The zLabs team identified a sophisticated Mishing (mobile-targeted phishing) campaign that delivers malware to the user’s Android mobile device, enabling a broad set of malicious actions including credential theft of banking, cryptocurrency and other critical applications.
The investigation revealed a network of phishing domains actively distributing a new variant of the Antidot banking trojan. This previously unknown strain builds upon the version discovered by Cyble in May of 2024.
The attackers presented themselves as recruiters, luring victims with job offers. As part of their fraudulent hiring process, the phishing campaign tricks victims into downloading a malicious application that acts as a dropper, eventually installing the updated variant of Antidot on the victim’s device, which we call AppLite Banker.
Beyond its ability to mimic enterprise companies, the Banker also masquerades as Chrome and TikTok apps, demonstrating its wide-ranging target vectors, including full device take-over and application access. The level of access provided the attackers could also include corporate credentials, applications and data if the device was used by the user for remote work/access for their existing employer.
Distribution methods
The attackers behind this phishing campaign demonstrated a remarkable level of adaptability, leveraging diverse and sophisticated social engineering strategies to target their victims. A key tactic employed by the attackers involves masquerading as a job recruiter or HR representatives from well-known organizations. Victims are enticed to respond to fraudulent emails, carefully crafted to resemble authentic job offers or requests for additional information. Figure 1 is an example of one of the emails associated with the campaign, identified by the inclusion of a company name previously observed in related campaign activity.
