With the increasing adoption of cloud computing, the complexity of managing and securing these environments has grown significantly. Hybrid cloud security has become a crucial aspect of modern IT strategy, aiming to protect data and applications across a mix of public and private cloud environments. This integration of different cloud services provides flexibility and scalability but also introduces unique security challenges that require specialised approaches.
Understanding Hybrid Cloud environments
A hybrid cloud environment combines public and private clouds, allowing data and applications to be shared seamlessly between them. This setup offers numerous benefits, such as cost-efficiency and optimising IT resources according to specific needs. By keeping sensitive data on private clouds while utilising the computational power of public clouds for less critical operations, businesses can meet compliance requirements and enjoy the advantages of public cloud services.
However, hybrid clouds’ diverse components and dynamic nature pose significant security challenges. Managing security across such a varied infrastructure demands a nuanced approach, as traditional security measures designed for static, on-premises environments often fall short. Here are some key challenges that we can encounter in hybrid cloud security.
Skill gaps and knowledge deficiencies
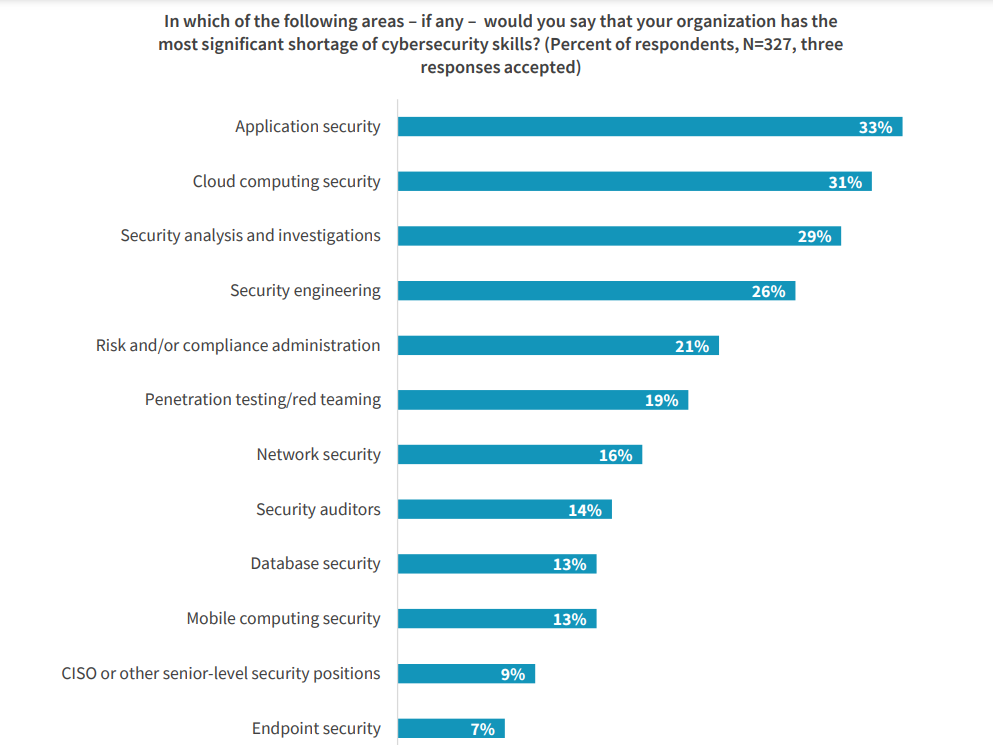
One of the primary challenges in hybrid cloud security is the skill gap among IT and cybersecurity professionals. The rapid pace of cloud adoption has outstripped the development of corresponding security skills, leaving many professionals unprepared to address the complexities of cloud security. According to ESG research, 46% of IT and cybersecurity professionals report a “problematic shortage” of cybersecurity skills, particularly cloud security. Bridging this gap is essential for effective hybrid cloud security.
This skills shortage leads to a significant knowledge gap that can hinder the implementation of robust security measures. IT teams may struggle to understand the unique security requirements of hybrid cloud environments, resulting in vulnerabilities that cyber threats can exploit. Organisations are at a higher risk of security breaches without adequate training and expertise.
Organisations must invest in comprehensive training and development programs to address these deficiencies. Enhancing the skills and knowledge of IT and cybersecurity professionals is critical to ensuring they can effectively manage and secure hybrid cloud environments.
