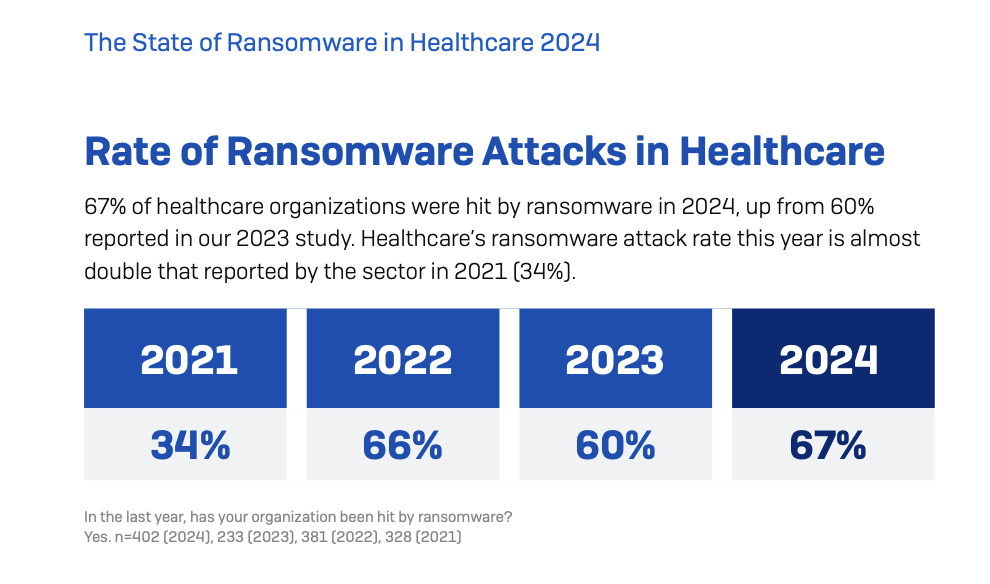
More in-depth studies on the individual sector have shown that the health sector is under assault by cybercriminals. Highlighting the growth in attacks, which this year reached the highest frequency in the last three years, is ‘The State of Ransomware in Healthcare 2024‘, the Sophos report, according to which more than two-thirds of the 402 organisations surveyed (67%) have suffered attacks this year. This figure is also alarming because it is up from last year (60%) and is in contrast to ransomware offensives across the board, which for Sophos have fallen from 66% in 2023 to 59% this year.
The effectiveness of a ransomware attack is measured not only by the ransom paid, if any, but also by the time it takes the company to react and get out of the recovery phase and back to operational standard. This is something to consider, as only 22% of the affected companies restored their operations within a week. If almost eight out of ten companies fail to do so, there is a major problem at the cybersecurity level: a gap that needs to be filled quickly and correctly.
What is most striking, moreover, is the backward step recorded in this regard by Sophos because, in 2022, 54% of the sample surveyed for the report had managed to stem the offensive within seven days, while in 2023, the figure was 47%. This year, on the other hand, there is a debacle, also due to the increased effectiveness and complexity of the attacks suffered, as almost 4 out of 10 companies needed a month to recover (in 2023, 28% of companies required 30 days to return to full strength).

