Zimperium uncovers sophisticated SMS stealer campaign: android-targeted malware enables corporate network and application infiltration
Over 105,000 Malware Samples Identified Key Findings: Over 95% are/were unknown and unavailable malware samples Malware hijacked OTP text messages across more than 600 global brands Approx. 4,000 samples contained…
What is Hybrid Cloud Security?
With the increasing adoption of cloud computing, the complexity of managing and securing these environments has grown significantly. Hybrid cloud security has become a crucial aspect of modern IT strategy,…
Essential cybersecurity tools for your PC in 2024
Essential cybersecurity tools: As we enter the second half of 2024, it becomes increasingly evident that security is a part of our lives. From viruses masquerading as the most innocent…
Why you should use incognito mode
Websites and companies, including giants like Google, track your activities through your browser; this is not news. But while altogether avoiding browsers isn’t practical, using incognito mode is a powerful…
Top 5 free virus scanners to fortify your devices
Top 5 free virus scanners: As we entrust our personal and professional lives to the convenience of technology, the threat of malicious software, or malware, becomes larger. Viruses, worms, Trojans,…
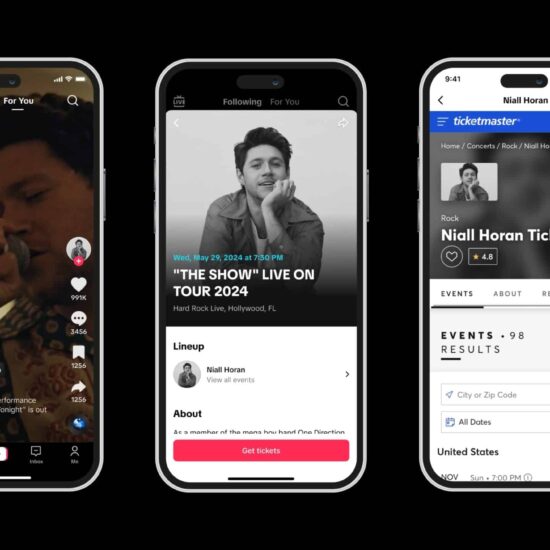
Live Nation admits Ticketmaster hacking
A big problem for the company and its customers A data breach in which the personal data of 560 million people was stolen. A huge reputational hit for Ticketmaster, a…
Black Hat Asia 2024: exploring cross-cache attacks
In the realm of cybersecurity, cross-cache attacks have emerged as an extremely popular technique for exploiting heap-based vulnerabilities. These attacks serve as the foundation for many well-known exploit methods, including Ret2dir and…
Dutch privacy watchdog recommends government organisations stop using Facebook
By Bart Meijer and Anthony Deutsch AMSTERDAM (Reuters) – The Dutch privacy watchdog AP on Friday said it was recommending that government organizations should stop using Facebook as long as…
What vulnerabilities are hidden from your cloud environment?
Cloud environment: The migration to cloud computing has revolutionized the way organizations operate, offering scalability, flexibility, and cost-efficiency. However, as we’ve ventured deeper into this digital transformation, the complexities and…
Microsoft announces the new Surface PCs optimized for AI
At the Advancing the New Era of Work with Copilot, Microsoft announced new Surface AI PCs: Surface Pro 10 and Surface Laptop 6. The two devices offer high performance, longer battery…