The increasing importance of API Security in the age of Digital Transformation
As businesses continue to embrace digital transformation, the use of API (Application Programming Interfaces) has become ubiquitous. APIs have provided a seamless and efficient way for different applications to communicate with each other, making it easier to share data and streamline processes. However, with the increasing use of APIs, adequate security measures have become a pressing issue. The potential risks associated with unsecured APIs can range from unauthorized access to sensitive information to complete system breaches. As a result, locking the gate on API security has become a top priority for businesses that want to safeguard their data and maintain customer trust.
The Importance of API Security in Digital Transformation
As mentioned, digital transformation has changed businesses’ operations by providing new opportunities to create value and improve efficiency. APIs have become critical to this transformation, allowing businesses to integrate different applications and services seamlessly. However, with the increasing use of APIs, the potential risks associated with unsecured APIs have become a significant concern for organizations. A single unsecured API can provide a gateway for hackers to access sensitive information, cause data breaches, and disrupt business operations.
Therefore, API security is essential in digital transformation because it protects against cyber threats. It helps ensure that the data transmitted through APIs are secure and that only authorized users can access it. API security also enables businesses to build trust with their customers by protecting their personal and sensitive information. That’s why businesses that ignore API security risk damaging their reputation and losing customers’ trust. To ensure their APIs are secure, businesses must adopt a proactive approach to API security. This involves identifying potential threats, implementing security measures, and continuously monitoring and updating security protocols.
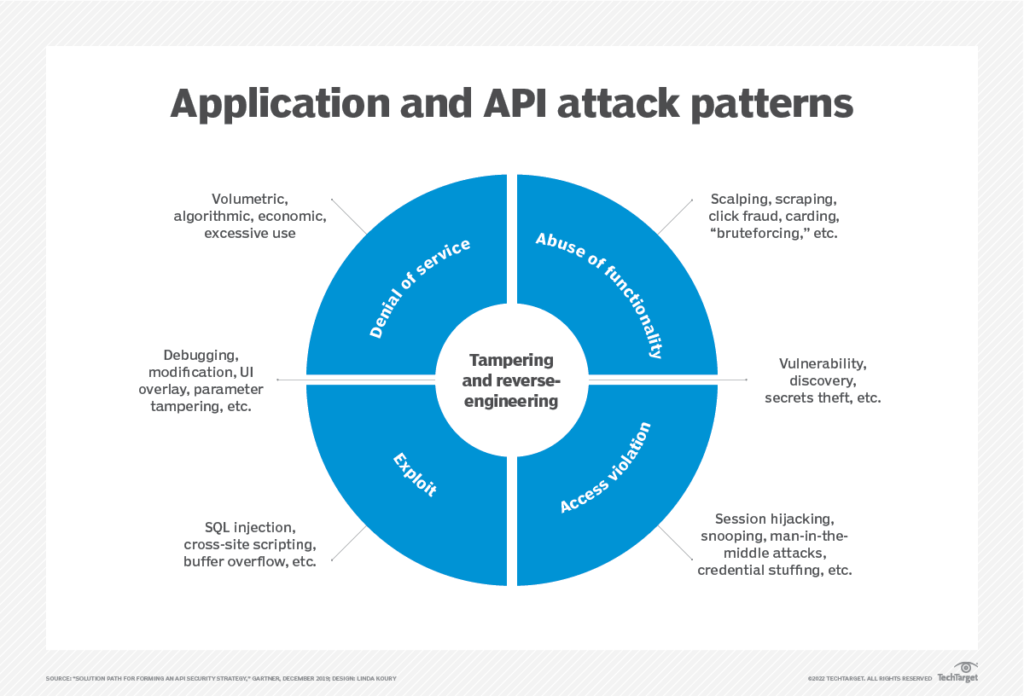
API security threats to watch out for
One of the most common API security threats is Injection Attacks. These attacks occur when an attacker injects malicious code into an API request, which can result in the execution of unauthorized commands or access to sensitive data. Injection attacks are a prevalent API security threat, and businesses need to implement security measures such as input validation, parameterized queries, and stored procedures to mitigate this risk.
