Albanian Cyberattack Continues
The infamous cyberattack that happened in Albania at the beginning of summer took every IT professional’s attention based on the attack’s nature. In July of this year, the Albanian government…
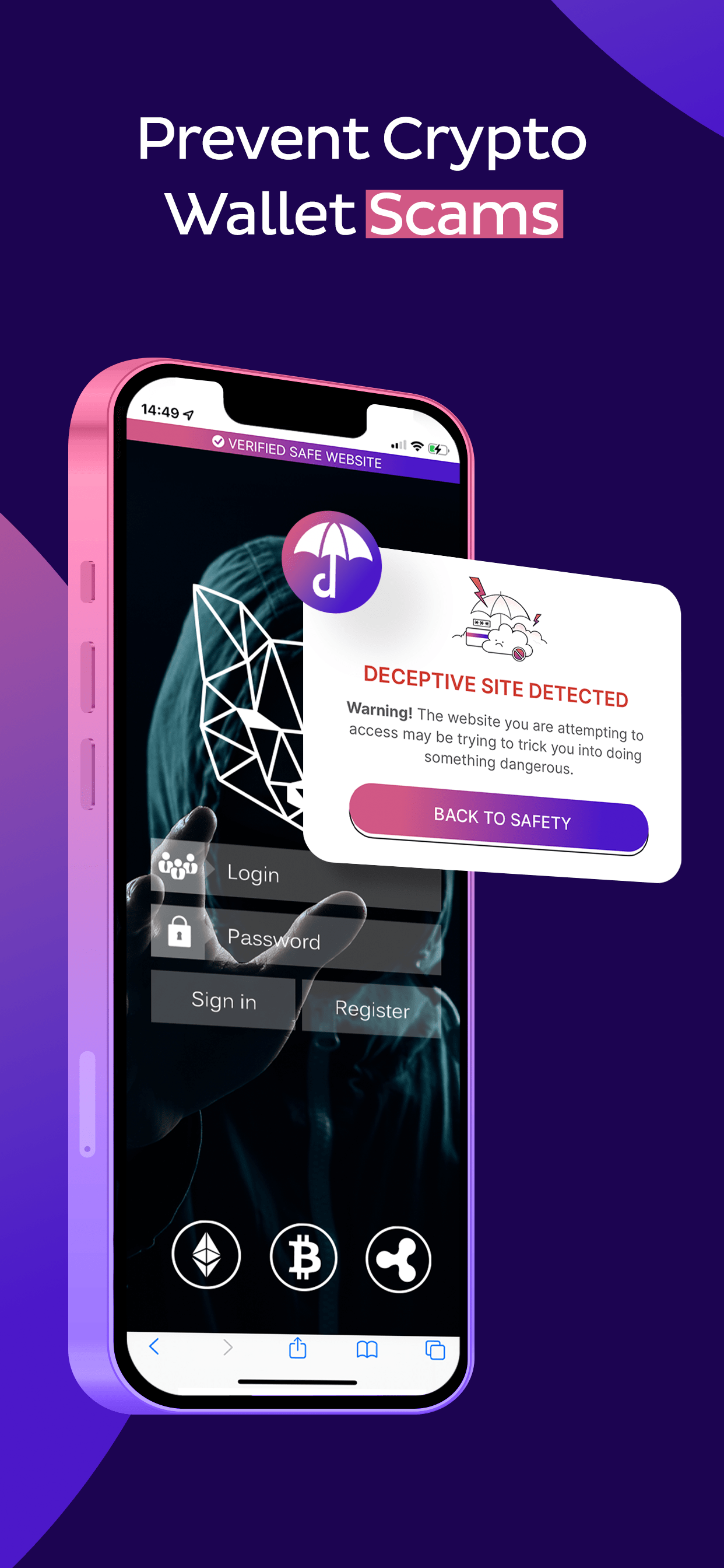
novoShield to Power the Next-Generation of Mobile Phishing Protection Solution
Mobile Phishing: novoShield’s enterprise-grade mobile security solution provides advanced phishing protection and seamless UX for individuals and businesses of all sizes. novoShield, the next-generation mobile phishing protection solution designed for…
Neeva, the alternative to Google that looks to users and not to advertisers
Neeva: An ad-free search engine that doesn’t sell personal data. But you pay “We believe that advertising-funded search engines will be inherently biased towards the advertisers and away from the…
Best Android and iPhone Antivirus Softwares to have in 2022
In our heads, when we think of antivirus software, they are typically linked with Windows PCs and laptops. But it is important to know that it’s critical to have these…
Acid Rain – the new malware that rained down on Europe
Last February on 24th it was reported a new cyber-attack happened on a satellite communications company named Viasat, which attacked their infrastructure in Ukraine. The company, in their new security…
Rohde & Schwarz reveals future-proof OEM deep packet inspection engine for encrypted traffic visibility
DPI engine R&S®PACE 2 uses advanced AI-based techniques including machine learning and deep learning to deliver real-time insights into encrypted traffic for networking and cybersecurity solutions Leipzig, Germany — April 13, 2022 — today,…
2022 CYBERTHREAT DEFENSE REPORT
Record-setting Ransomware Attacks, a Shortage of Skilled Personnel, and Low Security Awareness Across the Workforce Cause Headaches for IT Security Teams Annapolis, MD – April 4, 2022 – CyberEdge Group,…
Security Compass: building secure software is only the beginning
Security Compass was started in 2004 by Nish Bhalla to address a specific problem: creating secure software. “I was lucky enough to be employee number two” Rohit Sethi, CEO at…
Tips on how to protect yourself on Social Media
Social media nowadays has become a crucial part of our everyday life, from the moment we wake up and get into our phones, till the end of the night when…
The risk and reward of biometric technologies
Biometric technologies use an individual’s biological traits to identify them. Digital fingerprint scanners on mobile phones and in airports, or intelligent facial recognition camera systems are examples. When combined with…