Remediant – The groundbreaking cyber solution for privileged access management transformation
Remediant: We live in a world where cyber-attacks are becoming more and more often. Usually, the main goal of these malicious attacks is to retrieve sensitive information about a user. We are seeing breaches occurring daily. As such, it is vital that security teams can quickly and accurately detect breaches or even unprivileged access to prevent malicious attacks from expanding their reach. The type of attacks that we most commonly see is those whose goal is to exfiltrate sensitive data by gaining higher and unauthorized access.
This attack method is also known as the Lateral Movement method, which hackers use to move through a network in search of data or assets to exfiltrate. The attacker will try to gain higher privileges, allowing them to move laterally (between devices and apps) through a network. This way, they can identify targets and gather all the information needed. If the attacker manages to secure administrative privileges, malicious activities can be performed inside the system, and detecting it might be hard to differentiate.
But what can a company do if faced with a situation like this? Our first suggestion that comes to mind is Remediant, the first company to offer the first and only solution that consists of agentless Lateral Movement Prevention, which administers dynamic Just-in-Time (JIT) privileged account access to help customers achieve Zero Standing Privilege.
4imag has the exclusivity of getting an interview from Raj Dodhiawala, President of Remediant, Inc. Raj Dodhiawala has over 30 years of experience in enterprise software and cybersecurity, primarily focused on bringing disruptive enterprise products to new markets. Currently serving as President of Remediant, he is bringing focus, agility and collaboration across sales, marketing, finance and operations and leading the company through its next growth phase. We talked with Mr Dodhiawala, who shared valuable insights about the company and lateral movement prevention strategies.
How did the founders come up with the idea of creating an innovative platform that combines different cyber solutions such as Remediant?
Remediant, the leader in privileged access management transformation, was founded by Paul Lanzi and Tim Keeler, who both have a background in helping defend public and private organizations from corporate espionage attacks via state-sponsored agencies and organized cybercrime groups. During this time, they found that most cybersecurity breach cases were tied to privileged access management and lateral movement, inspiring them to develop a unique, patented concept to stop cybercriminals in their tracks. This resulted in the inception of Remediant SecureONE, a product that eliminates privilege sprawl across the enterprise.
What are some of the top products or solutions you are offering in the market that are considered innovative and have significantly impacted the cyber defence world?
Remediant SecureONE is a groundbreaking solution that addresses critical whitespace in the privileged access management (PAM) market. Whereas PAM focuses on credential management, our solution focuses on managing the privilege sprawl: the unnecessary 24/7 administrator access availability and the key vector of attacks. Remediant enables zero standing privilege (ZSP), which removes all admin accounts from systems (or endpoints), providing just-in-time access to the specific system at the right time for the right amount of time that the administrator requires to administer the system.
According to Verizon’s 2022 Data Breach Investigations Report, this year has seen a 25% increase in ransomware attacks, a 13% increase over last year, which is more than the previous five years combined. When looking across the range of cyber-attacks today, attackers in more than 80% of incidents use compromised admin credentials to elevate their privileges. What concerns these kinds of attacks is that the hacker can expand their abuse by harvesting new credentials and implicit trust conferred to privileged users, moving around laterally while remaining undetected – virtually having a free-for-all.
Stopping lateral movement has a significant impact on the outcome of an attack. Remediant SecureONE prevents this privilege escalation in its tracks because, without privileged access, the attacker cannot move around the organization to find crown jewels.
What is the main focus point of your platform, and where do you see the future of Remediant in a few years?
Remediant’s product has three core elements:
Zero Standing Privilege (ZSP) – This technique removes all privileged accounts to ensure a hacker cannot leverage compromised credentials.
Just-in-Time Administration (JITA) guarantees that administrators can connect to a system only when required and for the right amount of time.
Agentless – The solution runs without deploying an agent on each system.
It’s important to note that the privileged access management space is going through a transformation, shifting the focus to zero trust. As more and more organizations are deploying applications to the cloud and moving to remote work environments, they now have systems that are not connected to the enterprise network but operating in a distributed environment.
This becomes an issue for privileged accounts as it is becoming somewhat decentralized and distributed, growing the privilege sprawl and dramatically increasing the privileged identity attack surface. We are continually expanding the capability of our product to address managing privilege sprawl not just in enterprise networks but also in cloud systems and workloads.

Regarding the Lateral Movement Prevention solution, what are the key features that you are offering inside the platform that are based on this solution? How do you implement this solution into the business infrastructure?
In order for the attackers to accomplish the mission, whether they are attacking an endpoint on the network, a remote laptop, or the cloud, they have to move laterally. When we prevent them from doing so, then essentially, the attack becomes ineffective. We aren’t letting them get an elevated privilege into any of the systems through the three elements mentioned previously: zero standing privilege, just in time administration and agentless.
Zero Trust is all about identity, more specifically privileged identity. In terms of the business infrastructure, including privileged identity as part of the Zero Trust framework provides an extra layer of protection that protects your enterprise.
What kind of adjustments are needed to make in the platform in order to correspond to every specific need and changes of the business? How is this approach maximizing ROI?
One of the main benefits of our solutions is that they are simple to deploy. Since our products are easy to use and integrate seamlessly into existing security infrastructure and existing IT processes, the total cost of owning and operating the product is super low.