Another significant API security threat is Broken Authentication and Authorization. This occurs when an attacker gains unauthorized access to an API by exploiting authentication and authorization processes vulnerabilities. Businesses must implement strong authentication mechanisms, such as multi-factor authentication, to ensure only authorized users can access their APIs.
Denial of Service (DoS) Attacks are also a significant API security threat that can cause significant damage to businesses. These attacks occur when an attacker floods an API with requests, causing the API to become overwhelmed and unavailable. Businesses can prevent DoS attacks by implementing rate limiting and throttling, which limit the number of requests that can be made to an API within a specified period.
Man-in-the-Middle (MitM) Attacks are another API security threat businesses must be aware of. These attacks occur when an attacker intercepts communication between two parties and can eavesdrop on or modify the communication. Businesses can protect their APIs from MitM attacks by implementing secure communication protocols such as SSL/TLS and using digital certificates to verify the identity of clients and servers.
But, to ensure that APIs are secure and protect sensitive data, businesses must implement best practices for API security.
Best Practices for APIs security
One of the essential best practices for API security is implementing strong authentication and authorization mechanisms. This involves verifying the identity of users and devices accessing the API and enforcing strict access controls to limit unauthorized access. Multi-factor authentication and using secure protocols such as OAuth and OpenID Connect can help prevent unauthorized access to the API.
Encryption can help prevent unauthorized access to sensitive data transmitted or stored on the API. Encrypting data in transit and at rest is another crucial best practice for API security. This involves using secure protocols such as HTTPS to encrypt data transmitted through the API and strong encryption algorithms to encrypt data stored on the API server.
To protect against DoS attacks, businesses can use rate limiting and throttling to limit the number of requests that can be made to the API within a specified period. This can help prevent the API from becoming overwhelmed and unavailable, ensuring continuous service for authorized users. Finally, monitoring and auditing API activity can help businesses identify potential security threats and proactively protect their APIs. This involves tracking API usage, detecting anomalies, and generating alerts for suspicious activity. By monitoring API activity, businesses can identify and respond to security threats before they cause significant damage.
API security regulations and compliance
API security regulations and compliance become crucial for businesses to ensure their APIs are secure and their sensitive data remains protected. Compliance with various regulations and standards is mandatory for businesses to follow. Some of the most important regulations and standards that businesses must comply with include the following:
General Data Protection Regulation (GDPR)
The GDPR is a comprehensive regulation that outlines how businesses should collect, process, store, and transfer the personal data of EU citizens. Compliance with the GDPR is mandatory for businesses that process personal data through APIs. Businesses must ensure that their APIs are designed to protect personal data and provide adequate safeguards to prevent unauthorized access.
Payment Card Industry Data Security Standard (PCI DSS)
The PCI DSS is a set of security standards designed to ensure the secure processing, storage, and transmission of credit card data. Compliance with the standard involves implementing secure payment processing procedures, encrypting sensitive data, and conducting regular security assessments. Businesses that process credit card data through APIs must comply with the PCI DSS.
Health Insurance Portability and Accountability Act (HIPAA)
HIPAA is a regulation that governs the handling and storage of protected health information (PHI). Businesses that process PHI through APIs must comply with HIPAA. Compliance with HIPAA involves implementing secure access controls, implementing encryption for PHI, and conducting regular security assessments to ensure compliance. In addition to these regulations and standards, businesses must comply with other industry-specific regulations and standards. Compliance with these regulations and standards helps companies to protect their APIs from various security threats and ensures that their sensitive data remains secure. Failure to comply with these regulations and standards can result in severe financial and reputational damage to businesses.
Therefore, with the increasing amount of data being exchanged through APIs, businesses must prioritize the security of their APIs to protect against security breaches and data leaks. The future of API security will involve more sophisticated security measures, such as AI-driven threat detection, blockchain-based authentication, and zero-trust security models. As technology evolves, businesses must stay up-to-date with the latest API security best practices and compliance regulations to ensure that their APIs remain secure and that their sensitive data remains protected.


