What did we do to deserve the Web Summit?
Reflecting on my few days in Lisbon at this year’s Web Summit you’ve got to think we did something pretty good to deserve such a technology treat. Whether it was…
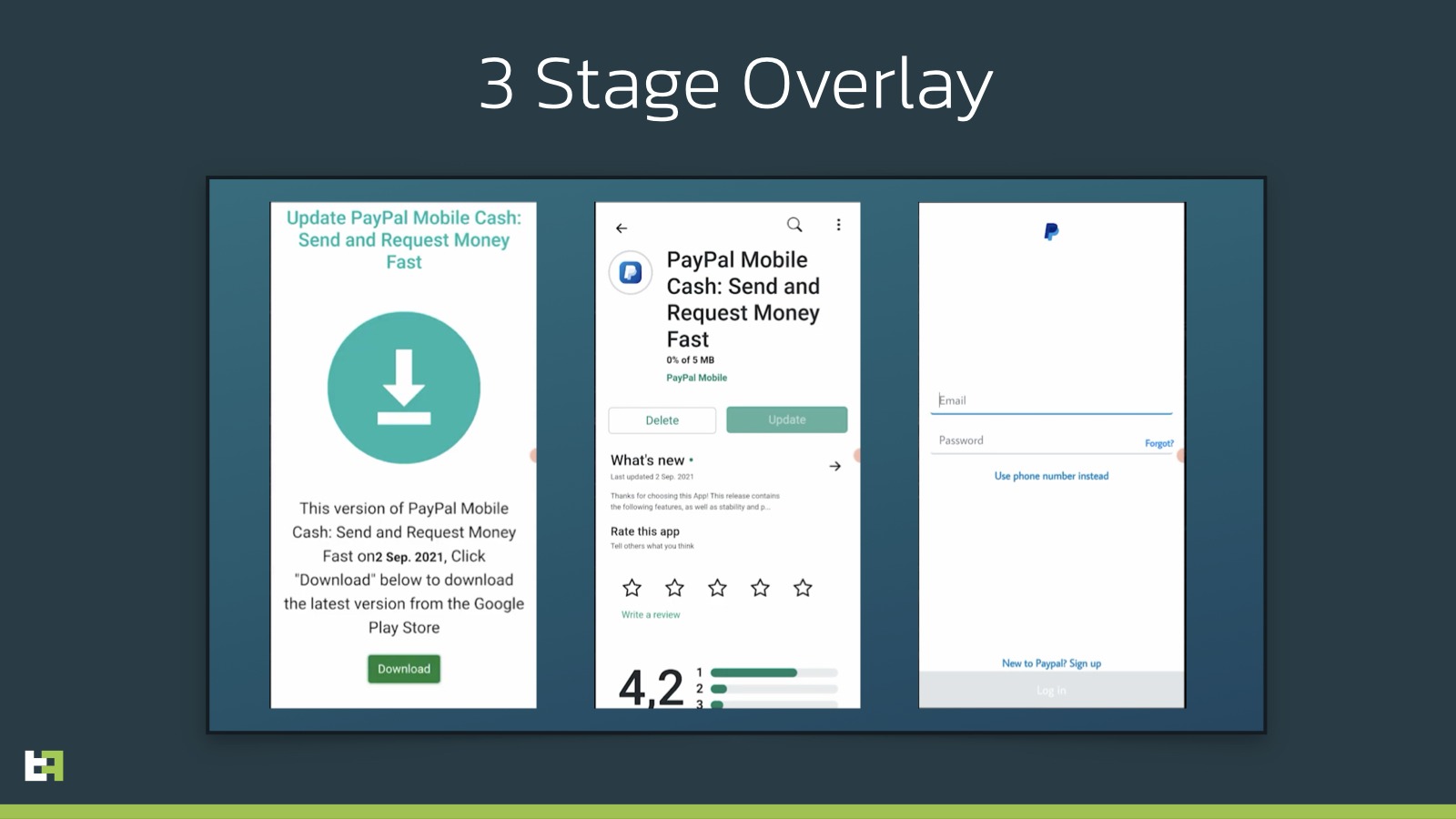
SOVA: A new Android Trojan that steals bank codes
An advanced Android Banking Trojan under active development A new sophisticated Android bank trojan, called SOVA, has been detected causing great concerns to users and companies. Although the malware is…
Blockchain, smart contracts, and gains for sustainability
Smart contracts are computer programs running on a blockchain that execute when certain conditions are met. Generally, they are used in agreements between two or more parties, allowing for transparent…
Tekntrash – knowing your customers with the help of AI
Companies depend on sales data to know consumer patterns when in fact they could obtain valuable data post-sales as well with the help of AI while at the same time…
LinkedIn data breach: A second colossal attack affected millions of users!
A recent data breach, back in June exposed 700 million users’ profiles causing great concern The allegations that data for millions of LinkedIn users have been leaked and made available…
Exit velocity: understanding Sweden’s tech success
Despite having a population of only 10 million, Sweden is already a global tech powerhouse. Last year, Stockholm displaced Berlin for the number three spot in the European rankings of…
Psychology of Programming
In recent years, it is generally accepted that teaching and learning of programming is generally characterized by certain “difficulties”, which manifest themselves mainly in the construction of an algorithm or…
Breathable Cities – the Smog Free Tower
The Smog Free Project is about the dream of clean air Cities versus our health? Who wouldn’t want to live in cities where the price we pay for our comfort…
Digital decarbonisation: sustainability in data centres
The amount of data we produce as a society is growing exponentially. Social media, video streaming, stockpiled images — together these phenomena result in huge quantities of information every day.…
Identity and Zero Trust
History of the zero-trust concept. Τhe concepts supporting zero trust are not new. First approach for the perimeter to an organisation’s IT systems was highlighted by the Jericho Forum in…