Without a doubt, our lives today have increasingly intertwined with technology. We rely on countless online services for everything from social media to online banking, and the need for a password comes with each of these services. Passwords are our first line of defence against hackers and cybercriminals, but what happens when our passwords are compromised? This is where password cracking comes in – a technique used by hackers and cybercriminals to gain unauthorized access to a user’s account. But how does password cracking work? Let’s find out.
Common password-cracking techniques
Password cracking is the process of deciphering or recovering a password from stored data or network transmission. Cybercriminals use various methods to crack passwords, each with its own level of sophistication and effectiveness. Understanding these techniques is crucial for both individuals and businesses looking to protect their digital assets.
A brute force attack is the most straightforward password-cracking technique. Hackers use software that systematically tries every possible combination of characters until the correct password is found. Although this method is time-consuming and resource-intensive, it is guaranteed to crack the password eventually. However, the growing use of long and complex passwords has made brute-force attacks less effective in recent years.
A dictionary attack involves guessing a password by running through a list of commonly used words, phrases, or patterns. Hackers often use large databases, known as “dictionary files,” containing millions of potential passwords. This method is more efficient than a brute force attack, as it leverages the fact that many users tend to use simple, easy-to-remember passwords. Dictionary attacks can be further refined by incorporating known details about the target, such as their name, birth date, or hobbies.
Rainbow tables are precomputed tables that contain the hash values of millions of possible passwords. A hash is a fixed-length string of characters generated from a password using a mathematical algorithm. Since computing the hash of a password is a one-way process, hackers cannot directly reverse-engineer the password from the hash. However, by comparing the target’s hash to the values in a rainbow table, an attacker can efficiently discover the original password. Rainbow tables are particularly useful for cracking passwords stored in hashed form, but their effectiveness can be mitigated through the use of unique “salts” for each password.

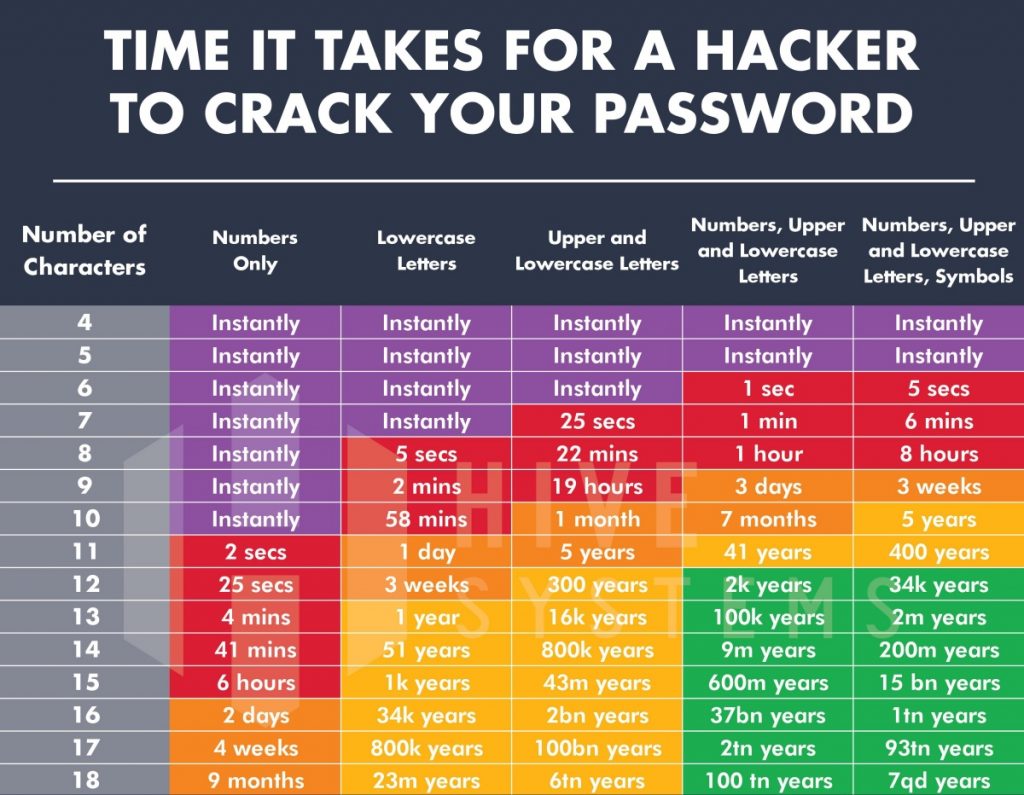
![2023 Password Table [Recovered]](https://4imag.com/wp-content/uploads/2023/05/source-Hive-Systems.jpeg)
Password hashing and encryption
To better protect passwords, many systems use a combination of hashing and encryption techniques. These methods add an additional layer of security, making it more challenging for hackers to crack passwords.
