Top 5 free virus scanners to fortify your devices
Top 5 free virus scanners: As we entrust our personal and professional lives to the convenience of technology, the threat of malicious software, or malware, becomes larger. Viruses, worms, Trojans,…
Why Apple Vision Pro marks the beginning of a new era for medicine
Apple Vision Pro: Sales are below expectations, and many returns are due to headaches, discomfort, excessive weight, and a high launch price. Initial reactions to the Vision Pro‘s arrival were poor, an…
Explainer video: what is Volt Typhoon
In the ever-evolving landscape of cybersecurity threats, one name has emerged as a harbinger of potential chaos: Volt Typhoon. This sophisticated cyber operation, backed by the Chinese state, has been silently…
China: goodbye WhatsApp, Threads, Signal and Telegram
Why Tim Cook cannot abandon the Asian giant WhatsApp, Threads, Signal and Telegram: China orders, and Apple delivers. It’s not the first time and probably won’t be the last given,…
What vulnerabilities are hidden from your cloud environment?
Cloud environment: The migration to cloud computing has revolutionized the way organizations operate, offering scalability, flexibility, and cost-efficiency. However, as we’ve ventured deeper into this digital transformation, the complexities and…
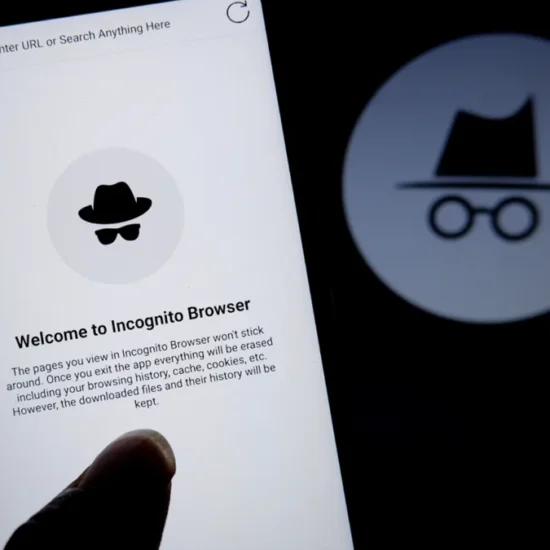
What happens when you use Incognito mode?
The digital age has blessed us with the convenience of accessing a world of information with just a few clicks. However, this accessibility comes with a price – our privacy.…
How to avoid privacy issues of ChatGPT
As artificial intelligence continues transforming how we interact with machines, tools like OpenAI’s ChatGPT, powered by the GPT-4 architecture, have emerged as pivotal in reshaping human-computer dynamics. These advancements, while…
Google’s new privacy feature in Chrome: good or bad?
Google has added a new feature to Chrome called IP Protection. This feature is supposed to make it harder for others to see your IP address, a unique number that can…
Big tech companies are not respecting new EU competition rules
24 companies have urged the European Commission and the European Parliament to exert all possible efforts to ensure that the gatekeepers adhere to both the literal requirements and the underlying…
Smartphone mirroring: how hackers use it to their benefit
With the rising popularity of smartphones, people are increasingly relying on them to access and share personal information. However, this growing dependency also makes us vulnerable to various security threats, such…