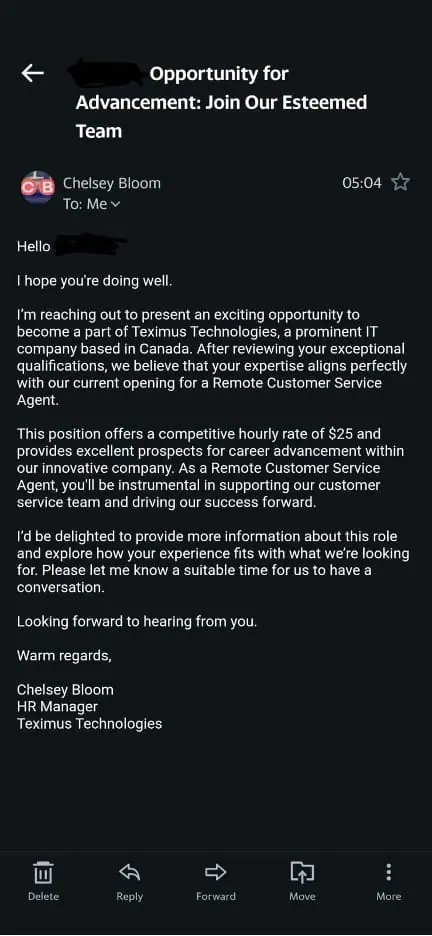
In a subsequent communication, the threat actors direct victims to download a purported CRM Android application. While appearing legitimate, this application functions as a malicious dropper, facilitating the deployment of the primary payload onto the victim’s device. As depicted below, the malicious site acts as the initial entry point for the attack.
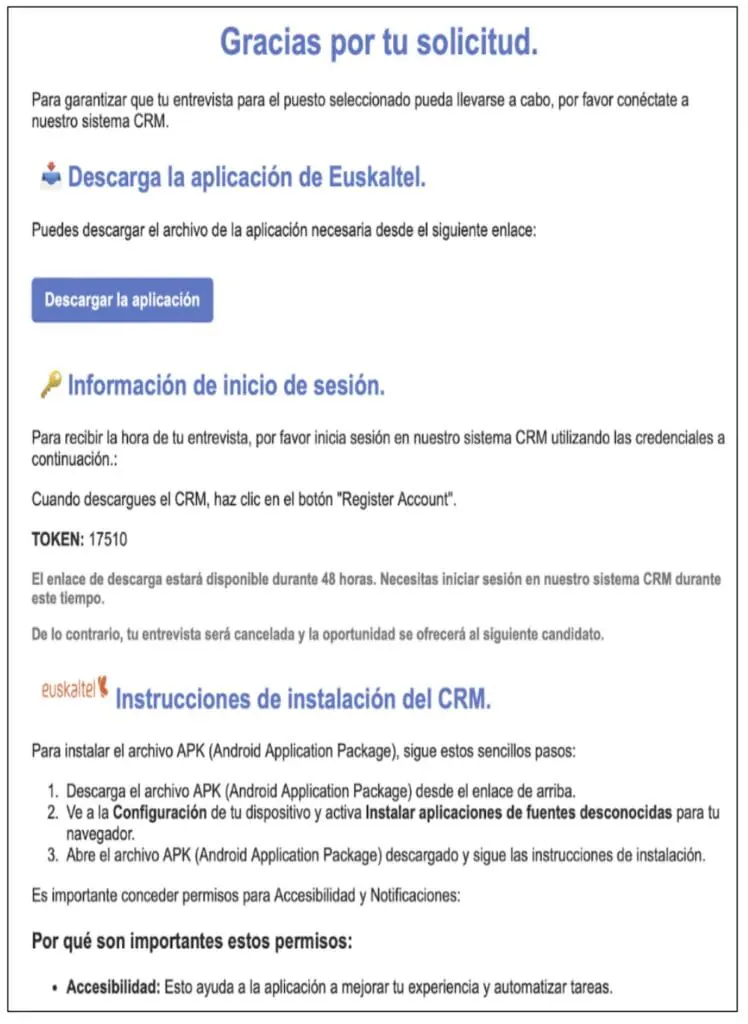
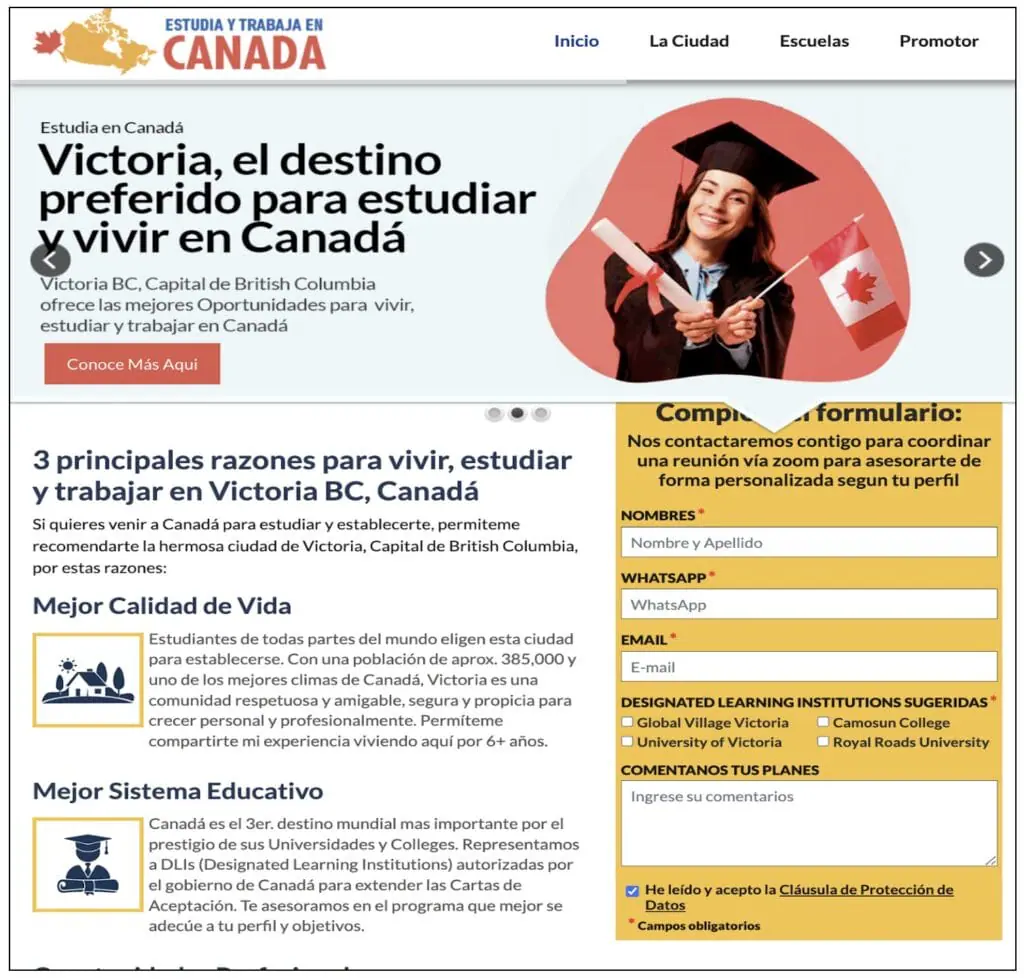
As seen above in Figure 2 several prominent corporations, such as Euskatel, Eminic, Distributel, and Oasis, were used as bait to entice victims. We also identified the attackers targeting other verticals, including educational institutions. Figure 3 illustrates a phishing website impersonating an educational institution, designed to trick users into downloading a malicious APK.
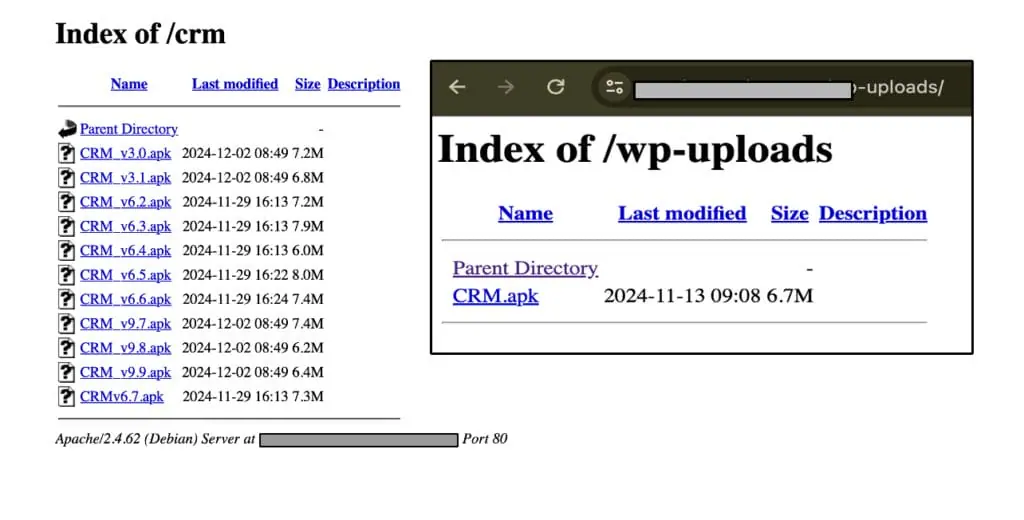
During the analysis, the team identified a network of malicious domains actively involved in distributing the malicious APKs. It is believed that these domains are propagated primarily through social engineering attacks.
Attack Sequence
The diagram below illustrates one of the methods employed to distribute and execute the AppLite malware on the victim’s mobile device throughout the campaign.
Threat actor impersonates HR representatives from well-known companies, crafting emails to appear as legitimate job offers.
Victims are redirected to a malicious landing page to continue the application process or schedule an interview.
The landing page manipulates victims into downloading and installing a malicious dropper application.
Once installed, the dropper delivers the AppLite banking trojan onto the victim’s device, enabling further malicious activity.
SOURCE: zimperium.com



