Rooting and jailbreaking, once widespread for enabling deeper customization and removing OS limitations on mobile devices, are increasingly becoming primarily the domain of power users, as manufacturers have made significant strides to reduce this practice from two different approaches. First, by adding more customization options so users feel less restrained. Second, by introducing tighter security protocols into stock Android and iOS versions. Despite a reduction in the number of rooted and jailbroken devices overall, they still represent a very serious security threat, not just to the user, but to enterprises who enable employees to access sensitive corporate apps and data from their devices. Our data shows that rooted devices are more than 3.5 times more likely to be targeted by mobile malware. Vulnerabilities and exploits related to these higher risk devices could represent the compromise of an entire organization; either accidentally or deliberately, as a stepping stone for a highly organized infiltration attack.
In this blog post, we’ll dive into the following key points about rooting/jailbreaking:
Why is this practice a significant threat for enterprises
How dynamic this matter is and why keeping up at this game is of paramount importance
How Zimperium’s unique technology allows for instant detection of these tools (and new ones) ensuring our customers stay secure
Is rooting still a threat?
What is Rooting?
Rooting is the process of gaining privileged access (or root access) to the Android operating system; analogous to superuser permissions in Linux or macOS. This allows users to modify system files, install specialized apps, and/or remove carrier/manufacturer restrictions; actions that would typically be off-limits in standard Android environments. Moreover, an advanced user can leverage a rooted device to reverse engineer installed applications.
Rooting vs Jailbreaking
While similar in principle, rooting and jailbreaking target different operating systems and functionalities. Rooting is typically an Android-specific procedure that focuses on gaining root access to allow deep system modifications. Jailbreaking, on the other hand, applies to iOS devices and encompasses broader objectives like bypassing Apple’s locked bootloader, enabling sideloading of non-approved apps and gaining administrative access. Although both allow elevated permissions, Android users have native support for sideloading apps while iOS users don’t.
As we’ll see next, rooted devices present hazardous usage patterns much more frequently than stock devices, so having these devices onboard isn’t cost free.
Some insights from our data…
Our analysis shows that rooted devices represent 0.1% of our total customer device base (figure 1).

Breaking this down by platform:
Android: 1 in 400 devices (0.25%) is rooted
iOS: 1 in 2,500 devices (0.04%) is jailbroken
Although there seems to be a particular emphasis on the United States and Malaysia, our data suggests that these devices can be found everywhere. Figure 2 gives a picture of how widely-spread rooted devices are all over the globe.
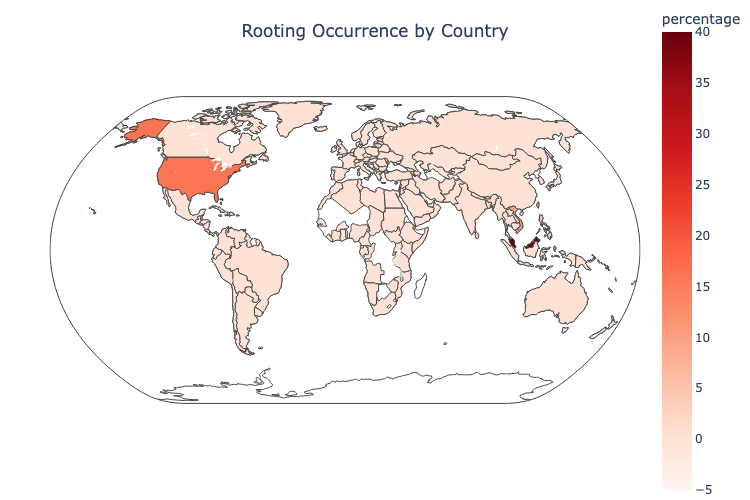
Figure 3 shows a comparison between the threats reported by stock and rooted devices over a 1-year period. This exhibits, at a broad level, the proportion by which the latter are more exposed to risk.
