In an increasingly complex threat landscape, sophisticated mobile-targeted phishing campaigns continue to evolve, leveraging multiple redirection techniques and platform-specific behaviors to evade detection. Spear phishing, a highly targeted form of social engineering, is a preferred attack vector against corporate executives, specifically designed to compromise high-value credentials that grant access to sensitive enterprise data and systems.
Over the past few months, enterprises have observed a pattern of sophisticated spear phishing attempts targeting their executives, with some specifically targeting their mobile devices. These attacks demonstrate social engineering sophistication with threat actors impersonating trusted business platforms and internal communications and leveraging the features of a mobile device to improve the effectiveness of the attacks. Most recently, zLabs researchers analyzed a targeted campaign that leveraged a DocuSign impersonation scheme attempting to harvest corporate credentials from company executives.
The analysis of this campaign revealed an interesting attack chain incorporating advanced evasion techniques, mobile-specific targeted phishing links inside PDF files, and sophisticated infrastructure designed to circumvent traditional security controls while maintaining a convincing corporate appearance. This level of sophistication illustrates the evolving nature of targeted corporate mishing and the importance of robust, adaptive security measures in protecting sensitive enterprise assets.
Attack Analysis
The attack chain began with a well-crafted email targeted to executives, demonstrating the attackers’ prior reconnaissance and understanding of the target’s organizational structure.
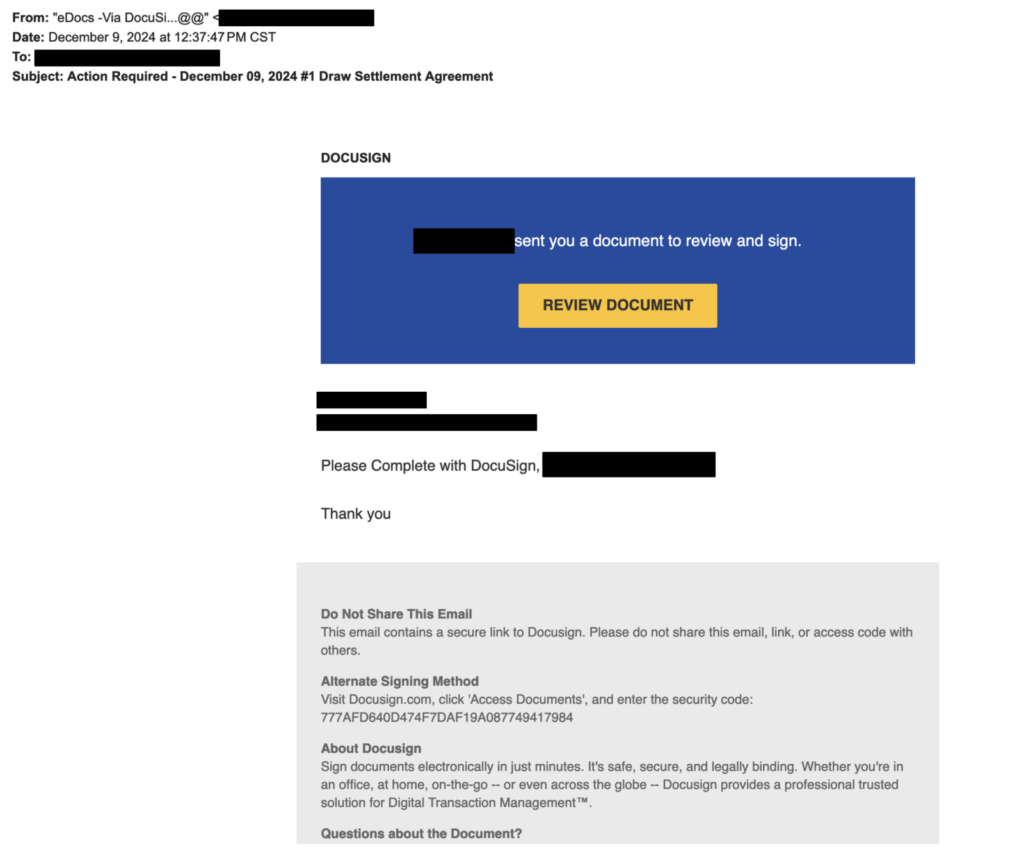
The initial payload was disguised as a DocuSign document requiring immediate review – a common yet effective social engineering tactic that exploits both urgency and authority. It’s worth mentioning that companies extensively use this platform to sign documents, which makes it a perfect delivery mechanism.
The technical analysis revealed a multi-stage attack infrastructure:
Initial Delivery: The phishing link was distributed via a legitimate domain, clickme[.]thryv[.]com, a sales and marketing platform service used to obscure the attacks’s origin.
Redirection: The link redirected to a high-reputation domain – a compromised university website, <REDACTED>…college[.]gov[.]bd – leveraging the institution’s credibility to evade detection.
