Zuul IoT is called the next generation of technology, a form of revolution that is changing and will continue to do further in our everyday lives. But with this technology’s growth comes the complexity behind these new IoT ecosystems. Machines and objects in virtually any industry can be connected and configured to send data over cellular networks to cloud applications and backends. And as technology advances, anything can be turned into part of the IoT. The benefits of implementing this technology not only in everyday life but in businesses are undeniable. But even though we can now do things deemed impossible decades ago, there are a few downsides to digitizing everything. The more devices are connected to the internet; the more attractive the data becomes for cybercriminals.
Unfortunately, high-profile attacks, combined with uncertainty about security best practices and associated costs, keep many businesses from adopting the technology. But luckily for everyone out there concerned about this issue, Zuul IoT has the solution for you.
Zuul provides a connected Industrial Operations Technology (OT) – cybersecurity platform. They take an asset-centric approach to OT security, enabling security teams to protect critical IIoT/IoT devices at the foundation of essential functions of the business. The centralized security strategy offered by Zuul maximizes security on all endpoints while reducing vulnerabilities, complexity, and human mistakes. We had the chance to talk with John Parmley, CEO of Zuul IoT, for an exclusive interview with 4imag, in which he shared valuable insights.
A little bit of background story of Zuul IoT
“I came to Zuul as a CEO in September last year. One thing about me is that I’ve always spent my entire career in the cyber security space early in my career on the technical side. Then I moved to the dark side of sales and marketing in my mid-career. What intrigued me about coming over to Zuul was the approach to OT (operational technology) or IoT cyber security, which is unique in the industry and piqued my interest.
The technology was developed as an outgrowth to our Co-founders and their yearly experience, which had learned that the process would take a multifaceted approach to secure operational technology and critical infrastructure. As the old saying goes, if all you have is a hammer, all your problems look like nails, and we wanted to have a solution, so every problem seems easy to approach. Today’s status quo is to look at network traffic and use deep packet inspection to determine what’s going on across the network. Even though this might be suitable for specific OT environments, we should move beyond that by looking at security controls existing in the OT environment and leveraging them as much as possible. This is our mission that we are striving to achieve.”
The goal and objectives of Zuul IoT
“We are an early innovative startup company, and it is important to continue growing our customer list and offering our innovative technologies to the market. We already have many customers in production in the transit field or real estate investment trust space responsible for managing building infrastructure for their tenants. But what we want to do further on is to continue down the path of transit and transportation because of the unique requirements in that space, as well as continue down the commercial real estate investment market to protect smart building infrastructure. And for plans, we aim to expand even more. Right now, we are exploring a number of industries and analyzing opportunistically everything based on horizontal solutions, where we’re blurring Fortune 500 companies trying to build out an OT cyber security strategy.
What happens is that most of those manufacturing organizations are embracing and making investments in network monitoring of the OT network to build out an asset inventory list. They’re making some lightweight investments in OT network monitoring and trying to formulate cyber security strategies above and beyond by just creating a master inventory list. But the problem we see in the Fortune 500 space is that many of these companies build out an inventory list of IoT devices. Then they get stuck, not knowing what to do and how do they protect it. This is where we step in and take the lead in helping make the right decisions.”