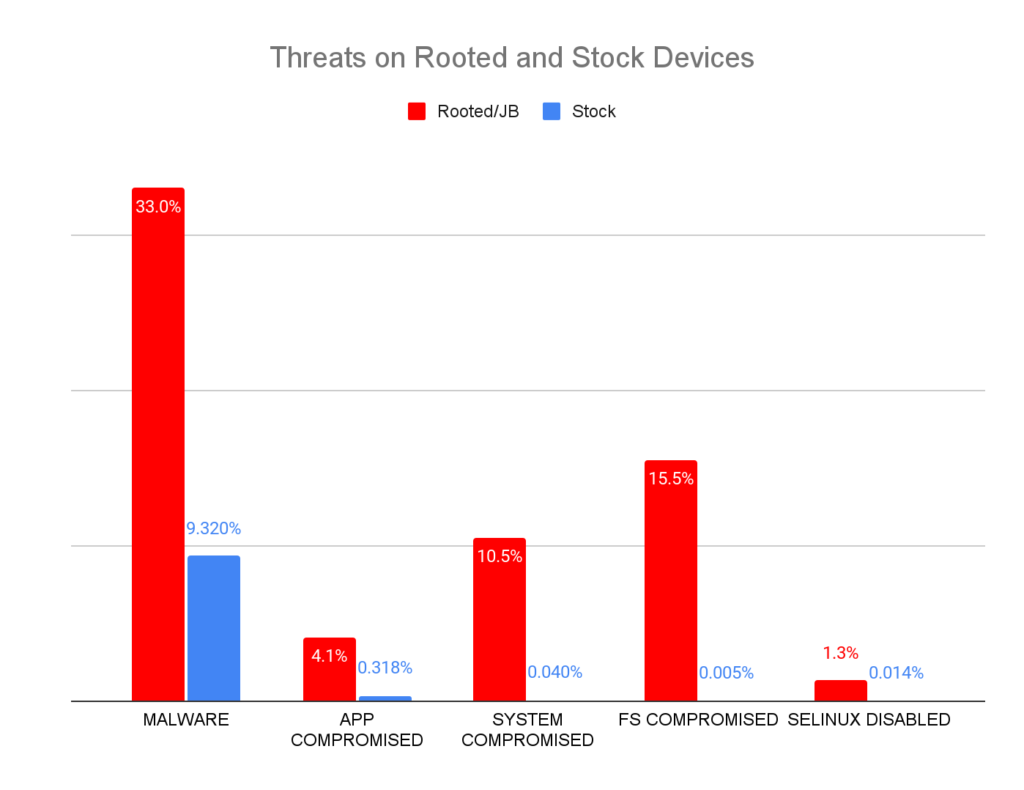
According to our data, the exposure factor of rooted devices versus stock devices varies from 3x to ~3000x, which suggests that rooted devices are potentially much more vulnerable to threats than stock devices. In other words, much riskier. In particular:
Malware attacks occur 3.5 times more frequently.
Compromised app detections surge by a factor of 12.
System compromise incidents are 250 times higher.
Filesystem compromise events increase by a factor of 3000.
Events where Security-Enhanced Linux is disabled increase more than 90 times.