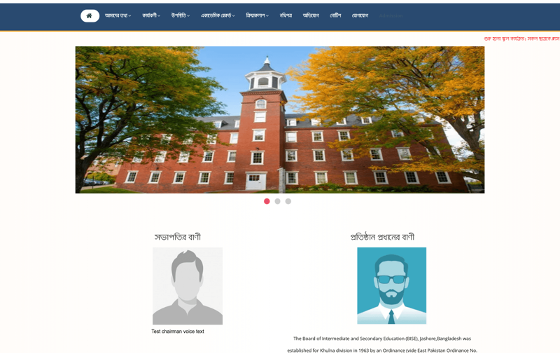
When analyzing detailed information about the compromised domain, our research team found a creation record dated “1999-05-20 00:00:00“, and owned by “Ministry of Posts, Telecommunications and Information Technology, Government of the People’s Republic of Bangladesh”. This can be used to easily evade detection systems based on reputation or in domain creation date to qualify a site as risky or legit.
Advanced Evasion (Multiple redirects): Attackers implemented CAPTCHA verification to bypass automated detection systems (e.g. bots).
Mobile-Specific Targeting (Mishing): Attackers used device fingerprinting to deliver tailored attack paths for mobile users, a tactic that is increasingly prevalent in modern phishing campaigns targeted to mobile device users. If the phishing link is accessed via a desktop, then the attack is abandoned:
On desktops or laptops, users were redirected to legitimate Google sites, for example, “support.google.com”, “mail.google.com”, “drive.google.com”, etc.
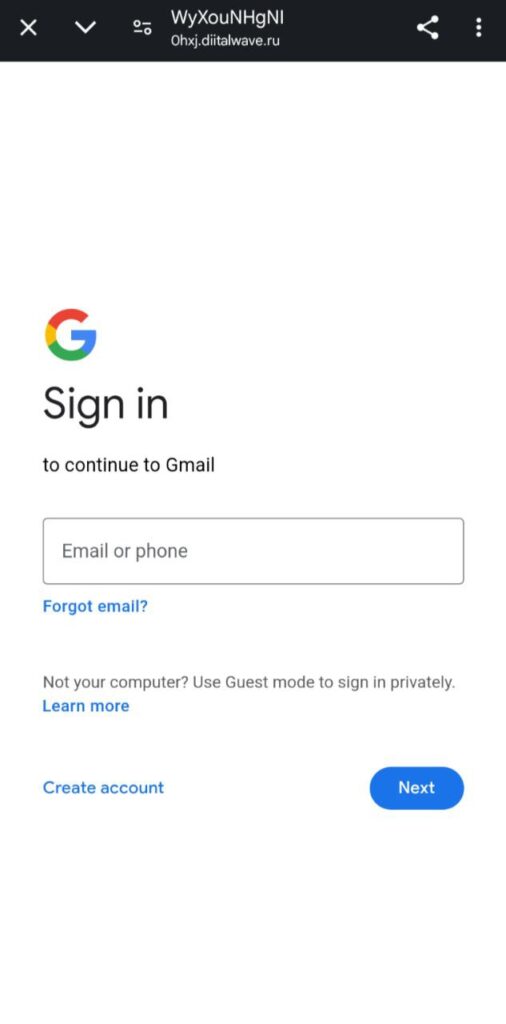
On mobile devices, however, additional redirections were leveraged to identify the platform. If the link was accessed via a mobile device, a cloned Google sign-in page designed to steal credentials was presented to the mobile user.
The following diagram shows the complete redirection chain of the attack, when accessed via mobile or desktop platforms:

Infrastructure Analysis
The domain used to host the final phishing site, diitalwave[.]ru is very recent, created on “2024-12-05 17:57:48”. The SSL certificate, issued to diitalwave[.]ru on “December 6, 2024 at 1:50:52PM”. The phishing attack was received on December 9, 2024. This information shows infrastructure created very recently relative to its usage for a targeted attack.
The IP hosting the site, “104.21.71[.]155”, CIDR “104.21.0[.]0/17”, belongs to Cloudflare infrastructure. Cloudflare is a well-known content delivery network (CDN) that offers features like DDoS protection, SSL encryption, and fast content delivery. When attackers abuse this infrastructure, they exploit its strengths for malicious purposes.
Our research identified phishing activity originating from the same IP address, with the earliest record traced back to mid-May 2024. Analysis revealed that this IP was associated with phishing campaigns targeting well-known brands such as USPS and WhatsApp. The domains linked to this IP in our records include:
wplusoriginal[.]com
oecoress[.]click
arrcom[.]top
o2-prepay[.]com
uspzlc[.]top
usuali[.]shop
Alternative Attack Vectors
While email-embedded phishing links remain prevalent, threat actors are increasingly diversifying their delivery mechanisms. PDF-based phishing represents an evolution in social engineering tactics, particularly effective against legacy security controls that lack deep file inspection capabilities. In this campaign targeting our executive leadership, we identified PDF-based attack vectors running parallel to the email-based campaign.