What maximizes ROI and drives high accuracy is the fact that we can stop the privilege escalation and lateral movement. By doing this we can directly influence or reduce costs, such as insurance premiums and or avoiding an attack.
What should Security engineers (pen testers, CISO, red teaming etc.) and DevOps engineers expect while using this platform?
One of the main benefits of our solutions is how easy it is to use, embrace and adopt within an organization with the help desk of IT admins, DevOps and/or IT security teams.
Our customers are easily able to integrate our products in the manner in which they do their DevSecOps work. Remediant fits into their preexisting framework and organizations do not need to go through the onerous task of learning another tool.
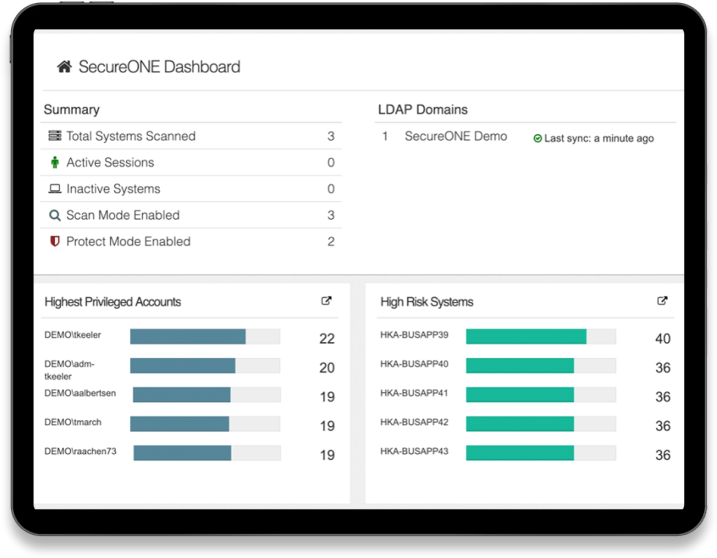
Did you encounter any challenges while implementing Remediant in different companies/businesses?
Remediant’s solution requires no heavy lifting, which is why there are few variations in our approach to particular industries.
This may seem surprising, but there aren’t implementation challenges. Remediant deploys very rapidly and provides all the infrastructure the customer needs to get the application going. Our solution continues to scan the environment automatically, so the customer doesn’t have to lift a finger; it’s agentless.
What sets us apart from legacy PAM products is that they require a lot of discovery, analysis, and configuration work upfront. It often takes months and even years to fully deploy legacy PAM solutions. In our case, none of that is relevant. We make the discovery automatically, provide the insights, visualizations, analytics, and place systems in protection mode, guiding customers to get rapid value out of our product.
Q8: Based on your experience and handling different scenarios, what seem to be some critical points and vulnerabilities that businesses most commonly suffer from?
Multi-factor authentication validates the user and does a decent job of protecting credentials. However, what’s missing is the next step of protection. Should the person granted access have 24/7 access to systems that they don’t need to use continuously? Once the system authenticates the identity, there often is no control or authorization, and that’s a large blind spot for organizations.
This is one of the most common causes of cyberattacks; hackers obtain credentials and are given 24/7 access to them. An example of this is the Okta hack that occurred in March. The cybercrime group Lapsus$ gained access to Okta’s administrative accounts. It later moved to compromise additional systems and gain control of the ‘crown jewels’, which posed risks to Okta’s systems and their customers and supply chain. This incident, along with many others, followed the pattern of compromised credentials, giving hackers a free for all to an organization’s information once they’re in a system.
Protecting organizations from these attacks is as easy as establishing a proper privileged access management program. Still, it requires a methodical approach: even after discovering and vaulting the most coveted accounts, it is essential to look at standing privileges across the estate. As headlines continually show us, managing your standing privileges is one of the most critical and effective methods to prevent lateral movement and halt most incidents. The longer you wait to address it – the greater your chances of becoming a headline.

What advice would you give to different companies regarding endpoint security? Would securing endpoints be the future of cybersecurity?
Endpoint security has gained much importance lately, particularly with EDR, endpoint detection response and XDR. It has become a buzzword and is a solution that all organizations are looking to implement if they haven’t done so already. However, it’s also important to recognize that the EDR/ZDR solutions are backwards-looking: meaning that for them to work, a threat has to occur or an attack is progressing, which these EDR/XDR solutions may first detect and then stop. So, it does not prevent an attack; it stops it from moving forward or worsening its impact.
There is no one size fits all solution that can 100% prevent the incidents we see – something is bound to get in. The attacks we see today are a testament to that. Looking ahead, the future of cybersecurity will look further upstream from a protection perspective and ask how we stop lateral movement instead of acting after the fact.
Since we see the trend of the moment, the – Zero Standing Privilege, what are your thoughts on this new security strategy? What benefits might come from it?
As we touched on earlier, the idea that authenticated individuals have 24/7 access to privilege sprawl is a hacker’s ‘field day.’ The only way to prevent a hacker is to take all the privileges away. To do these, zero standing privileges need to be implemented.
ZSP states that there should be no 24/7 access available to anybody in the organization. When Remediant SecureONE is protecting systems with ZSP and JITA, our customers find that even the red teams express frustration that they cannot complete their tasks and confirm that the environment is very well protected from privilege escalation and lateral movement. It is fundamental to solid security, and zero-standing privilege is the best way to get there.