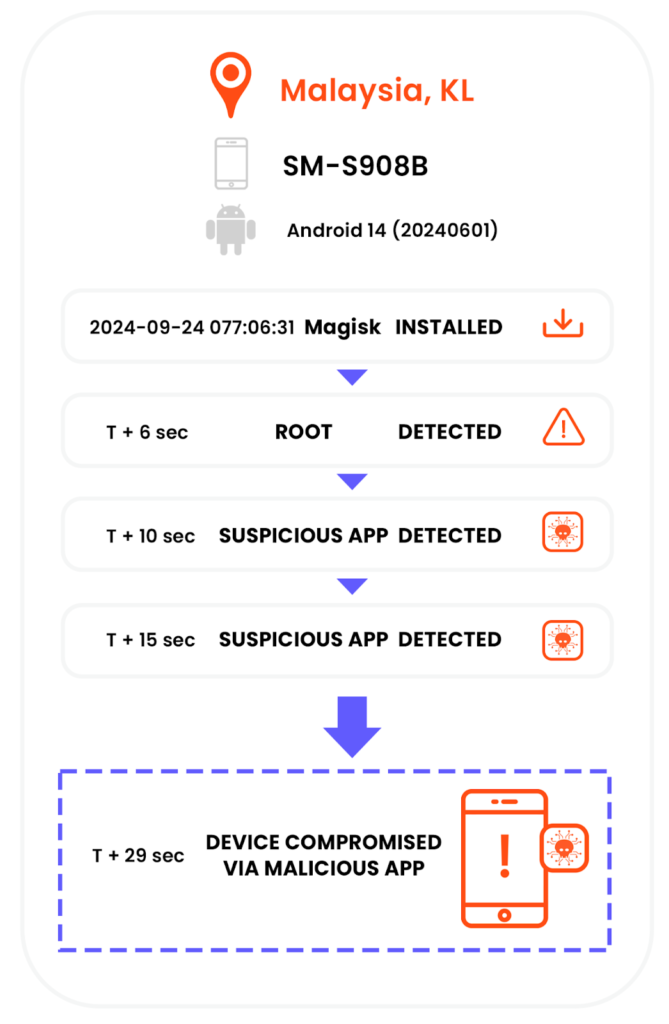
These findings demonstrate the severe security risks of using rooted or jailbroken devices in enterprise environments. Figure 4 illustrates this idea, showing a case of a rooted device that ended with a full compromise after sideloading malicious applications.
The Rooting Toolkit Guide To The Galaxy
Rooting toolkits continue to evolve, providing users with powerful frameworks to gain elevated control over their devices. In this section, we will explore some of the most prominent rooting tools observed in the wild and examine the key factors that contribute to their widespread use.
Android
Magisk
Magisk is one of the most popular rooting tools for Android, known for its “systemless” rooting method, which means it doesn’t modify the actual system partition but creates changes in a way that’s more concealed from apps and the OS. Latest versions of this tool allow users to gain root access without affecting OTA (over-the-air) updates and retain compatibility with apps that use Play Integrity, Google’s security check for rooted devices. Its popularity stems from its Magisk Modules, which offer various customization options and its ability to mask root status from apps that typically block rooted devices. One of the most popular modules for Magisk is Zygisk (its Zygote injection framework) which enables powerful runtime modifications. Its exploitation technique primarily relies on boot image manipulation and custom init scripts.
APatch
APatch distinguishes itself by using kernel hot-patching techniques that don’t require boot image modification, making it more stealthy than traditional rooting methods. Its exploitation approach focuses on runtime kernel memory modifications, allowing for dynamic system modifications without permanent changes. Users particularly appreciate its ability to maintain device firmware integrity while still providing root access, and its compatibility with Zygisk modules makes it an attractive alternative to Magisk for users seeking a more kernel-level approach.
KernelSU
This tool is focused on Android kernels, providing root access by modifying the Linux kernel layer rather than the user or system partitions. By integrating root functions directly into the kernel, KernelSU can provide more stable performance and potentially enhanced security for advanced users who are comfortable managing kernel configurations. It’s favored for its advanced customization potential and is particularly popular among developers and users interested in deep-level device modifications.
iOS
Dopamine
Dopamine gained popularity through its modern approach to jailbreaking, utilizing a CoreTrust bypass and implementing a rootless design that maintains much of iOS’s native security architecture. Its exploitation chain combines kernel exploits with careful Page Protection Layer bypasses, making it more stable than previous jailbreaks. Users favor it for its balance of stability and functionality, particularly on newer devices, while maintaining important security features of iOS.
Checkra1n
Checkra1n is a semi-tethered jailbreak tool designed over a hardware-based exploit called “checkm8” (CVE-2019-8900). This exploit targets vulnerabilities in Apple’s bootrom, making it effective for older Apple devices (primarily those up to the iPhone X) that are permanently vulnerable. Checkra1n’s popularity comes from its reliability and longevity since Apple cannot patch the bootrom exploit via software updates, making it a valuable tool for persistent jailbreaking on compatible devices.