Hashing is the process of converting a password into a fixed-length string of characters using a mathematical algorithm. The resulting hash value is unique to the input password, meaning that even a minor change in the password will generate a completely different hash. Since hashing is a one-way process, it is virtually impossible to reverse-engineer the original password from the hash. This makes it an ideal method for securely storing and transmitting passwords.
Salting is a technique used in conjunction with hashing to enhance password security further. A salt is a random string of characters that is generated for each password and combined with the password before hashing. The resulting hash value is unique not only to the password but also to the salt. This means that even if two users have the same password, their hashes will differ due to the unique salts. Salting makes it more difficult for attackers to use precomputed tables like rainbow tables to crack passwords.
Encryption is the process of converting plaintext data, such as a password, into ciphertext, which someone with the appropriate decryption key can only read. Encryption is a reversible process, unlike hashing, so the original data can be recovered by decrypting the ciphertext. Encryption is often used to protect sensitive data during transmission, such as when logging into a website or emailing. By encrypting passwords, systems can ensure that even if a hacker intercepts the data, they will be unable to read the password without the decryption key.
Ethical Considerations in password cracking
While password-cracking techniques are often associated with malicious activities, there are legitimate uses for these methods in the realm of cybersecurity. Ethical hacking, also known as penetration testing or “white-hat” hacking, involves using the same techniques as cyber criminals to identify vulnerabilities in a system and recommend solutions to improve security.
Penetration testing is a proactive approach to cybersecurity, where a team of ethical hackers attempts to breach a system’s defences using password-cracking techniques, among other methods. By simulating real-world cyberattacks, penetration testers can identify weaknesses in an organization’s security policies, processes, and technologies. The results of these tests are then used to prioritize and implement necessary security improvements.
In some cases, password cracking can be used for legitimate password recovery purposes. For example, an individual may forget their password for an encrypted file, or an administrator may need to access a locked account. In these situations, password cracking techniques can be employed to recover the lost password, provided that the person attempting the recovery has the proper authorization.
Finally, security researchers often use password-cracking techniques to study the effectiveness of various password security measures. By analyzing the strengths and weaknesses of different hashing algorithms, encryption methods, and password policies, researchers can develop new strategies for protecting passwords and mitigating the risk of unauthorized access.
Tips for creating secure passwords
To protect your digital assets from password-cracking attempts, it is essential to use strong, unique passwords for each of your online accounts. Implement the following best practices when creating and managing your passwords:
Length and complexity
Longer passwords are generally more secure, as they increase the number of possible character combinations, making brute force attacks more time-consuming and resource-intensive. Aim for a minimum of 12 characters in length and include a mix of uppercase and lowercase letters, numbers, and special characters to create a complex password that is difficult to crack.
Avoid common words and patterns
Dictionary attacks rely on many users choosing simple, easy-to-remember passwords. Avoid using common words, phrases, or patterns, such as “password,” “123456,” or “qwerty.” Instead, opt for random combinations of characters or use a passphrase made up of multiple unrelated words.
Use unique passwords for each account
Reusing the same password across multiple accounts increases the risk of a single password breach leading to unauthorized access to all of your accounts. Always use unique passwords for each of your online accounts, and consider using a password manager to help you keep track of your passwords securely.
Two-factor authentication
Enable two-factor authentication (2FA) whenever possible. 2FA adds an extra layer of security by requiring a second form of verification, such as a fingerprint, a text message code, or an authenticator app, in addition to your password. This makes it more difficult for an attacker to gain unauthorized access to your account, even if they have cracked your password.