Inconsistent security policies and controls
Another significant challenge is maintaining consistent security policies and controls across public and private clouds. Traditional security controls are often inadequate for the dynamic and distributed nature of cloud infrastructure. Ensuring that security policies are uniformly applied requires continuous monitoring and adjustment, a task made more difficult by the diverse components of hybrid cloud environments.
The inconsistency in security policies can create gaps that cyber attackers can exploit. A cohesive security strategy that spans all cloud environments is crucial for protecting data and applications. Developing such a strategy involves implementing policies that can adapt to the changing nature of cloud environments.
Organisations must also consider the need for integrated security management solutions. These solutions can provide a centralised platform for managing security policies and controls and monitoring across all cloud environments, ensuring consistent application and enforcement of security measures.
Visibility and monitoring difficulties
Visibility and monitoring across hybrid cloud environments are inherently complex. Traditional network monitoring tools may not effectively capture traffic between cloud-based workloads, leading to blind spots in security coverage. This lack of visibility can prevent security teams from promptly identifying and responding to potential threats.
Advanced monitoring tools are necessary to provide end-to-end visibility and detect real-time anomalies. Comprehensive visibility ensures that security teams can monitor all activities within the hybrid cloud environment, enabling them to respond quickly to security incidents. This capability is crucial for maintaining the security of hybrid cloud environments.
Implementing advanced monitoring solutions that integrate with threat intelligence feeds can help identify suspicious activities and indicators of compromise. These tools enhance the ability of security teams to manage risks and protect critical assets in the cloud.
Compliance and regulatory issues
Navigating compliance and regulatory requirements across different cloud providers is challenging. Each provider has its own compliance standards, making it difficult to ensure uniform compliance in a hybrid environment. Organizations must thoroughly understand these requirements and implement appropriate controls to meet them.
Regular audits and assessments are essential to identify compliance gaps and ensure regulation adherence. Failing to comply with regulatory standards can result in legal issues and damage to an organization’s reputation. Maintaining compliance requires a proactive approach and the use of compliance management tools that facilitate adherence to regulatory standards.
Organizations should establish a comprehensive compliance strategy with continuous monitoring and regular reviews. This strategy helps ensure that all aspects of the hybrid cloud environment meet regulatory requirements, thereby reducing the risk of non-compliance.
Best practices for securing Hybrid Cloud environments
Implementing unified security management is essential for managing security policies and controls and monitoring across all cloud environments. Solutions like Check Point’s vSEC provide a centralized platform that supports various cloud and software-defined data centre (SDDC) infrastructures, enabling consistent security practices. A centralized approach allows security teams to apply uniform policies across both public and private clouds, reducing the risk of security gaps and enhancing overall protection.
Investing in training and development programs is crucial to upskill IT and security teams in cloud security. Collaboration between DevOps and security teams can bridge the knowledge gap, ensuring that security considerations are integrated into development and deployment processes. This collaboration fosters a security-first culture within the organization, which is vital for effective hybrid cloud security. Enhancing skills and knowledge prepares teams to handle the unique challenges of hybrid cloud environments and maintain a robust security posture.
Advanced security controls, visibility, and compliance
Adopting advanced security controls tailored for cloud environments is vital. Micro-segmentation reduces the attack surface by creating virtual network segments for specific communications, while service chaining applies security services like intrusion prevention systems (IPS) and antivirus to particular workloads. These controls provide granular protection and align security measures with the specific needs of hybrid cloud environments, addressing unique vulnerabilities and risks.
Deploying monitoring and analytics tools that provide visibility across physical, virtual, and cloud environments is critical. Tools integrating with threat intelligence feeds help identify suspicious activities and indicators of compromise, enabling proactive threat management. Comprehensive visibility ensures that security teams can monitor all activities and respond promptly to potential threats, reducing the risk of significant breaches.
Leveraging automation and orchestration tools to streamline security provisioning and management enhances security posture. Automation ensures consistent application of security policies as new workloads are deployed, reducing human error and improving efficiency. Automated processes help maintain compliance and mitigate risks effectively. Regular audits and compliance checks ensure adherence to regulations and help avoid legal issues. Establishing a comprehensive compliance strategy with continuous monitoring and regular reviews is essential for maintaining a secure hybrid cloud environment.



