Are your applications bulletproof against today’s sophisticated cyber threats? Engineers understand that robust application security is not optional—it’s critical. Effective security testing methodologies, specific strategies, and industry best practices can significantly enhance your defences. How prepared is your organisation to tackle these challenges and stay ahead of potential threats?
Application security testing methodologies
To effectively identify and mitigate application vulnerabilities, security professionals rely on a range of testing methodologies, each offering unique advantages and insights. The three primary testing methodologies are Static Application Security Testing (SAST), Dynamic Application Security Testing (DAST), and Interactive Application Security Testing (IAST). SAST involves analysing an application’s source code, bytecode, or compiled binaries for coding flaws and security weaknesses without executing the code. This method is typically performed during the development phase, helping identify and remediate issues early, thereby reducing overall remediation costs.
In contrast, DAST analyses an application while running, simulating real-world scenarios to exploit potential vulnerabilities. This approach focuses on how the application responds to malicious inputs, identifying issues like authentication flaws and business logic vulnerabilities that may not be detectable through static analysis alone. IAST combines the strengths of both SAST and DAST, analysing an application’s source code, configurations, and runtime behaviour. This comprehensive approach provides a holistic view of potential vulnerabilities, allowing for identifying issues that may be missed by either method alone. By leveraging a combination of these methodologies, organisations can thoroughly understand their application’s security posture and proactively address identified vulnerabilities.
Analysing best practices
Implementing effective application security requires a holistic approach encompassing various best practices and strategies. While the specific tactics may vary depending on the application’s nature and the organisation’s security requirements, several overarching best practices can help organisations achieve a robust application security posture.
Integrating security practices throughout the software development lifecycle (SDLC) is crucial for developing secure applications from the ground up. The Secure Software Development Lifecycle (SSDLC) is a framework that incorporates security considerations into every phase of the development process, including:
Requirements gathering: Identifying and documenting security requirements and threat models early in the development process.
Design: Incorporating secure design principles, such as the principle of least privilege and defence in depth, into the application’s architecture.
Implementation: Adhering to secure coding practices, conducting code reviews, and implementing security controls during development.
Testing: Performing comprehensive security testing, including static and dynamic analysis, to identify and remediate vulnerabilities before deployment.
Deployment: To minimise the attack surface, implement secure deployment practices, such as secure configurations and hardening.
Maintenance: Regularly monitoring and patching deployed applications to address newly discovered vulnerabilities and security updates. By adopting an SSDLC approach, organisations can proactively address security concerns throughout development, reducing the overall cost and effort required to secure applications.
Secure coding practices and code reviews
The keys to developing secure applications involve focusing on the development practice of properly secured coding and going through detailed code reviews. The process of secure coding includes using established guidelines and best practices for writing robust code, which will hopefully involve accepting user inputs, managing errors properly in program services, and appropriate memory management.
On the other hand, a code review is a thorough audit of the source code by skilled security professionals or automated software. The purpose of these reviews is to detect the existence of a vulnerability, incorrect or inaccurate code and lack of security rules while coding aimed at the developer correcting it before deploying their application. It is no secret that integrating secure coding practices in the development process and performing a code review can greatly decrease the chances of introducing vulnerabilities or weaknesses to an application, which also helps improve its security stance at large.

Security testing and vulnerability management
Comprehensive security testing is a critical component of an effective application security strategy. This process involves subjecting the application to various testing methodologies, including static analysis, dynamic analysis, penetration testing, and fuzzing, to identify potential vulnerabilities and weaknesses.
Static analysis involves examining the application’s source code or compiled binaries without executing the application, while dynamic analysis consists of analyzing the application’s behaviour during runtime. Penetration testing simulates real-world attack scenarios to evaluate the application’s resilience against potential threats, while fuzzing involves subjecting the application to unexpected or malformed inputs to identify potential vulnerabilities.
Once vulnerabilities are identified, an effective vulnerability management process is essential. This process involves prioritizing and addressing identified vulnerabilities based on their severity, potential impact, and the availability of remediation measures. Regular patching and updating of applications and their dependencies are crucial to mitigate newly discovered vulnerabilities and maintain a robust security posture.

Continuous monitoring and incident response
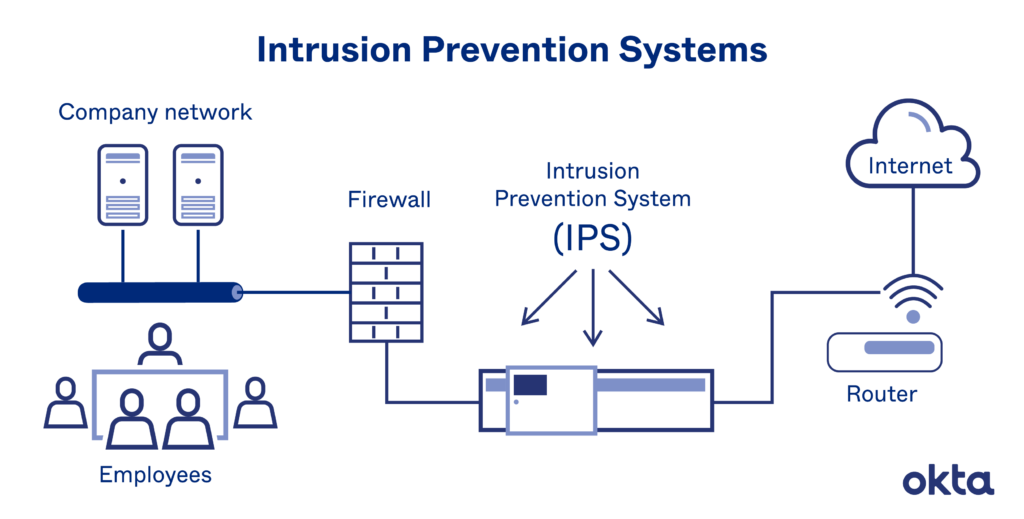
Continuous monitoring involves actively monitoring applications, systems, and networks for potential security incidents, anomalies, or indicators of compromise. This process can involve various techniques, such as log analysis, intrusion detection and prevention systems (IDS/IPS), security information and event management (SIEM) solutions, and real-time threat intelligence feeds. By continuously monitoring the application environment, organizations can rapidly detect and respond to potential security incidents, minimizing the potential impact and reducing the risk of data breaches or system compromises.
An effective incident response plan outlines the procedures and steps to be taken in the event of a security incident, ensuring a coordinated and efficient response. This plan should include roles and responsibilities, communication protocols, incident containment and eradication strategies, and post-incident analysis and recovery procedures. By implementing continuous monitoring and an effective incident response plan, organizations can proactively identify and respond to security incidents, minimizing the potential impact and facilitating a timely recovery from any successful attacks or breaches.
Security awareness and training
Building a culture of security awareness and training all employees, developers, and stakeholders is key to maintaining strong application security. Security awareness training programs help equip everyone with knowledge of the kinds of threats they may be facing, how to prevent them, common practices that should always be followed, and more specific information on their roles when it comes to protecting applications.
It should involve training on secure coding practices, data handling procedures, incident reporting rules, and the need to use security policies and guidelines. Ongoing security awareness campaigns and training can reinforce these principles and keep employees alert for any signs of a breakdown in the preventive measures that help identify and squelch potential threats. Organizations can make their employees part of the application security process by creating a culture that values safety and offering ongoing training to reduce human error and enhance overall security effectiveness.

