Unmasking invisible threats: Diving into the rise of encryption and fileless malware
Cybersecurity has taken centre stage in protecting us from digital harm in today’s hyper-connected world. This article invites you to explore encryption and fileless malware – two sinister foes that have emerged as significant threats to our online safety. They pose a significant risk to organizations and individuals alike, as they can easily evade traditional security measures and cause significant damage to systems and networks. According to a report by WatchGuard, fileless malware attacks increased by 888% from 2019 to 2020, with the number always rising in the coming years. As these nearly undetectable threats continue to evolve, we must stay informed and vigilant in our efforts to defend against them.
Understanding fileless malware and its impact
Fileless malware, as its name suggests, is a type of malicious software that operates without the use of traditional executable files on a target system. Instead, it leverages legitimate system tools and processes to carry out its malicious activities, such as blending in with normal background operations and evading conventional detection methods. By exploiting known vulnerabilities in applications and operating systems, fileless malware can infiltrate networks, compromise sensitive data, and destroy affected systems with minimal trace.
The rise in the use of file-less malware is proof of the adaptability of cyber criminals, who continue to devise new tactics to bypass traditional security measures. This type of malware is especially concerning because it can avoid detection by most antivirus, which often relies on identifying malicious files and signatures. As a result, fileless malware attacks can go undetected for extended periods, providing an opportunity for threat actors to establish a foothold in target systems and gather valuable data. Successful attacks can result in the theft of sensitive information, financial losses, and damage to a company’s reputation.
Additionally, the nature of fileless malware can make it difficult for security teams to determine the full extent of an attack and properly remediate affected systems. In some cases, organizations may have to expend resources to recover from an incident, further underscoring the need for improved detection and prevention mechanisms.
Common types of fileless malware attacks
Several types of fileless malware attacks target various aspects of a system. These include:
Memory-based attacks leverage system memory to execute malicious code, using tools like PowerShell or JavaScript engines to initiate the attack. By operating exclusively in memory, these attacks evade traditional file-based detection methods, leaving little to no trace on the infected system.
Living off-the-land attacks (LOLbins): This type of attack involves using legitimate, pre-installed system tools to carry out malicious activities. These tools, such as PowerShell, Windows Management Instrumentation (WMI), or the Microsoft Office suite, are commonly used by administrators for legitimate purposes, making it difficult for security solutions to discern between normal and malicious activities.
Registry-based attacks: In these attacks, malware is injected directly into the Windows Registry, a database that stores configuration settings and options for the operating system. Once embedded within the Registry, the malicious code can be executed without ever writing a file to disk, making detection and removal more challenging.
Document-based attacks leverage malicious macros or scripts embedded within seemingly innocuous documents (e.g., Word, Excel, or PDF files) to execute code once the document is opened. Using a trusted file format, attackers can bypass security measures to block traditional malware delivery methods.
Each fileless malware attack poses unique challenges for organizations seeking to detect and prevent them, underscoring the need for a comprehensive and adaptable cybersecurity strategy.
How encryption and fileless malware are used together
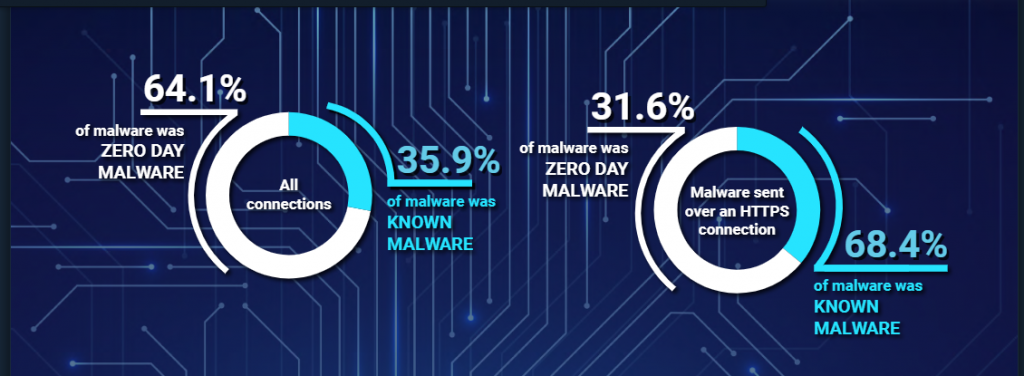
Encryption is a powerful tool that can be used to protect sensitive data from unauthorized access. However, it can also be weaponized by threat actors to conceal the presence of fileless malware within a system. By encrypting malicious payloads or command and control (C2) communications, attackers can effectively hide their activities from security solutions that rely on signature-based detection. In some cases, fileless malware may use encryption to obfuscate its code, making it more difficult for security analysts to reverse-engineer the malware and develop effective countermeasures. This technique, known as “crypting,” is often employed by advanced persistent threat groups and other sophisticated attackers to protect their custom malware tools from discovery.
