The growing threat of Cybercriminals targeting VPN: What you need to know
In recent years, the online world has become increasingly vulnerable to cybercriminals. As VPN (Virtual Private Networks) continue to grow, so does the risk of cyberattacks. Unsurprisingly, VPNs have become a significant target for hackers and other cybercriminals. But why are they targeting these networks in the first place? The answer lies in the fact that VPNs provide a secure and private connection to the internet, allowing users to access restricted websites, protect their data, and even bypass internet censorship. Moreover, the anonymity offered by VPNs makes them attractive targets for criminals, as they provide a way to hide their identity and location. As such, it is important to understand the growing threat of cybercriminals targeting VPNs and the steps that can be taken to protect against them.
What is VPN?
Virtual private networks (VPNs) are online services that allow users to protect their online activity and send data through a network. VPNs can be used to add a layer of security to your internet connection and protect you from the prying eyes of hackers or government surveillance. VPNs can also allow you to access content that might be blocked in your country, such as news channels or sports programming, and are often used in a corporate setting to allow workers to access company resources from remote locations securely. They can also be used to protect online banking and online shopping or to access public WiFi. Some VPNs, like NordVPN and ExpressVPN, are used by millions of people daily and are very popular.
What are the methods cybercriminals use to target VPN?
According to the VPN Risk Report, a survey based on the opinions of 351 cybersecurity professionals claims that remote access solutions are not without a challenge. “Breaches show that it only takes one infected device or stolen credential to put an entire network at risk, which is why cybercriminals are targeting users by accessing through a VPN,” the report reads. It has been reported that cybercriminals are using a combination of methods to target VPNs, including IP address detection, traffic analysis and brute-force attacks.
IP address detection: Cybercriminals can use IP address detection to find out whether you use a VPN by identifying it as a “false’’ IP address. This can be done by analyzing your computer’s IP address to see if it matches your VPN’s IP address. With this method, cybercriminals can determine whether you are using a VPN by comparing your IP address to the IP address of your VPN.
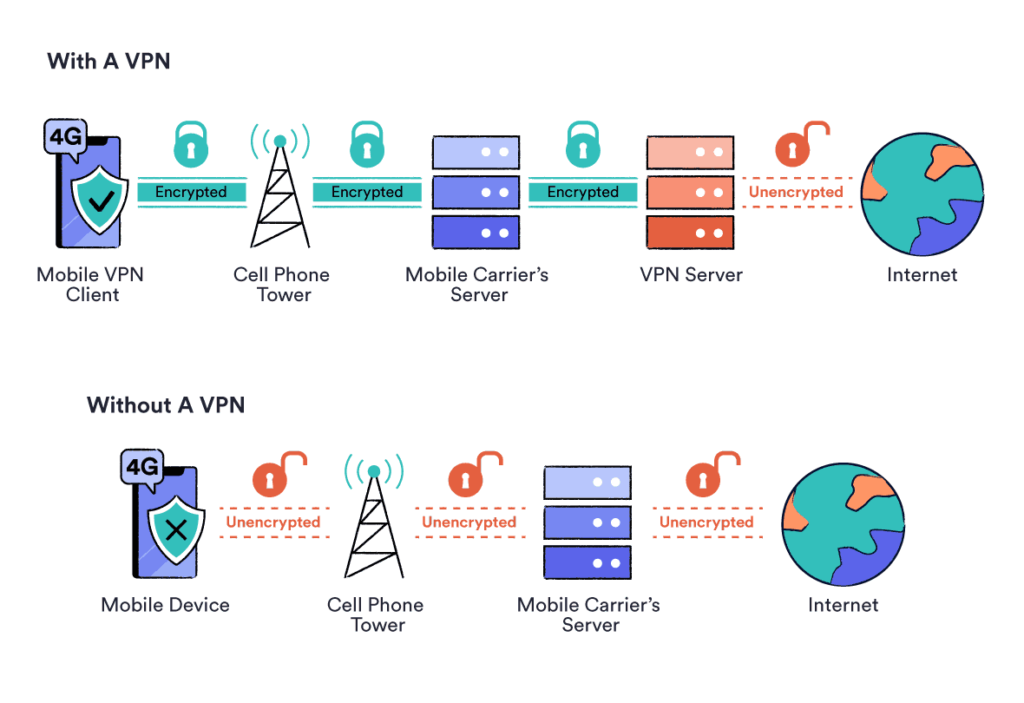
Traffic analysis: Traffic analysis, also known as traffic fingerprinting, looks at how your data travels over a network. It analyzes the data and looks for similarities or anomalies in the traffic to determine if someone is using a VPN. This method is especially effective when used in combination with other methods.
Brute-force attacks: These attacks can be used to crack an account that uses a VPN by repeatedly attempting to log in with a false password. If a cybercriminal manages to crack your account, they can steal your data and use your VPN to mask their activities.
What are the risks posed by cybercriminals targeting VPNs?
Cybercriminals targeting VPNs can pose a serious risk to your online safety. If cybercriminals successfully target a VPN, they can hijack your traffic and use it to conduct malicious activity, such as distributing malware or spam. They can also intercept the data you send over the internet and steal sensitive information, such as your passwords or credit card numbers. Then they can even use your sensitive data to borrow money, apply for government benefits, take out personal loans, commit credit card fraud, and carry out other online crimes. Another risk posed by cybercriminals targeting VPNs is that they can use the VPN to host malicious content, such as child exploitation material or distributed denial-of-service attacks.