Roothide
Roothide (now known as Rootify) focuses on stealth and stability through its KFD (Kernel File Descriptor) exploit-based approach. Its exploitation technique centers on sophisticated kernel memory manipulation and process hiding, making it particularly effective at evading detection. The tool’s popularity stems from its reliability on newer iOS versions and devices, combined with its emphasis on maintaining system stability while providing comprehensive jailbreak features. Users particularly appreciate its focus on preserving device functionality while maintaining the jailbreak.
Table 1 (below) gives a comprehensive summary of the most frequently used rooting tools in the industry. It is worth mentioning that most of these frameworks offer add-ons or modules to implement their detection evasion mechanisms.

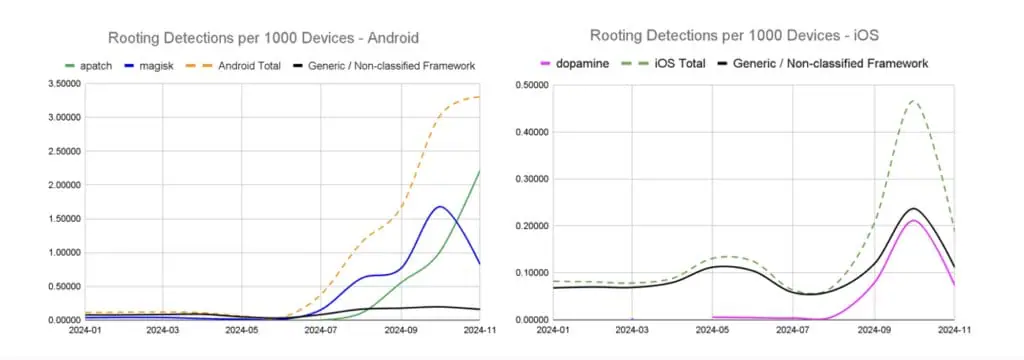
Figure 5 splits out our data between Android and iOS users. It can be seen that for some rooting tools (Apatch, Magisk, Dopamine) there’s been a ramp up in detections in recent months., This upward trend underscores the importance of closely monitoring these evolving threats.
The Cat and Mouse Game
Rooting tools have been around for quite some time now. Since Android first came out in 2008, a rooting community was born with the sole objective of giving the end user more control over their device. Many rooting frameworks became available from that time until2016, when manufacturers and security vendors started striving to detect the presence of these types of tools. That’s where Magisk comes into play, and quickly becomes a sensation with its “systemless root”, allowing users to modify their devices without changing the system partition. This approach allowed root to persist even after system updates while avoiding security checks like Android’s Play Integrity. This shift in strategy marked a turning point, as rooting was no longer just about gaining elevated privileges—it became a battle of stealth, where tools like Magisk had to evolve to remain undetected while maintaining persistent control over the device.
Riding the Wave: The Ever-Evolving Ecosystem of Modern Rooting Frameworks
As seen next, the innovation landscape for rooting technologies is quite vast and dynamic. Lots of contributors around the world chip in constantly, providing new ideas and algorithms to improve the rooting mechanisms.

Figure 6 tracks the number of new forks created over time for several of the major rooting and jailbreak frameworks. The data reveals interesting development patterns in the community. Magisk shows consistent developer interest with a steady baseline of new forks (150-300 monthly), indicating ongoing community engagement. More revealing are the sharp spikes in activity: KernelSU experienced a surge of nearly 500 new forks in mid-2023, while Roothide saw two significant waves of developer interest, peaking at around 400 new forks in early 2024 (coinciding with Roothide’s initial public release as a promising root solution for iOS 16 and 17) and an even larger spike of nearly 600 new forks in late 2024. These sudden increases in forking activity often coincide with major framework updates or with increased security measures in Android/iOS, demonstrating how quickly the development community mobilizes to maintain and adapt these tools. Meanwhile, frameworks like APatch, Dopamine, and Palera1n maintain lower but persistent levels of new development activity, typically generating under 100 new forks per month.