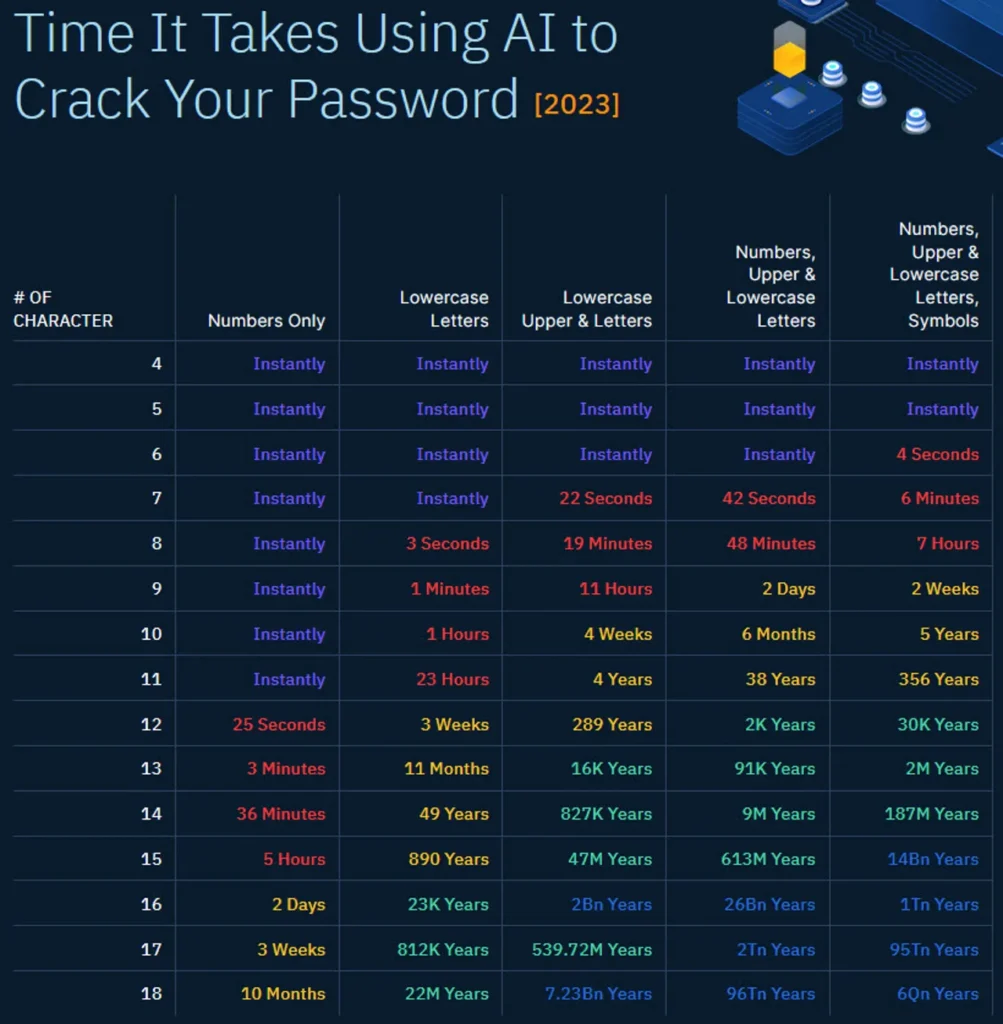

How businesses can protect against password cracking
Businesses face unique challenges when it comes to password security, as they must manage and protect the credentials of multiple users with varying levels of access to sensitive data. Implement the following strategies to help safeguard your organization against password-cracking attempts:
Implement strong password policies
Establish and enforce strict password policies that require employees to use long, complex passwords unique to each account. Provide guidelines on choosing secure passwords and regularly educating employees on password security’s importance.
Regularly monitor and update systems
Stay up to date on the latest security vulnerabilities and patches, and regularly update your organization’s systems and software. Routinely monitor your network for signs of intrusion and promptly investigate any suspicious activity.
Conduct regular penetration tests
Hire a team of ethical hackers to conduct regular penetration tests on your organization’s systems. This will help identify potential weaknesses in your security defences before cybercriminals can exploit them. By simulating real-world attacks, penetration testing can provide crucial insights into the effectiveness of your organization’s security measures.
Use multi-factor authentication
Enable multi-factor authentication (MFA) for all accounts that contain sensitive data. MFA requires users to provide additional verification forms, such as a fingerprint or a code sent to their phone, in addition to their password. This adds an extra layer of security that can help prevent unauthorized access, even if a password is compromised.
Use password managers
Encourage employees to use password managers to help them create and manage strong, unique passwords for each account. Password managers can also help ensure employees do not reuse passwords across multiple accounts, reducing the risk of a single password breach leading to a widespread security incident.
Password cracking is a serious threat to the security of our digital lives. Still, by understanding the techniques used by cybercriminals and implementing best practices for password creation and management, we can better protect ourselves and our organizations. By staying informed and proactive, we can help ensure that our digital assets remain secure for years to come.