The innovative approach of the Zuul IoT platform
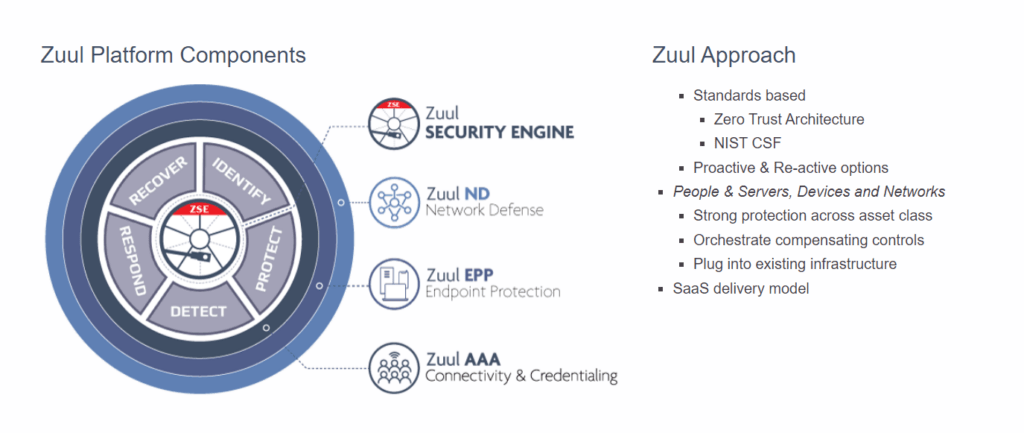
“Our Platform is a SAS (software as a solution), which is a solution that is delivered on the AWF platform. The first underlying technology of the solution encompasses PKI or digital certificates. The second leg of the stool is endpoint protection or the agent for agent lists, and the third leg is network defense. What’s interesting about the solution and what we think is of high value is that those three components are all proven technologies. Digital certificates, PKI, and endpoint protection have been around for years. But the unique thing that we offer to the market is deterministic security. It is well-known that OT-centric devices are designed to perform very limited functions.
But because it performs very limited functions, we can build a hardened operating system and application on that device. First, OT provides some unique opportunities with whitelisting and weightlifting to develop a very tightly monitored and protected solution. The final step is network defense. By tracking the traffic, you can analyze the type of traffic the endpoint will generate, reducing your network monitoring solution’s false positives and negatives. Now what’s interesting is that if you orchestrate all three of these solutions together, it provides significant value over buying three solutions and having a siloed environment, and then trying to push log files through central.
I think one of the significant values of the orchestration of these three legs of the stool is the considerable value above and beyond just integration, so we can have a centralized security policy component which makes a really powerful solution, as seen in the proactive and reactive approach.
The implementation of Zuul in different businesses
“Every business is in a different stage of maturity level; therefore, every business has its unique priorities. One example we have is one with the real estate investment trust companies we have as a client. When they started, their priority was network defense and monitoring. Therefore, we implemented our network defense solution first. And now, as the deployment matures, they want to be introduced to endpoint protection and digital certificates in the environment. They want to extend the security controls to the devices that are unique to that environment. So, in that particular case, we met the customer’s needs where they were until today, where they’re deploying network defense.
It depends on the client’s needs, our 1st priority, and then we start implementing the other components. We want to think of our solution as a form of building a cyber security strategy, which will be a perfect and comprehensive enterprise-wide solution for the OT environment.”
The challenges that they faced and overcame
“Most companies have a very tactical and specific problem that they want to address. The problem is that most cases, they don’t care about anything other than addressing that problem, and that’s why we see today with so many siloed solutions.
And so much shelf ware is because someone buys this one tactical solution. It either never gets implemented, or it gets implemented. Still, the person who made the decision leaves the organization. Now there’s no sponsorship in the organization for maintaining responsibility for that solution. So, we try to straddle the fence by balancing both sides of the equation. And by that, I mean If you want to do network monitoring, then we will deliver network monitoring.
We will provide you with digital certificates if you need digital certificates. But we want to emphasize that even if we meet this particular objective for you, we want to walk down the path with you to where you want to be in four or five years. Now, I think the challenges are typically ownership and accountability of who’s responsible for OT, especially in specific industries. Is it the person responsible for manufacturing and the present chief information security officer? Is it the building management facilities owner of the organization as well? These are some questions we face in our cases and where the institutional challenges are portrayed. And last but not least, one challenge we often face is embracing businesses to deliver an excellent solution to protect their IoT devices.
The challenge is whether they buy IoT devices based on price or capabilities. And what we’re finding is that most organizations that make purchase decisions based on capabilities over the long run are much more successful in securing those environments.”
What should businesses be aware of in terms of IoT Security
“What we have learned so far is that in smart cities or intelligent transportation systems dealing with IoT, you might deal with different components that share information and overlap.
And the problem is who is responsible for both forms of accountability perspective and an ownership responsibility. Who is accountable for cyber security in that environment, and how do you address them? So, as we can see, we are dealing with a bigger issue which is not a technical one but rather an institutional challenge to dividing accountability and responsibility. But at the end of the day, it impacts all of us.”