The dynamic nature of rooting tools, evidenced by the intense development activity shown in Figure 6, adds another layer of complexity to the detection challenge. Each spike in development activity, potentially represents new evasion techniques and countermeasures being developed.
Beyond Detection: Fingerprinting Rooting Tools
While identifying rooted or jailbroken devices presents a significant technical challenge, the Zimperium security framework goes a step further by pinpointing the specific rooting tool in use. This is particularly challenging as concealment is a core feature of these tools —they are specifically engineered to evade detection.
As we see in figures 7 and 8, the development lifecycle of these tools is highly dynamic and rapidly evolving so this never-ending pursuit is constantly being played between security vendors’ development teams and the end-users’ development community. New frameworks come and go while others adapt to stay in the game. As detection technologies improve, so do the hiding mechanisms of these tools. Development teams for these frameworks are highly collaborative, with many contributors from all over the world putting their grain of salt to come up with the most innovative and out-of-the box solutions. Some of the development communities behind these frameworks push many minor releases per month and major releases no more than a few months apart.

Despite this cat-and-mouse game, our analysis has successfully mapped the footprints of various tools across our user base, enabling us to identify not just the modified devices, but also the specific methods used to achieve root access.
Summary
Rooting and jailbreaking remain a serious threat to enterprise security. These practices grant users privileged access to their device’s operating system, opening the door to a host of security risks—including malware infections, compromised apps, and full system takeovers. A single compromised device can serve as the entry point for a much larger attack, putting an entire organization at risk.
What makes this challenge even more pressing is the ever-evolving nature of rooting tools. This isn’t a static threat; tools like Magisk, APatch, KernelSU, Dopamine, Checkra1n, and Roothide are in constant development, with new versions and techniques emerging regularly to bypass security measures. Keeping up with these changes is critical, and that’s exactly where Zimperium’s zLabs team excels. Our experts continuously monitor these tools, analyze new releases, and adapt detection methods to ensure enterprises stay ahead in this ongoing battle.
Zimperium’s on-device, dynamic detection engine is purpose-built to combat these threats in real time. Unlike conventional security solutions, our technology doesn’t just detect rooted devices—it also identifies associated tampering events, leveraging advanced machine learning, AI, and behavioral analysis to fingerprint these tools and track their evolution. This level of detail is crucial, as these tools are designed to evade detection. By combining deep intelligence with real-time, on-device threat detection, Zimperium provides enterprises with unmatched visibility and protection against these sophisticated attacks.
The game is always changing, but Zimperium is committed to staying ahead. Our continuous monitoring, cutting-edge detection capabilities, and proactive security measures ensure that enterprises can detect, respond to, and mitigate the impact of these threats—before they escalate into full-scale breaches. In an environment where security risks are constantly evolving, Zimperium delivers the visibility and protection organizations need to stay secure.
As a cutting-edge mobile security leader, Zimperium has been a major character in this chase; evolving with technologies to keep up with this industry’s demanding pace. New technologies are being developed within our Labs on a continuous basis in order to protect our customers from this and many other types of threats and give them visibility over what, for most users, is transparent. These ever-evolving technologies allow us to stay in the game, ahead of the competition and advanced persistent threats (APTs) by achieving high profile intelligence and granularity at detecting and analyzing threats and their impacts. From simple (yet powerful) data analytics to the most advanced automated behavior patterns detection mechanisms, we at Zimperium got you covered so none of these threats goes unnoticed.
[1] This data period goes from October, 2023 till October 2024. The plotted magnitudes correspond to threats per device (rooted or stock, respectively).
[2] This CVE appears as reserved at the time of writing this article. An associated post with an overview and some specifics can be found here.
[3] Android’s Play Integrity: a set of services and APIs that help protect apps against security threats, including device tampering, bad URLs, potentially harmful apps, and fake users (https://developer.android.com/google/play/integrity/overview)
SOURCE: ZIMPERIUM



