Online voting defined
Electronic voting (e-Voting) is an alternative way of voting by citizens that can be applied to any voting using electronic methods over traditional ones. The range of users can be extensive, including methods ranging from a simple electronic automated vote count to the entire exercise of every citizen’s right to vote. It also helps many non-“active” voters, due to not having easy access to the respective polling stations, to vote electronically. But there are also some caveats, especially in direct electronic voting systems where large-scale electronic fraud can easily be committed, both in citizen identification and vote-counting process. So, we need a digital voting system with all the rules and principles governing that.
The main objective of an e-Voting system is to support all the required services for the organization and conduct of an electoral process, which is either included in the framework of parliamentary elections, is a referendum, or is carried out internally by an organization or collective body or institution. Depending on the type of electoral process, the system supports the definition of electoral districts, the registration of combinations and candidates, the creation of electronic ballots, the entry of voters’ data for the creation of electoral lists, the creation of means of authentication for voters, the automatic counting of votes after the end of the electoral process, etc.
Naturally, security and voter privacy are of major importance and largely determine whether the system is widely accepted. Therefore, the security and trust mechanisms incorporated by e-Voting systems are highly sophisticated, making the most of the possibilities provided by recent technological developments.
Features and characteristics for online voting security issues
The functions and features of online voting in terms of security are the same since it is a digital online information system. Therefore, the challenges in the field of cyber security are many and varied, and the latest technology needs to be used as much as possible to effectively address the security issue in a digital online voting system.
So, we’re talking about understanding the attack of systems that can be exploited and manipulated by a malicious attack. Based on events that have already occurred in information systems, the attack can be from the Internet or offline. The main problem is the undetectability of a cyberattack on a system. For example, ShadowWalker, a particularly high-level instance, exists only in memory and cannot be examined from the most privileged levels of the operating system. This kind of software is difficult to remove without affecting the operating system or even erasing its trace. As we said above, even when a device is not connected to the Internet. Malware has been installed on “air-gapped devices”, e.g., via USB and other removable media.
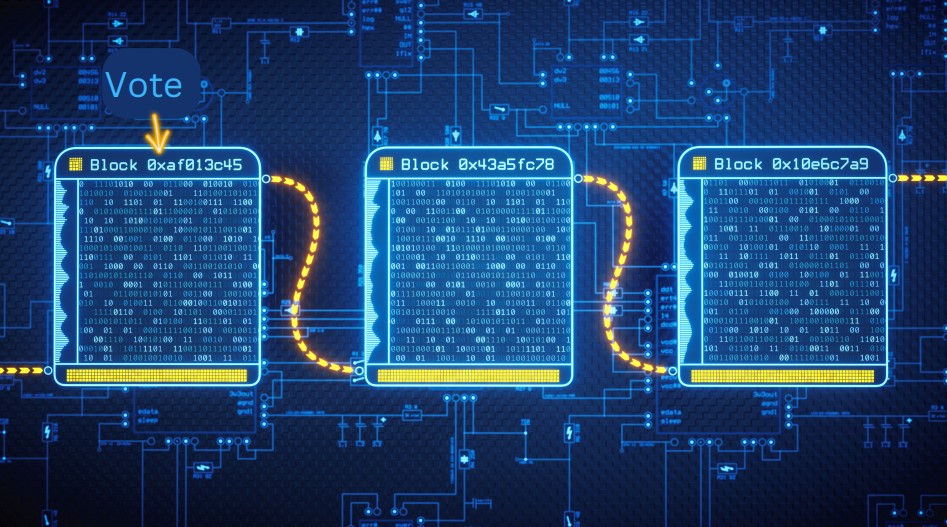
As mentioned in a previous article, an online voting system should be created to overcome attacks of various kinds with malicious software or cryptographic attacks, attacks on databases, etc. In a previous article, we mentioned all the categories (SQL injection, Brute Force Attack, etc.) of attacks on an information system. The solution proposed based on the latest developments in the field of IT security is the blockchain solution. Blockchain refers to a wide range of technologies, such as distributed databases, hashing, digital signatures, and multi-party computing, so it seems somewhat complicated. But all the above individual technologies exist in a cryptocurrency like Bitcoin.
The security, in this case, lies in the fact that most mining hashes agree with the Bitcoin protocol (in this case, Bitcoin). Similar security conditions exist in other cryptocurrencies. Below we describe the idea for the future use of this technology in an online voting system.
Future Usage of Blockchain Technology for an online e-voting system
Blockchain technology seems to be helpful in electronic voting on the Internet. But using cryptographic signatures can eliminate vote forgery and use hashing and distributed consensus to maintain a vote book that attackers can’t break unless they participate in large part of the network. Based on this, we understand that a vote can work like a cryptocurrency using blockchain. But using a device like a smartphone should be protected and not compromised. Therefore, there should be secure software in the first place so that the security of the blockchain can work because otherwise its vote could also be compromised.



