Specific problem hacking define
New, more convincing tricks have recently been applied by astute people who attempt to steal money from bank debit or credit cards. Under the weight of the ongoing public awareness campaign in recent months, Internet hackers have been forced to improve their techniques.
Many fall victim to criminals who scan their card details using specially modified devices (skimming) and then steal their money. In a small store in America, a man noticed that they had installed a skimming device in the POS, where when the customer paid with their card, it would copy it and store their codes. Copies of the cards passed through the POS are made, and cash is withdrawn using the pin.
Another method of hacker theft is that they approach and remove small amounts from the debit cards of unsuspecting citizens intact, without even reaching into the pocket of their victims, as long as they bring the tiny devices they have within three centimetres of the point where they the card is located. Spirals have gone a step further by withdrawing cash with wireless… POS devices. We remind you that contactless debit or credit card holders do not need to enter a code for amounts up to 25 euros. However, they can become “financiers” of savvy wireless POS users if they approach them and come within close range.
A new type of malware has emerged targeting POS used by restaurants and hotels to steal payment information stored on the device. These recent attacks have disrupted financial institutions, vendors, and users who are trying in every way to protect their data.
Features and characteristics
The new malware aims to steal banking information and customer details, such as card details. However, the nature of POS makes it different from other malware. The payment card industry follows specific security standards whereby personal data is end-to-end encrypted. However, to process data, data in RAM is decrypted. Criminals target RAM and try to find security weaknesses to steal the information after decryption. If successful, hackers can choose which data to steal and upload to a remote server. On the plus side, POS malware limits the actions of criminals. Stolen bank details cannot be used to make online purchases. This is because the magnetic strip and chip do not contain the three-digit number (CVV2) required for online shopping. To use the stolen information, the criminal must clone the credit or debit card.
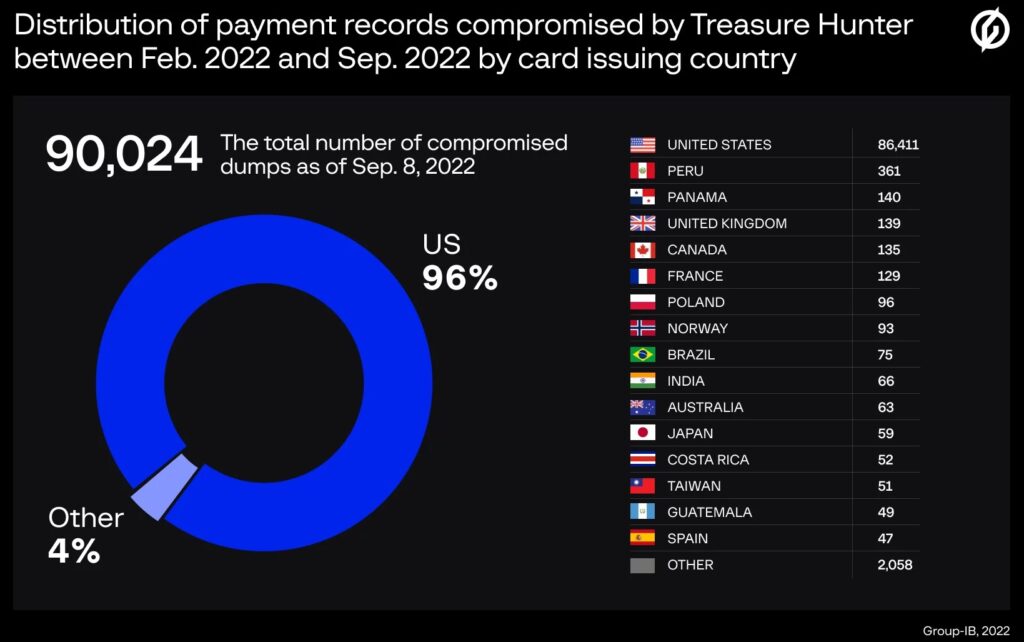
Researchers reported that threat actors used 2 PoS malware variants to steal information about more than 167,000 credit cards. Initially, the MajikPOS PoS malware was first detected by Trend Micro in early 2017 when it was used to target businesses in North America and Canada. Group-IB researchers identified the C2 server of the POS malware called MajikPOS.
Unfortunately, on July 18, 2019, the source code for MajikPOS (aka MagicPOS) was offered for sale on the cybercrime forum “exploit[.]in” by the user cartonash. MajikPOS is written using the “NET framework” and uses an encrypted communication channel to avoid detection. A misconfiguration of the server allowed experts to investigate the activity of its operators and discover that it was also used as a C2 for other POS malware called Treasure Hunter. Fraudsters did not use sophisticated techniques to compromise targets; they could gain access to PoS systems through brute force attacks on Virtual Network Computing (VNC) and Remote Desktop Protocol (RDP) services protected by easy passwords. Cybercriminals sometimes used command-line FTP (File Transfer Protocol) or a modified version of Ammyy Admin to install the MajikPOS malware.
Future solutions usage
With the new contactless cards, further POS malware attacks are fewer, but every development in technology comes with unknown security risks, so the corresponding actions for security development are necessary.
Trend Micro and Bitdefender products can protect the devices with which you access e-banking and avoid malicious activity. Unfortunately, as users, we cannot know if a POS is infected, as this is the seller’s responsibility. For this reason, we should be cautious, frequently checking our e-banking transaction history to prevent purchases by criminals who have compromised our bank cards. Notifying the bank in case of suspicious movements in our account can protect our bank details and prevent bigger damage.



