Cloud environment: The migration to cloud computing has revolutionized the way organizations operate, offering scalability, flexibility, and cost-efficiency. However, as we’ve ventured deeper into this digital transformation, the complexities and risks associated with cloud environments have become increasingly significant.
According to Synergy Research, the growth of cloud services continues to surge, as evidenced by a 19% increase in spending on cloud infrastructure in 2023. This spending saw its most significant ever quarter-on-quarter rise in Q4 2023.
Furthermore, Gartner, Inc. forecasts a 14% rise in global security and risk management spending in 2024. Factors including cloud technologies, hybrid workforces, generative AI, and regulatory changes drive this anticipated growth. Gartner notes that organizations are enhancing their technical security capabilities, which improves visibility and responsiveness throughout their digital ecosystems.
Understanding the concept of a cloud environment
At its core, a cloud environment refers to the virtual infrastructure that delivers hosted services over the Internet. This encompasses everything from applications and storage to processing power, facilitated through models like Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS). The allure of cloud computing lies in its ability to provide on-demand access to resources, eliminating the need for substantial upfront investment in hardware and software. Yet, this very characteristic introduces a level of abstraction that can obscure the view of underlying security challenges.
As we navigate these virtualized services, it becomes crucial to discern the shared responsibility model governing cloud security. This model describes the obligations of the cloud service provider and the client, emphasizing the need for a collaborative approach to safeguarding the cloud environment.
Delving deeper, we confront the reality that cloud environments are not monolithic but are instead composed of a complex web of interdependencies. These interconnected services create a dynamic, perpetually evolving ecosystem, introducing new features and functionalities. While this fosters innovation and agility, it also presents a moving target for security measures, necessitating constant vigilance and adaptation.
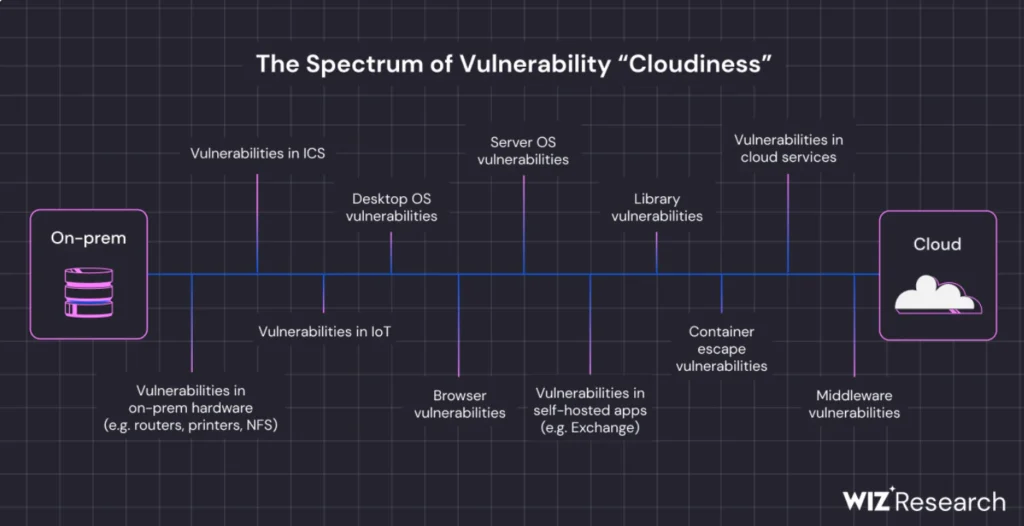
Common vulnerabilities in a cloud environment
Transitioning to examining cloud vulnerabilities, we encounter a spectrum of risks that can compromise cloud-hosted data and services’ integrity, availability, and confidentiality. Misconfigurations, inadequate access controls, and compromised user credentials are among the most prevalent vulnerabilities. According to Forrester, significant breaches involving these vulnerabilities have led to fines and substantial reputational damage for affected organizations.
Misconfigurations are one of the chief vulnerabilities. They occur when security settings are improperly configured, often due to default settings or administrative oversight. This was evident in the case of McGraw Hill, where a misconfigured AWS S3 bucket exposed 22 TB of sensitive data. To prevent such breaches, organizations can employ cloud security posture management (CSPM) tools to regularly audit and correct configurations.
Inadequate access controls compound the security challenges, allowing unauthorized users to access critical resources. The principle of least privilege, which dictates that users should have only the access necessary to perform their duties, is frequently overlooked in the rush to deploy cloud services. This oversight can open the door to data breaches and unauthorized modifications of critical data.
Compromised user credentials represent another significant threat vector, often targeted through phishing attacks and other social engineering tactics. Once an attacker gains access to a user’s credentials, they can move laterally within the cloud environment, accessing sensitive data and resources. For example, the Broward Health data breach, which exposed 1.3 million patient records, was facilitated by overprivileged third-party access. Multifactor authentication and strict password policies can mitigate this risk, but it remains a persistent challenge for organizations.
In-depth analysis of the hidden vulnerabilities
Looking closer, we find less obvious but just as risky problems in cloud environments. These hidden threats include insecure APIs, shadow IT, and the potential for data leakage.
Insecure Application Programming Interfaces (APIs) serve as a gateway to cloud services, enabling automation and integration with other applications. However, if these APIs are not properly secured, they can become a conduit for unauthorized access and data exfiltration. Ensuring robust authentication, encryption, and access controls for APIs is paramount to mitigating this risk.
Shadow IT, which uses unauthorized cloud services by employees, presents a clandestine challenge. Security teams cannot enforce policies or protect against data loss without visibility into these unsanctioned applications. This phenomenon underscores the importance of comprehensive cloud visibility and governance strategies to detect and manage the use of unauthorized services.
Data leakage, whether through misconfigurations, insecure interfaces, or malicious insiders, poses a significant threat to organizations. The ephemeral nature of cloud services and ease of data transfer necessitates stringent controls and encryption measures to protect data at rest and in transit.

Ways to identify vulnerabilities in your cloud
Identifying vulnerabilities in a cloud environment requires a proactive and multifaceted approach. Regular security assessments, including vulnerability scanning and penetration testing, are essential tools for uncovering and addressing security weaknesses.
Adopting a configuration management strategy can help prevent misconfigurations by enforcing standard settings and monitoring for deviations. This approach, combined with continuous monitoring and anomaly detection, enables organizations to identify and respond to potential security incidents rapidly.
Furthermore, embracing a security awareness and training culture empowers employees to recognize and mitigate risks associated with phishing attacks and unsafe online practices. This human element is critical in safeguarding the cloud environment against external and internal threats.
In conclusion, while cloud environments offer many advantages, they also introduce a complex landscape of vulnerabilities that demand diligent attention. Embrace the journey, secure your cloud environment today, and ensure that your organization reaps the benefits of cloud computing without falling prey to its vulnerabilities.



