Endpoint Security – where the future of cybersecurity is headed
Endpoint: With the rising number of malware throughout these last few years, we have witnessed the advancing of these malicious attacks to the extent that all IT networks have become a very fragile component. Traditional solutions such as antivirus software have become an inadequate defense mechanism because, mostly, they are focused on a specific part of network security. Also, a lot of malware circulating has the capability to bypass a lot of security walls, therefore, manage to compromise the systems. This is why we have to enhance the levels of security, and endpoint security comes in as an essential tool in advanced cybersecurity.
Endpoint security, or endpoint protection, is ensuring the entry point connected to networks are protected from malicious attacks. It plays a crucial role in ensuring that sensitive data and intellectual property are protected from malware, phishing, ransomware, and other cyberattacks on the network or cloud. Endpoints are the entry points of your IT networks, where we also include desktops, laptops, tablets, mobile devices, servers, and printers. And two of the most persistent threats of endpoints, statistically speaking, have been revealed to be ransomware and phishing attacks.
Ransomware is one of the main threats to computer networks, where an attacker can gain unauthorized access to endpoints and proceed with data encryption stored on the device. It’s usually used to steal data, login details of users, and credit card numbers. Similarly, phishing attacks target endpoints via suspicious emails in which they con a person to click on a malicious link, leading to malware installation or freezing of their systems. As we see, endpoints have become an easy target, which is why added security layers are a must to enhance the security of our devices and the data stored in them.

How does endpoint protection work?
The main goal of endpoint protection is to secure the network from unauthorized access, which can be achieved via advanced security software that monitors and secures every entry point.
EPP – Endpoint Protection Platform
Endpoint protection platforms, or else known as EPP, are used to detect and stop perceived threats at entry points. For example, every file uploaded and entered into an enterprise’s internal system must be analyzed thoroughly. And with the help of a cloud-based system, EPP examines the information stored in the file to ascertain where there might be potential threats. With EPP, this platform makes your system familiar with every endpoint that connects to it while making provisions for upgrades to the devices. It can also request login verification of individual endpoints and administer your company’s procedures from one place.
EDR – Endpoint Detection and Response
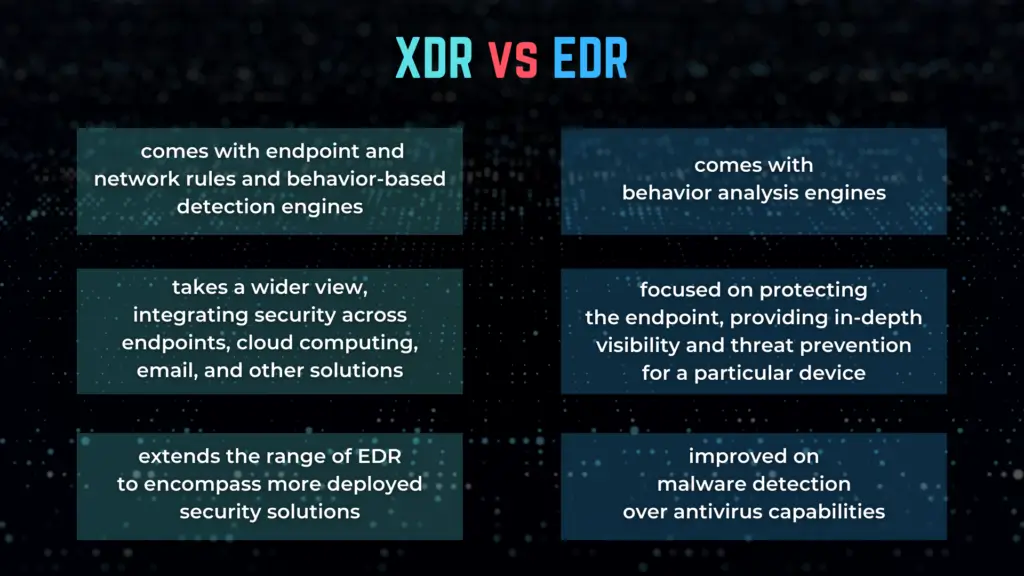
Traditional endpoint detection and response (EDR) systems have become a popular way to protect enterprise endpoints from attacks and breaches and achieve secure remote access. This other advanced security tool continually monitors and responds to advanced malicious attacks. The detection and response mechanism can detect high-risk threats such as different malware and zero-day exploits, bypassing the first layers of protection and managing their way into the organization’s system.
This tool can examine the whole lifecycle of a threat, whether investigating the way of bypassing the security layers, to the point of analyzing how to stop its spreading. For example, if we study the form of ransomware, the objective of this attack is simply the encryption of sensitive data at the expense of the data owner. EDR can help detect the malware and eliminate the threat quickly so we can secure our data. To go to another extent of endpoint protection, some vendors are adding EDR capabilities via extended detection and response (XDR) suites. The difference is that EDR focuses on protecting endpoints only, while XDR has a larger objective.
XDR- Extended Detection and Response
If we can explain it shortly, the Extended Detection and Response solution monitors and prevents cyber threats. This tool analyzes the collected and correlated data of different network entry points and grants visibility to them to comprehend and understand advanced threats that might occur. After the disclosure, the threat can be separated to prevent data loss and security collapse. With this tool, security defenders can identify vulnerabilities and get rid of them at the early stages by adding another security layer to the network system.
What’s the future like for Endpoint security?
Gartner, the technological research and consulting firm, shared their latest in-depth review of the entire endpoint security field of study. After a thorough analysis to determine which key technologies, the firm pointed out that Unified endpoint security (UES) and Unified endpoint management (UEM) are thought to be the next step in endpoint security’s future. UES focuses on endpoint security and provides some management features, while UEM, on the other hand, stresses management and typically includes good security functionality. The Gartner report notes that endpoint protection experts have been focusing more and more on automated detection, prevention, and remediation of vulnerabilities and threats. One of the goals is to protect endpoints while enabling access from any device to any application over any network and with a good user experience in terms of performance and low latency.
Gartner Report
Some other exciting predictions mentioned in the report published by Gartner were:
- Endpoint Protection Platform Forecast predicts that global enterprise spending will reach $13.3 billion in 2021, growing to $26.4 billion in 2025, achieving a compound annual growth rate of 18.7%. Gartner’s latest forecast reflects that enterprise endpoint security is a priority today.
- The Zero-trust network access (ZNTA) framework is planned to be one of the top most implemented frameworks for different ongoing businesses to ensure the safety and the future of these operating businesses. Gartner also notes that cloud-based ZTNA offerings improve scalability and ease of adoption.
- Self-healing endpoint will be a focus point. A self-healing endpoint can self-diagnose a breach and take immediate measures to remediate the threat. This means that organizations are becoming more persistent about endpoint protection, giving them more visibility, control, and security in different IT operations.
So, all in all, we can say that endpoint security is a goal for all organizations to focus on during 2022. Therefore, organizations should harness the knowledge and invest in endpoint security tools to prevent, detect and remediate threats coming from different entry points.