Red and Blue team combined – an explanation of red and blue cyber simulations
When we are talking about the professions and methodologies division in cyber security, we are grasping a vast area of operation filled with specifics in professions, specialities and work methodologies. The very interesting thing is that most often, all these divisions are portrayed with colours to give a more interesting and clear approach to each one. We have mentioned white hat and black hat hackers/ or security engineers (link here), and we have seen other colours mentioned, such as red, blue and purple. But what do red, blue or even purple mean in the cyber security world?
Every organization should have a cybersecurity department that ensures the business’s assets are safe from attacks and data breaches. This security department is mainly made up of two teams: the red team and the blue team. These teams are equally important and work hand-in-hand to ensure the company’s security. So, what do the red team and blue team do? And how are they different from each other?
Cybersecurity is a set of techniques used to protect people, data, and their assets from attacks, breaches, and unauthorized access to the internet. It is a vast concept and is divided into many fields. Therefore, having different categories and teams is crucial in operating according to security standards and enhancing the best security protection methods. That’s why we have red and blue teams that help ensure that the best practices and security measures are being implemented in different information systems. Most of these teams exist in an organization’s security department and work hand-in-hand to ensure that the business is secure and safe from threats.
Our previous article explained what the teams do specifically and their differences. But, the concept of red and blue teams is similar to the one in an army, where the red team is the offensive approach or team, and the blue team is the defensive team.
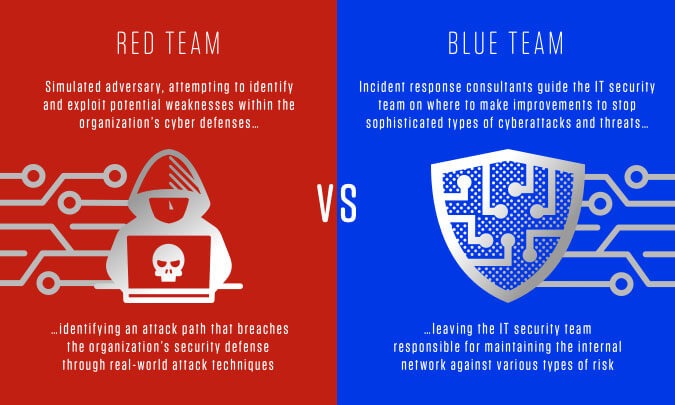
Red team and blue team simulation
As I mentioned above, looking closely at these colour-specific teams’ approaches is very similar to a military training exercise. We have an offensive team (the red one) and a defensive part (the blue one). In a military training drill, both teams are facing each other at ‘war’: a red team that uses real-world adversary tradecraft in an attempt to compromise the environment, and a blue team that consists of incident responders who work within the security unit to identify, assess and respond to the intrusion. Both parties play a very important role in protecting and defending the organizations by pointing out the vulnerabilities they may have and the solutions for each one. In a cyber security testing or simulation, the red team acts as an adversary, trying to exploit potential vulnerabilities by using advanced attacking techniques.
The penetration testers that are part of the offensive (red) team use the latest ethical hacking and real-world attack techniques to bypass different system layers to the point where they have compromised the system. The red team gains initial access, usually through the theft of user credentials or social engineering techniques. Once inside the network, the red team elevates its privileges and moves laterally across systems with the goal of progressing as deeply as possible into the network, exfiltrating data while avoiding detection. This approach tests a system’s performance and its incident response since all the attacks are made from a real-world hacker point of view.

Examples of red team activities include:
Penetration testing in which a red team member attempts to access the system using a variety of real-world techniques
Social engineering tactics, which aim to manipulate employees or other network members into sharing, disclosing or creating network credentials
Intercepting communication to gain more information about the environment etc.
If the red team plays offence, the blue team is on defence. The blue team in cybersecurity is a group of experts who defend and protect a business’s security from cyberattacks. They constantly analyze an organization’s security standing and implement measures to improve its defences. They perform threat intelligence, incident management, and security automation tasks to ensure no risks or vulnerabilities. One key metric is the organization’s “breakout time” — the critical window between when an intruder compromises the first machine and when they can move laterally to other systems on the network. After the analytic security auditing and testing, the blue team offers protection measures according to the best security standards based on the organization’s situation.
Examples of blue team exercises include:
Performing DNS research
Conducting digital analysis to create a baseline of network activity and more easily spot unusual or suspicious activity
Reviewing, configuring and monitoring security software throughout the environment
Ensuring perimeter security methods, such as firewalls, antivirus and anti-malware software, are properly configured and up-to-date.
Employing least-privilege access means that the organization grants the lowest level of access possible to each user.

Benefits of the Red / Blue team
The red team and the blue team are equally important in every organization. They work together to secure and protect a company from threats and attacks. Therefore, these kinds of teams greatly help and offer many benefits to their organization regarding enhancing security standards and defensive techniques. Some of the benefits that the organization can get from these groups are:
Identifying and detecting vulnerabilities or security gaps in different information systems
Improving security mechanisms to detect targeted attacks and improve breakout time
Raising awareness among staff as to the risk of human vulnerabilities which may compromise the organization’s security
Creating a safer, low-risk environment by increasing the maturity of an organization’s security capabilities
All these and more are offered by the combination of the two teams with each other. And like that, creating the purple team is the ultimate step in the division of security approaches and teams.
When you mix Red and Blue, you get Purple
Just like in colours, if you mix blue and red, you get purple. The same principle goes with the security team divisions. If, in simpler terms, the purple team is created by fusing the two teams together. The purple teams share information and insights to improve the organization’s security. To ensure that red and blue teams operate in a spirit of collaboration, a purple group can be created (or hired) to analyze the process from a distance, foster communication, and help both sides work toward their shared objective. In conclusion, a purple team acts as a mediator and can provide insight from a more detached perspective. When all three elements work cohesively, organizations can gain a much clearer perspective on their readiness to deal with attacks.
So overall, the whole division into teams is a little piece of a great puzzle. When it is put together, it can give you a clearer picture of the whole cyber simulation, the proactive approach we should choose and post-attack procedures to follow in case of attacks.

