Security researchers worldwide say the Snowflake breach will be for cloud identity attacks, which is like WannaCry was for ransomware. In July 2024, Snowflake, a leading cloud data warehousing company, experienced a significant security breach that sent shockwaves across the tech industry. The breach, which resulted in unauthorized access to a vast amount of sensitive customer data, highlighted the vulnerabilities that can arise from identity management failures and misconfigurations in complex cloud environments. The first signs of unauthorized access appeared on April 14, 2024, with data thefts surfacing by May 24.
The attackers exploited a combination of compromised credentials and misconfigured permissions to gain access to Snowflake’s systems. According to reports, over 200,000 customer records were exposed, including personally identifiable information (PII) and confidential business data. This incident is estimated to have impacted nearly 5% of Snowflake’s global customer base, underscoring the far-reaching consequences of such breaches in today’s interconnected world. Let’s look deeper into what happened during the Snowflake breach and unpack the critical lessons it offers.
The anatomy of the breach
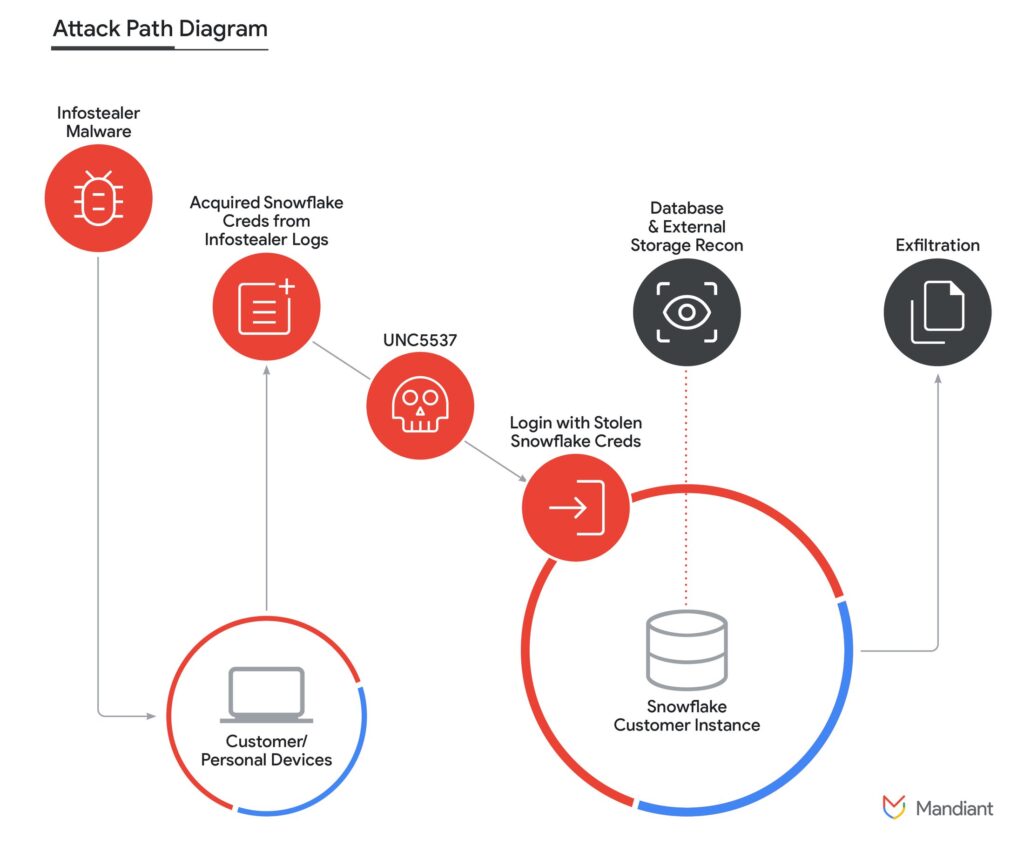
The Snowflake breach unfolded as a textbook example of how a series of seemingly small missteps can snowball into a major security catastrophe. It was the result of a cascade of errors that exposed the vulnerabilities within the company’s cloud infrastructure. The financial damage from the breach was estimated to be in the tens of millions of dollars, compounded by reputational harm and a loss of customer trust. The incident also prompted investigations from regulatory bodies, further highlighting the serious implications of the breach.
However, this incident was more than just a singular breach; it represented the intersection of two significant security vulnerabilities — misconfigured cloud resources and leveraging lost credentials. These weaknesses provided a gateway for attackers to access and compromise sensitive customer data, jeopardizing both Snowflake’s integrity and the privacy of its users.
Overlooked cloud configurations: The breach enabler
The foundation of the breach was laid by improper cloud configurations, an all-too-common issue in complex environments where permissions and access controls are frequently updated. In Snowflake’s case, certain identities were granted excessive access rights far beyond what was necessary for their functions.
These permissions that bypassed all roles became the breach enabler, allowing attackers to leverage low-level accounts to gain higher-level access. This scenario shows us the critical need for identity management and regular audits to ensure access rights are appropriately limited and continuously monitored.
Stolen credentials: the attackers’ entry point
The breach escalated when attackers gained legitimate user credentials, most likely through phishing or social engineering tactics. These credentials served as the attackers’ golden ticket, allowing them to easily bypass many security measures.
Once inside, they could move through Snowflake’s systems under the guise of legitimate users, a method that often evades detection by traditional identity and access management (IAM) tools. This highlights a crucial vulnerability in security systems that rely too heavily on credential-based authentication without additional layers of anomaly detection.

The domino effect escalating access
Once the attackers infiltrated Snowflake’s environment, they exploited the system’s flaws to move laterally, hopping from one compromised system to another. Each step allowed them to escalate their access, eventually reaching sensitive data that was supposed to be off-limits.
This lateral movement represents the true danger in such breaches, where the initial intrusion is only the beginning of a much larger attack. The breach’s progression illustrates the limitations of traditional security tools that often lack the visibility and integration needed to detect and stop such intrusions before they escalate.
The aftermath and lessons learned
The Snowflake breach serves as a sobering reminder of the importance of robust identity and access management practices. It also highlights the need for continuous monitoring and assessment of cloud environments to prevent such incidents in the future. The financial and reputational damage to Snowflake was significant, with industry analysts estimating the cost of the breach to be in the tens of millions of dollars. Moreover, the breach led to a loss of customer trust and triggered investigations from regulatory bodies, further compounding the impact on the company.
In the wake of the breach, Snowflake has implemented stricter security measures, including enhanced monitoring of identity permissions and the adoption of more advanced security posture management tools. These steps are crucial for restoring trust and preventing similar incidents in the future.