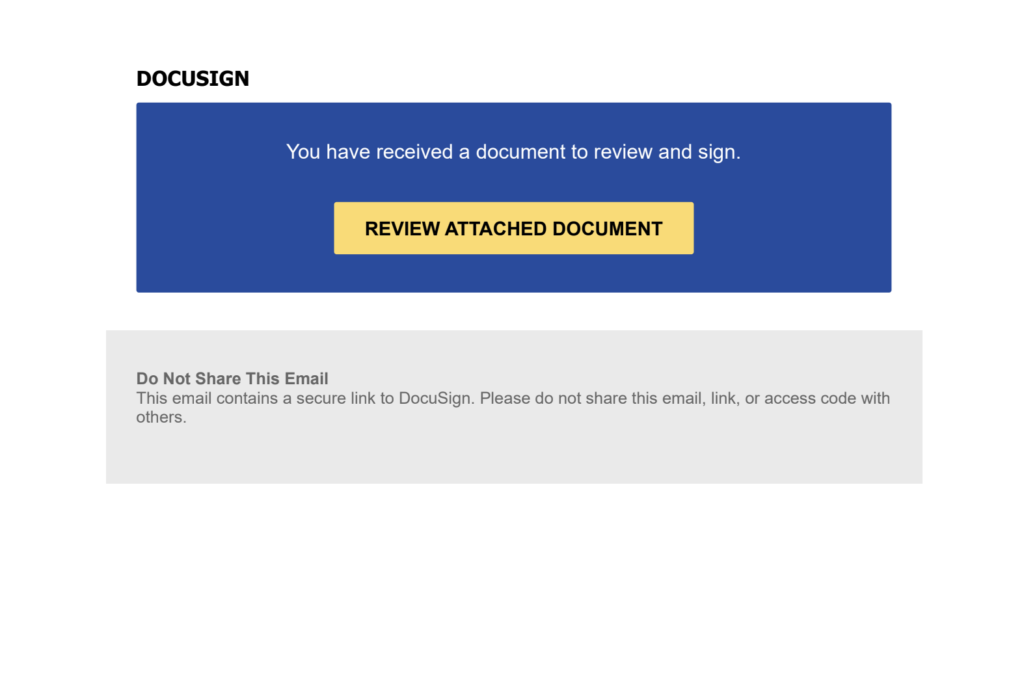
Our analysis revealed carefully crafted PDF documents designed to mimic legitimate DocuSign workflows, containing embedded phishing URLs. This technique exploits several technical advantages:
Deep link concealment within document structure
Bypass of traditional URL scanning mechanisms
Exploitation of user trust in PDF business documents
Potential evasion of email security controls
The identified phishing URL (https[://]elckg[.]kidsavancados[.]com/) was offline during analysis – consistent with the rapid infrastructure rotation typically observed in phishing campaigns. This ephemeral nature of phishing infrastructure, combined with PDF-based delivery, creates significant challenges for traditional detection mechanisms.
Strategic Implications
This incident underscores several critical points about modern phishing campaigns:
Attackers are increasingly investing in sophisticated infrastructure to bypass security controls.
Attackers know that mobile devices are largely unsecured so they have adopted a mobile-first attack strategy as demonstrated in this spearphishing example.
Mobile devices represent a distinct attack surface requiring specialized protection.
Compromised legitimate domains continue to play a crucial role in lending credibility to attacks.
Proven Protection
Zimperium’s comprehensive zero-day anti-phishing capabilities is evident in its ability to detect and neutralize a recent spearphishing campaign. In this sophisticated phishing attack, we see how MTD’s advanced detection capabilities successfully identified and blocked the entire threat chain before any credentials were compromised, underscoring the vital role of mobile-aware phishing protection in safeguarding sensitive data.
Attackers are continuing to rapidly evolve their tactics and techniques to circumvent traditional phishing detection techniques, especially when it comes to mobile-specific phishing campaigns, also known as Mishing attacks. Traditional anti-phishing and mobile threat defense solutions lack the advanced, on-device capabilities to detect these evolving, zero-day campaigns. Zimpeirum’s MTD solution provides enterprises and device users the most comprehensive set of detection options to detect and mitigate phishing threats, including:
Phishing links in SMS messages
Platform-specific browser extensions to detect phishing links real-time
Local, device-wide network-based filtering options
Ad-hoc, user-initiated phishing lookup
Phishing & malicious links embedded in files
Supported for both Managed, and/or BYOD devices
The real power, though, comes from Zimperium’s on-device, dynamic detection engine. Zimperium’s Mobile Threat Defense (MTD) solution delivers comprehensive, zero-day protection against phishing campaigns. By utilizing on-device artificial intelligence (AI), MTD detects and blocks malicious URLs, applications, and network traffic designed to target and exploit mobile users and their most sensitive information. With the use of advanced, mobile-specific machine learning classifiers running on-device that are continuously trained and updated via over-the-air updates, Zimperium is able to identify and mitigate new and evolving mishing tactics before they can compromise users’ mobile devices. As attack techniques continue to evolve, maintaining current and comprehensive mishing protection should be a cornerstone of any organization’s security strategy.
Source: Zimperium