Another common risk that gets overlooked is that VPNs are often used to give third parties access to corporate resources. It is common for companies to use “site-to-site” VPNs to connect and share resources. Over time, the rules on the VPN termination devices get stretched thin as more holes are opened. This approach to managing the connectivity is not only risky but consuming as well. It also assumes that every employee from that company should have the same access as every other employee, but that is often not the right approach because it leaves many opportunities to attack. So, what can we do to protect ourselves if our VPN communication has been corrupted?
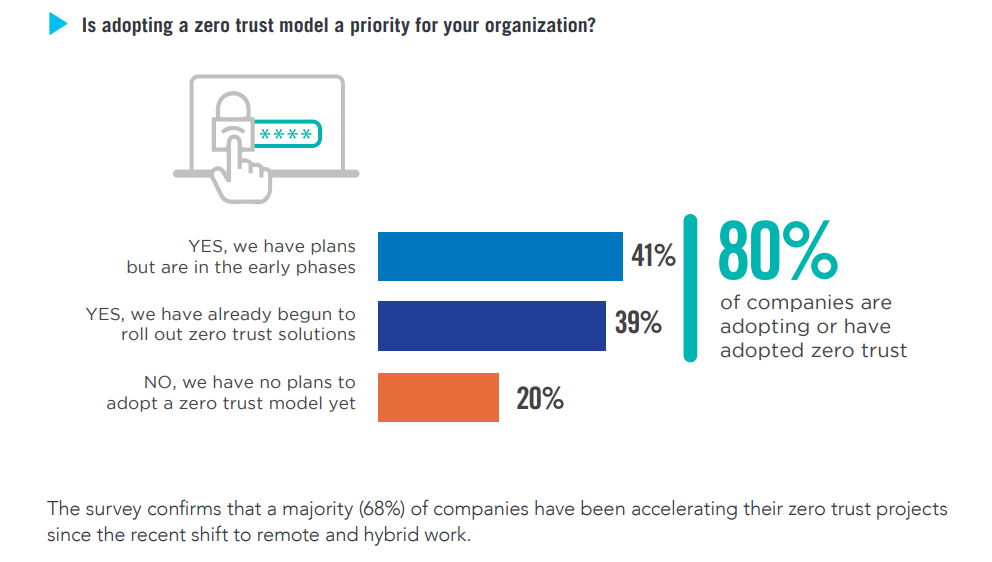
How can you protect yourself from cybercriminals targeting VPNs?
The best way to protect yourself from cybercriminals targeting VPNs is to ensure your VPN is secure. The best way to do this is to quickly check your VPN’s security features before signing up for it. But even after different evaluations, the worst can happen, and your VPN can get corrupted. If your virtual private network (VPN) gets hacked, you should take the following steps:
Stop using the VPN right away. Using a possibly infected system gives cybercriminals access to your confidential data.
Uninstall the VPN. A lot of VPNs have services running in the background. Depending on the hack, cyber attackers would employ it to gain more details and even direct access to your devices.
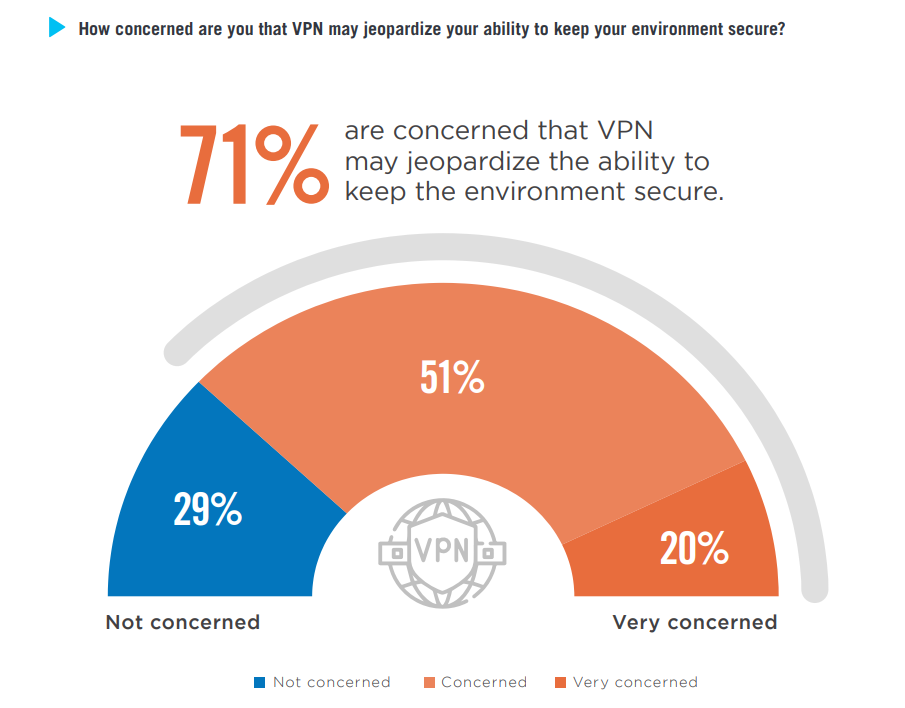
Change the VPN credentials. Suppose any information you have entered for sign-up has been compromised, such as your email, password, name, and the like. Never use them again. If you use your password for other applications, websites, or emails, modify those too. This process is much easier if you have a dependable password manager like CyberGhost VPN offers.
Re-evaluate your VPN. Not every hack is a comprehensive violation. That being said, VPN hacks are more concerning than others since they handle delicate information. Be on the lookout for opinions from cybersecurity professionals—does the VPN’s response address the issue, and was the breach handled professionally? If the answer is no, you should reconsider changing your VPN.