Increased costs to get back into operation
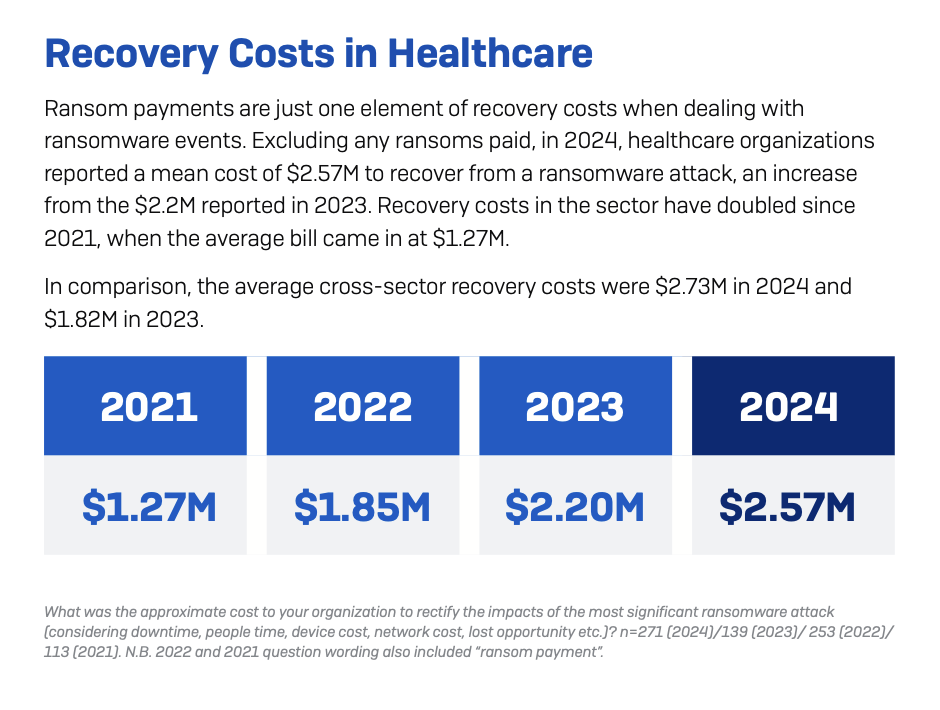
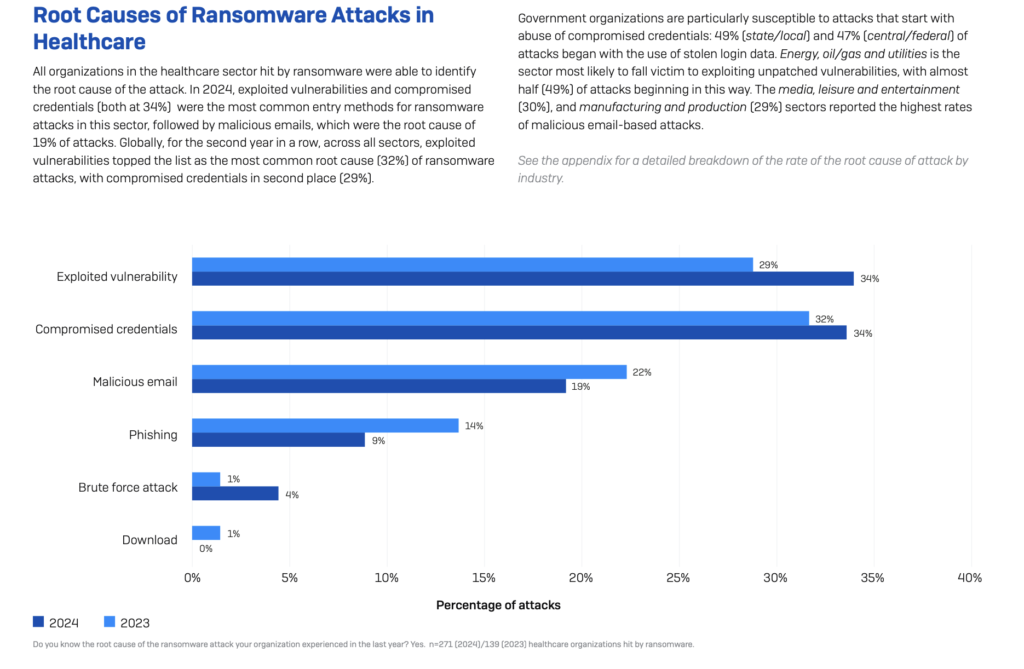
Worsening the situation is the rising cost of business recovery, as the average cost for healthcare organisations in 2024 was $2.57 million, up from $2.2 million the year before. The industry snapshot also shows that 57% of healthcare providers paid the ransom by paying more than the initial demand. As for the causes of attacks, compromised credentials and vulnerabilities are the two weak points (34%) cybercriminals exploit. Another relevant point is the increasing interest of attackers in backup, with 95% of healthcare facilities affected by ransomware having faced a backup breach attempt, resulting in more than double the likelihood of paying to regain possession of the encrypted data (63% vs. 27%).
‘Although the frequency of ransomware attacks has reached a sort of homeostasis or even decreased across the board, attacks against the healthcare sector continue to intensify in both number and scope. The particularly sensitive nature of the data handled in healthcare and the need to have it accessible at all times will be an irresistible lure for cyber criminals, who have realised that very few healthcare workers are prepared to respond to such attacks, as evidenced by the extended recovery times,’ said John Shier, Field CTO Threat Intelligence at Sophos.
The expert also suggested a solution to remedy the problem: ‘These attacks can have an immense ripple effect, affecting the healthcare sector and the care provided to patients. To combat such determined adversaries, healthcare must adopt a more proactive, expert-led approach to threat detection and response that combines advanced technology and continuous monitoring to stay one step ahead of the attackers.’



