Microsoft, Cisco, Google, IBM, and Amazon said that their services were vulnerable to the new threat
The Log4j vulnerability poses a serious threat to the functioning of the entire internet, affecting major technology vendors.
Tech companies, including Microsoft, Cisco, Google, IBM, and Amazon have just reported that their services were vulnerable to the new threat and made their effort to issue fixes. Also, they have advised customers on how to protect themselves and released guidance on how to mitigate the threat.
According to experts, this new vulnerability in the open-source Apache logging library is of the most serious software flaws in recent times and can provide hackers with unfettered access to computer systems.
The flaw, which is known as Log4Shell, came to light on Tuesday and prompted an urgent warning by the US Government’s Cybersecurity Agency, and many other technology organizations, agencies, and companies. The hackers, however, seem to have taken advantage of the Log4j vulnerability since the beginning of December.
According to Apache Software Foundation (ASF), this is the second Log4j vulnerability discovered, and a patch has already been released for this issue. The first attempt to cope with the flaw was deemed as “incomplete in certain non-default configurations”.
“Earliest evidence we’ve found so far of Log4J exploit is 2021-12-01 04:36:50 UTC. That suggests it was in the wild at least 9 days before publicly disclosed. However, don’t see evidence of mass exploitation until after public disclosure” wrote Matthew Prince, Co-founder, and CEO of Cloudflare, on Twitter.
Hackers have exploited the Log4j vulnerability in many ways. “The vast majority of observed activity has been scanning, but exploitation and post-exploitation activities have also been observed. Based on the nature of the vulnerability, once the attacker has full access and control of an application, they can perform a myriad of objectives. Microsoft has observed activities including installing coin miners, Cobalt Strike to enable credential theft and lateral movement, and exfiltrating data from compromised systems” said Microsoft in a recent report.
“This vulnerability, which is being widely exploited by a growing set of threat actors, presents an urgent challenge to network defenders given its broad use. End users will be reliant on their vendors, and the vendor community must immediately identify, mitigate, and patch the wide array of products using this software. Vendors should also be communicating with their customers to ensure end-users know that their product contains this vulnerability and should prioritize software updates” US Cybersecurity and Infrastructure Security Agency director Jen Easterly said in a written statement.
“We are taking urgent action to drive mitigation of this vulnerability and detect any associated threat activity. We have added this vulnerability to our catalog of known exploited vulnerabilities, which compels federal civilian agencies — and signals to non-federal partners — to urgently patch or remediate this vulnerability. We are proactively reaching out to entities whose networks may be vulnerable and are leveraging our scanning and intrusion detection tools to help government and industry partners identify exposure to or exploitation of the vulnerability” she added.
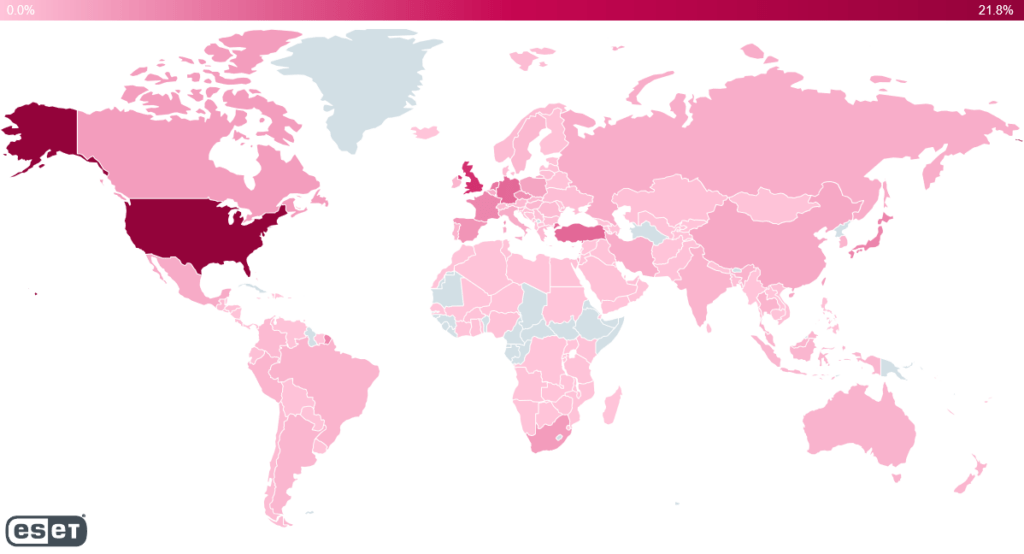
The Dutch National Cyber Security Center has also released a report with the software that is affected by the Log4j vulnerability, while the international security company ESET created a map showing where Log4j exploitation attempts have been made. Based on the map, the US, UK, Turkey Germany, and the Netherlands are the areas where most hacker attacks are detected. Microsoft Threat Intelligence Center (MSTIC) has also observed the Log4j vulnerability being used by multiple tracked nation-state activity groups originating from China, Iran, North Korea, and Turkey.
“This activity ranges from experimentation during development, integration of the vulnerability to in-the-wild payload deployment, and exploitation against targets to achieve the actor’s objectives,” said Microsoft.
The UK’s National Cyber Security Centre recommended a set of priority actions, such as to “install the latest updates immediately wherever Log4j is known to be used”, “discover unknown instances of Log4j within an organization”, and “deploy protective network monitoring/blocking”.
“The NCSC is aware of widespread scanning for this vulnerability, and we note that almost all organizations will have received HTTP requests with the JNDI string. We do not require reports of scanning activity. However please notify the NCSC of any cases where you have identified malicious Java being loaded into one of your systems, or where any follow-on activity has occurred” said the UK’s National Cyber Security Centre.



