Security concerns in the Metaverse you need to watch out for in 2023?
As the Metaverse continues to evolve and expand, so do the security concerns associated with it. We are entering a new era of digital life, where online identities and virtual worlds are…
Dutch hacker obtained virtually all Austrians’ personal data
VIENNA (Reuters) – A Dutch hacker arrested in November obtained and offered for sale the full name, address and date of birth of virtually everyone in Austria, the Alpine nation’s…
Israel’s Cognyte won tender to sell intercept spyware to Myanmar before coup
By Fanny Potkin and Poppy McPherson SINGAPORE (Reuters) – Israel’s Cognyte Software Ltd won a tender to sell intercept spyware to a Myanmar state-backed telecommunications firm a month before the…
The Top 10 weakest passwords of 2022 – Did your password made the list?
Weakest passwords: In the age of technology, having a secure password is becoming increasingly important. Unfortunately, many people still use weak passwords, leaving them vulnerable to attack. Protecting your information…
A look back at the Top Security Issues of 2022: What we learned and how to avoid them in the future
2022 was a year of unprecedented events, and the security landscape was no exception. As the world grappled with the effects of the global pandemic on businesses and individuals, cybercriminals…
Hacking of bank cards analyzed
Specific problem hacking define New, more convincing tricks have recently been applied by astute people who attempt to steal money from bank debit or credit cards. Under the weight of…
Hackers using OAuth malware to hijack email servers
OAuth has two main purposes on the web right now. Often, it is used to create an account and log in to an online service. OAuth 2.0 is an authorization…
Kaspersky Transparency Center
“The cybersecurity market needs to open up because customers need to trust it” The Russian invasion of Ukraine has changed world geopolitics and many companies’ fortunes. The international escalation between…
What benefits brings the Multi Factor Authentication implementation in everyday processes
For the past years, the security of different information systems has relied on the function of the password. The more the password filled the requirements to be stronger and adapt…
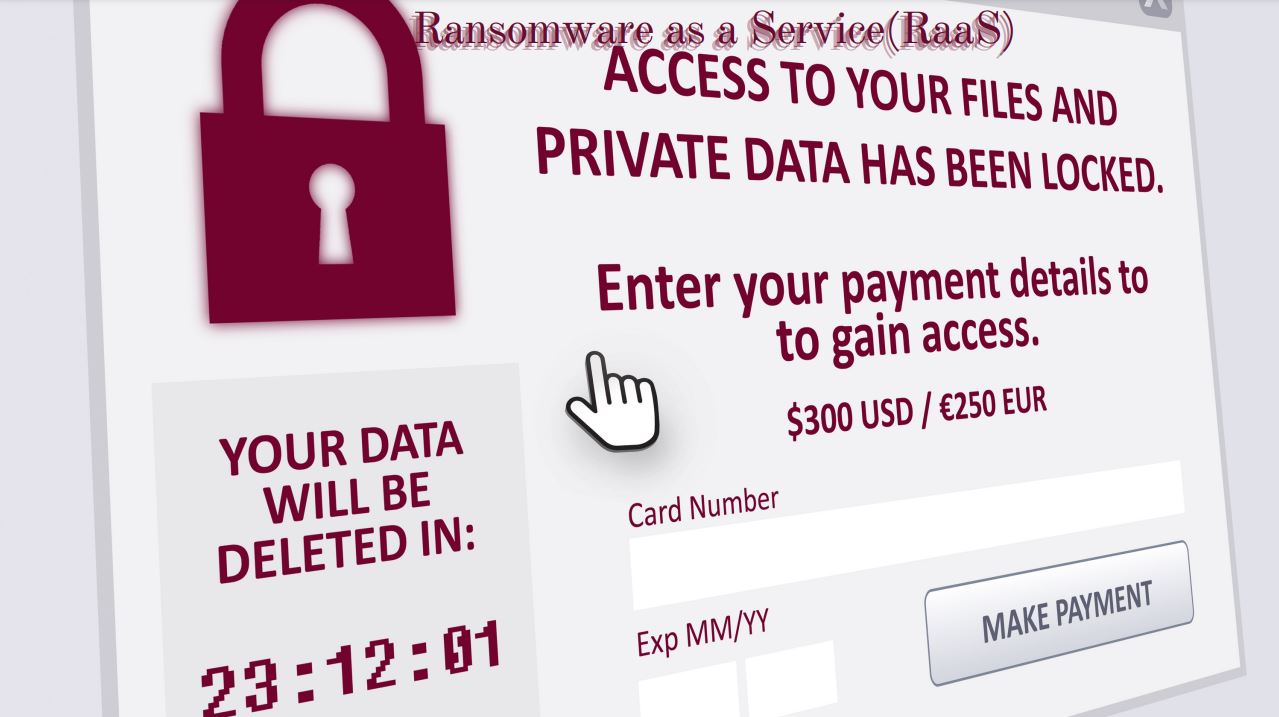
RaaS – Ransomware as a Service
RaaS: In recent years, the ransomware threat has continued to grow. The most apparent trend is that ransomware groups are now targeting larger businesses and, in doing so, can demand…