Zero Trust Security: How it can save your business from ransomware attacks
You’ve probably heard the term “zero trust” security before, especially regarding new user authentication methods. But what does that phrase mean? Zero trust security is an access control practice that emphasises identifying users as trusted or untrusted instead of whether they are authenticated users with a certain level of access. This means that intruders cannot run programs from other users’ accounts, even if your employees have been granted access to systems with sensitive data in such an environment, access files directly from the server, or crack weak passwords. That might sound like a lot of work and different approaches to security. Still, it can be implemented relatively simply and easily across most businesses with little to no resistance from staff members. It also has impressive benefits for any company, including reduced risk of cyber-attacks due to ransomware and other malicious software.
What is Zero Trust Security?
The term “zero-trust” was first coined in 2010 by John Kindervag—a Forrester Research analyst—and is built on the core principle of never trusting anyone and always verifying things. Zero trust security is an access control practice that requires strict identity verification for all users and devices before granting them access to resources, regardless of whether they’re within or outside the network perimeter. That might sound a little confusing, but it means that in a zero trust environment, no one is ever automatically granted access. Every user has to be verified before being granted access to other resources. The zero-trust security model is not a single technology or solution. Instead, it’s a strategy upon which network admins can build the security ecosystem.
The guiding principles of Zero-Trust framework
The guiding principles of a zero-trust framework include the following:
– The path of least resistance: The path of least resistance is the route that an intruder will take. It can run through your network, your computers, or even your users as a weak entry point into your system. A trust-based system may allow certain employees to access specific network parts without proper authentication or knowing their passwords. With a zero-trust system in place, those same employees are blocked from accessing the network or specific data because they don’t have the correct permissions. Even if they try to guess someone else’s password, reset it, or even try to log in with a different system, they won’t be successful because they need the correct access.
– The Principle of Least Privilege: With such a system, no one is ever automatically granted access. As we mentioned above, it doesn’t matter whether they’re an employee, contractor, or even a regular user. Everyone has to be verified as clean before being granted access to sensitive data or network resources. The least privilege principle is based on giving users just enough access necessary for a use case or operation. This means that a particular user account or device will be granted access only to the use case and nothing more.

The benefits for your business
It’s hard to find benefits more important than safeguarding your company data and networks against malicious cyber-attacks. But zero trust security provides more than just protection against ransomware attacks. It also offers effective protection against other malicious software and threats to your network security. This type of approach can increase security measures and reduce the risk of data breaches. When users don’t have access to data, they can’t accidentally or maliciously share it. That means fewer data breaches, less time spent cleaning up the mess, and a lot less money spent.
It can prevent unauthorized access to sensitive data. One of the biggest benefits of a zero trust system is that it prevents users from accessing sensitive data without authorization. This is important for both employee data and customer data. And lastly, it can protect employees from ransomware attacks. When all users are verified as trusted or untrusted, it’s a lot harder for malicious software to sneak in, especially ransomware. Even if it does, it’s much easier to find, track down, and remove without affecting other systems or data.
How Does Zero Trust Security Help Prevent Ransomware Attacks?
When employees are required to authenticate to the network and their systems before being granted access to sensitive data or network resources, a zero trust system makes it more difficult for malicious software to sneak in. For example, a user may try to log in to your network as another employee to download sensitive data, or they might try to run a malicious program that encrypts files and adds a Bitcoin ransom note. If you have a zero trust system, those attempts will likely fail. The malicious software won’t get access to the network, and the employee attempting to log in as someone else will be flagged as untrusted. The network can also alert administrators that a login attempt failed, and they can use that information to track down the source of the attempted intrusion.
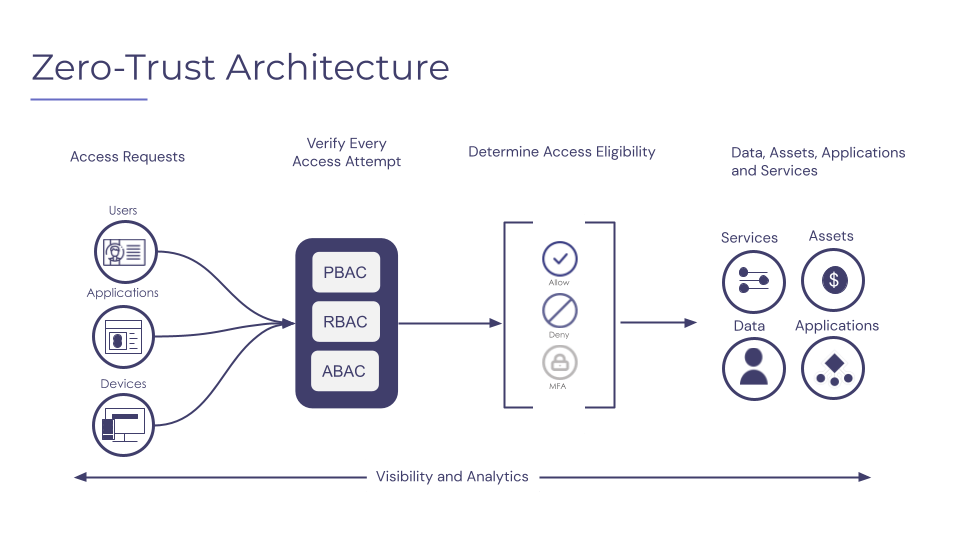
Limitations of Zero Trust security
While there are many benefits of zero trust security, it does come with some limitations. Some of the main limitations of such a system include the following:
– More upfront work: When you first implement a zero trust system, it will require more upfront work to verify users and add them to the system. Users will also take more time to log in because they’ll have to provide two-factor authentication or another verification method. However, once the system is in place, it will operate relatively easily.
– Higher initial cost: Investing in a zero trust system will cost more upfront than a trust-based system. However, it saves a lot of time and effort in the long run, and overall, it’s less expensive than a trust-based system.
– Limitations on mobile devices: Mobile devices are less secure than computers, and a zero trust system is more challenging to implement on a mobile device. In fact, many businesses have a completely different system in place for their mobile devices.

The ‘trust nothing, verify everything’ zero trust approach.
As we mentioned so far, it is a statement when we say that verification is the key to a zero trust security system. A third-party identity verification service should verify employees or contractors before being granted access to the network or access to sensitive data. It also helps to verify the devices used by users before being granted access. For example, before granting access to someone’s iPhone, we must ensure it’s not rooted.
If an employee’s personal phone is rooted, they can easily download malicious software that logs keystrokes and sends them to another computer. This allows them to access sensitive data, such as usernames and passwords. But with a zero trust system in place, no one is ever automatically granted access. This model works on the basic principle of never trusting a user or device and verifying everyone before granting them access to resources. This explicit trust reduces risk and improves security posture regardless of where your endpoints are located.