Additionally, encryption can be used to secure communications between an infected system and the attackers’ C2 infrastructure. By using encrypted channels, like HTTPS or encrypted DNS, cybercriminals can obscure the true nature of their activities and maintain control over compromised systems without raising suspicion.
The challenges of detecting Fileless Malware attacks
Fileless malware presents a unique set of challenges for organizations seeking to detect and prevent these elusive threats. Some of the key challenges include:
Lack of traditional indicators: Because file-less malware does not rely on conventional executable files, it can evade signature-based detection methods employed by many antivirus and endpoint protection solutions. This makes it more difficult for security teams to identify and respond to fileless malware attacks in their early stages.
Use of legitimate tools and processes: Fileless malware often leverages legitimate system tools and processes to carry out malicious activities, making it difficult for security solutions to distinguish between normal and malicious behaviour. This can result in a high number of false positives, complicating the detection process and potentially leading to missed threats.
Stealthy communication methods: The use of encryption and other obfuscation techniques enables fileless malware to communicate with C2 infrastructure discreetly, further complicating the detection process. Security teams must constantly adapt to new tactics and techniques employed by threat actors to maintain visibility into their network communications.
Rapid evolution: Fileless malware attacks are constantly evolving, with new techniques and tactics emerging on a regular basis. This rapid pace of change makes it difficult for organizations to keep up with the latest threats and develop effective countermeasures in a timely manner.
Techniques for protecting against encryption and fileless malware
To effectively protect against encryption and fileless malware, organizations must employ a combination of preventative measures, detection capabilities, and response strategies, as such:
Endpoint detection and response (EDR): EDR solutions can provide enhanced visibility into endpoint activities, including memory and process monitoring, to help detect and respond to fileless malware attacks. By continuously monitoring and analyzing endpoint behaviour, EDR solutions can identify anomalies and potential indicators of compromise (IOCs) that may signal a fileless malware attack.
Behavioural analytics: Leveraging machine learning and artificial intelligence, behavioural analytics can help security teams identify patterns of malicious activity that deviate from normal system behaviour. This can be particularly useful in detecting file-less malware attacks that leverage legitimate system tools and processes and encrypted communications.
Network segmentation: Implementing network segmentation can restrict lateral movement within a network and help contain the spread of fileless malware. By limiting the access and privileges of individual network segments, organizations can reduce the potential impact of a successful attack.
Threat intelligence: Staying informed about the latest fileless malware threats and associated IOCs can help organizations proactively defend against emerging attacks. Organizations can collectively improve their defences against file-less malware and other advanced threats by sharing threat intelligence with peers and industry partners.

Regular patching and updates: Ensuring that systems and applications are kept up-to-date with the latest patches and updates can help reduce the risk of fileless malware attacks. By addressing known vulnerabilities, organizations can limit the attack surface available to threat actors, making it more difficult for them to gain a foothold within the network.
Security awareness training: Educating employees about the risks associated with file-less malware and the importance of following best practices for cybersecurity can help reduce the likelihood of successful attacks. By promoting a culture of security awareness, organizations can foster a more resilient workforce better equipped to recognize and avoid potential threats.
The rise of encryption and fileless malware represents a significant challenge for organizations seeking to protect their digital assets. These stealthy threats can evade traditional security measures and cause significant damage to affected systems and data. Organizations must adopt a multi-layered approach incorporating preventative measures, detection capabilities, and response strategies to combat these threats effectively.
The stakes are high, and the time to act is now. Don’t wait until it’s too late – start fortifying your defences against the invisible threats that imperil your digital existence today.



